腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Just published a new blog post in the zero-to-TrustZone series: https://bits-please.blogspot.com/2016/06/trustzone-kernel-privilege-escalation.html Qualcomm TrustZone Kernel privilege escalation!
" 高通 TrustZone 内核提权漏洞的利用(CVE-2016-2431) ︰ https://t.co/rkCZOhcrwb "
-

[ Android ] McAfee Labs discovers app collusion threats, increasing growth in mobile malware http://zpr.io/Kvfm https://t.co/eUd53v8Qoc
" 一种称为 'APP 勾结' 的新威胁 - 两个 APP 勾结作案,一个负责收集信息,另一个负责外泄信息: https://t.co/P3SKoH0MDl Trustlook 也有一篇 Blog 谈这个问题: http://blog.trustlook.com/2016/06/15/hijacked-mobile-app-collision/ "
-

[ Android ] Dalvik bytecode from tampering Principle and Implementation: http://drops.wooyun.org/mobile/16677 (Chinese) https://github.com/leonnewton/selfmodify
" Dalvik 字节码自篡改原理及实现 ︰ https://t.co/MSWISRGmvH GitHub Repo: https://t.co/p6SpnxNYKy"
-

[ Attack ] xDedic - an "eBay" for hacked servers: https://securelist.com/blog/research/75027/xdedic-the-shady-world-of-hacked-servers-for-sale/
"xDedic - 专门交易被黑服务器的网站︰ https://t.co/WQs0Xhfj6p"
-

[ Attack ] IT threats during the 2016 Olympic Games in Brazil - Securelist http://ow.ly/V17G301gu7s
" 2016 巴西奥运会期间的网络威胁,来自 Kaspersky Blog: https://t.co/vE2U5WQG3B"
-

[ Attack ] Mofang : A politically motivated information stealing adversary : https://foxitsecurity.files.wordpress.com/2016/06/fox-it_mofang_threatreport_tlp-white.pdf (pdf)
" Mofang - 具有潜在政治动机的攻击组织(几乎确定来自中国),来自 Foxit 的分析报告︰ https://t.co/vQOVkkxxfC "
-

[ Attack ] Over 45 Million passwords from Verticalscope 1,000 sites leaked online http://securityaffairs.co/wordpress/48404/deep-web/verticalscope-data-breach.html
" Verticalscope 平台被黑,运行在平台上的 1,000 个网站受影响,泄漏了 4500 万份密码: https://t.co/TdNZwxQOvq"
-

[ Browser ] Chrome - GPU process BufferManager double-read https://bugs.chromium.org/p/project-zero/issues/detail?id=787#c_ts1465984996
" Chrome GPU 进程 BufferManager Double-Read 漏洞,来自 Project Zero Issue 787: https://t.co/XfcoAIPiGI"
-

[ Browser ] Safari will no longer reveal installed common plug-ins. No Flash, Java, Silverlight, QuickTime in navigator.plugins: https://webkit.org/blog/6589/next-steps-for-legacy-plug-ins/
" 默认情况下,Safari 10 将不再向网站提供某插件是否安装的信息,如 Flash、Java、Silverlight,来自 WebKit Blog : https://t.co/dJUFcTISsp"
-

[ Defend ] ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks : https://www.trust.informatik.tu-darmstadt.de/fileadmin/user_upload/Group_TRUST/PubsPDF/ropdefender.pdf (pdf)
"ROPdefender - 检测 ROP 的工具, Paper ︰ https://t.co/gYqfOBFnxf "
-

[ Hardware ] #Siemens SIMATIC S7-300 Denial-of-Service Vulnerability V3.2.12 Exploit causes device to go OOS reboot required https://ics-cert.us-cert.gov/advisories/ICSA-16-161-01 …
" 西门子 SIMATIC S7-300 拒绝服务漏洞,来自 US CERT: https://t.co/WUB4DE1Jhw..."
-

[ Hardware ] Intel x86s hide another CPU that can take over your machine (you can't audit it) http://boingboing.net/2016/06/15/intel-x86-processors-ship-with.html
" Intel x86 除了主 CPU 外,还隐藏着一个 CPU: https://t.co/P9yPmWJ6Vc"
-

[ iOS ] Liberation, a new iOS engine uses Keystone assembler inside for code injection! https://github.com/iOSCheaters/Liberation
" Liberation - iOS 代码注入引擎,基于 Keystone 汇编工具: https://t.co/spJbYYSkbh"
-

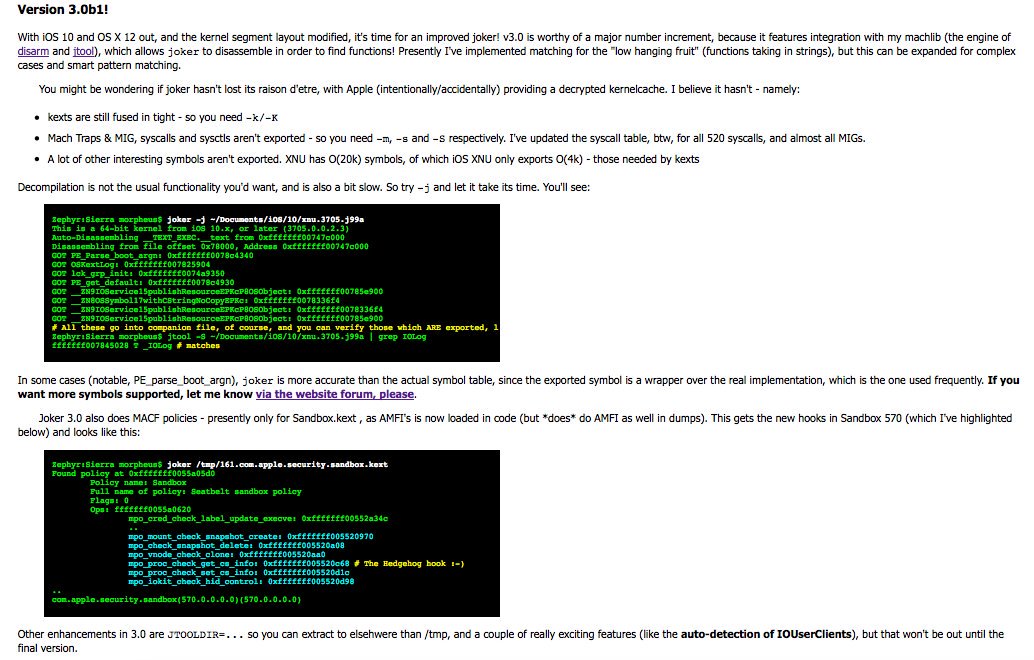
[ macOS ] Joker (#iOS10/#OSX 12 #kernel reversing aid) v3.0(β): now shows MACF hooks, syscalls, MIG. http://newosxbook.com/tools/joker.html#v3 https://t.co/WKDkscwhAT
" Joker - OS X Kernel Cache 处理工具(辅助逆向): https://t.co/AlYBBbvT4w https://t.co/WKDkscwhAT"
-

[ Malware ] Malware authors uses OLE embedding to deliver malicious files. #MMPC on ID and mitigation: http://ow.ly/p0od301gt5o https://t.co/Gx6f8H1SCw
"恶意软件作者正在通过内嵌 OLE 对象的方式传播恶意软件,来自微软 Blog: https://t.co/Or2SJfJyAb https://t.co/Gx6f8H1SCw"
-

[ Obfuscation ] Deobfuscator - all-in-one Java deobfuscator which will deobfuscate code obfuscated by most Android obfuscators https://github.com/java-deobfuscator/deobfuscator
" Java 反混淆工具: https://t.co/C3oCAyuNE2"
-

[ Others ] Technical Details on the DNC hack via powershell backdoor : https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
" 针对民主党委员会的入侵行动,来自 CrowdStrike Blog︰ https://t.co/YzXROv7Mu4"
-

[ Others ] Face Authentication Bypassing – KeyLemon http://goo.gl/fb/YdzjJm #FullDisclosure
" KeyLemon 人脸识别绕过漏洞,来自 FullDisclosure 公告: https://t.co/94hyRogLcw "
-

[ Others ] Password DNA: https://www.unix-ninja.com/p/Password_DNA
" Password DNA ︰ https://t.co/1ZH0osslM0"
-

[ Pentest ] Where My Admins At? (GPO Edition) : http://www.harmj0y.net/blog/redteaming/where-my-admins-at-gpo-edition/ cc @ harmj0y
" 通过组策略对象(GPO)关联的方法枚举管理员成员信息︰ https://t.co/w29wunOJWb "
-

[ Popular Software ] [CVE-2014-1520] NOT FIXED: privilege escalation via Mozilla's executable… http://goo.gl/fb/gWJ7FS #FullDisclosure
" Mozilla 可执行安装包文件劫持漏洞(CVE-2014-1520),来自 FullDisclosure 的公告: https://t.co/C9P5molCKY "
-

[ Popular Software ] Telegram calls claims of bug in messaging service bogus - https://threatpost.com/telegram-calls-claims-of-bug-in-messaging-service-bogus/118678/
" Telegram APP 存在漏洞,攻击者可以使设备 Crash: https://t.co/EWvLVuu4EN"
-

[ Popular Software ] [local] - AdobeUpdateService 3.6.0.248 - Unquoted Service Path Privilege Escalation https://www.exploit-db.com/exploits/39954/
" AdobeUpdateService 3.6.0.248 存在一个不带引号的服务路径搜索漏洞: https://t.co/7rDLzyVVVM"
-

[ Popular Software ] New post: Unsupported TeamViewer Versions Exploited For Backdoors, Keylogging http://bit.ly/239nP7P @ TrendMicro
" 前两周有报道称 TeamViewer 被黑导致用户被攻击,后来 TeamViewer 官方否认了这一说法。趋势科技这篇 Blog 提到,用户被黑是因为安装了内嵌木马的旧版本 TeamViewer 安装包: https://t.co/YS1mmCo43o "
-

[ ReverseEngineering ] Extracting the master key from an iClass RFID reader by @ kchungco – PANDA makes a cameo appearance! https://blog.kchung.co/reverse-engineering-hid-iclass-master-keys/
" 从 iClass RFID 阅读器中提取 Master Key: https://t.co/9z2LobroAE"
-

[ Rootkit ] (2012) Great slide deck from @ snare on building EFI-based rootkits http://ho.ax/downloads/De_Mysteriis_Dom_Jobsivs_Black_Hat_Slides.pdf
" 基于 EFI 的 Rootkit,来自 BlackHat 2012 年的一篇演讲: https://t.co/gObWDb7PBP"
-

[ Sandbox ] Here's the slides from my talk on unprivileged containers and sandboxes, huge shout out to asciinemia for the gifs https://docs.google.com/presentation/d/1FGhm7S7bm8AwzF6eD8hb9m6cjf68Vr3ej-HzfYpGiNA
" 权限受限的容器与沙箱: https://t.co/iySNvEjhec "
-

[ Tools ] RT @ bartblaze: Recover encrypted files by #Nemucod #Ransomware: https://github.com/Antelox/NemucodFR By: @ Antelox
" Nemucod 勒索软件加密文件还原工具: https://t.co/rSeAambOmF "
-

[ Virtualization ] CVE-2016-3642 - Java Deserialization in Solarwinds Virtualization Manager 6… http://goo.gl/fb/aHPuMo #FullDisclosure
" Solarwinds Virtualization Manager 6.3.1 Java 反序列化漏洞(CVE-2016-3642),来自 FullDisclosure 公告: https://t.co/vyRuSNhVo9 "
-

[ Web Security ] Revisiting XSS payloads in PNG IDAT chunks https://www.adamlogue.com/revisiting-xss-payloads-in-png-idat-chunks/
" 存在于 PNG 文件 IDAT Chunks 中的 XSS Payload: https://t.co/Y6LHoBNHig"
-

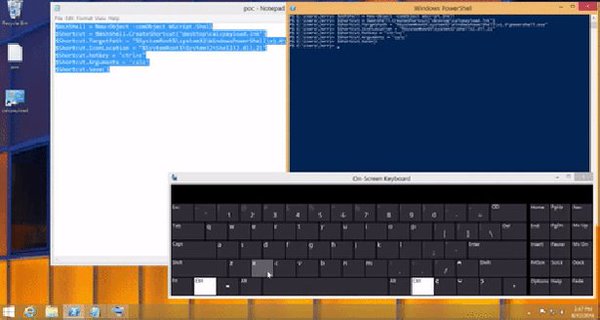
[ Windows ] Hijacking Common Windows Shortcuts with Powershell : http://jerrygamblin.com/2016/06/12/hijacking-common-windows-shortcuts-with-powershell/ https://t.co/HG1O3SpPKW
" 利用 PowerShell 劫持 Windows 快捷键︰ https://t.co/UowdNqB5oA https://t.co/HG1O3SpPKW"
-

[ Windows ] Windows 7 win32k bitmap use-after-free https://bugs.chromium.org/p/project-zero/issues/detail?id=747#c_ts1465979557 (MS16-062)
"Windows 7 win32k Bitmap UAF(CVE-2016-0173/MS16-062),来自 Project Zero Issue 747: https://t.co/GDN1I5NxXk "
-

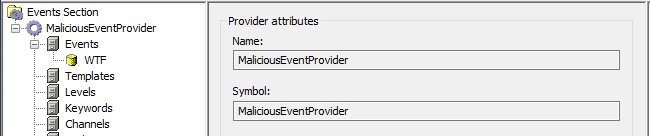
[ Windows ] Craft a malicious ETW Provider? Seems plausible... https://wychi.wordpress.com/2009/10/21/create-your-own-etw-provider-and-log-it-by-xperf/ My bet... someone has figured this out. https://t.co/bbOj8tw3qk
" 自己构造一个恶意的 ETW Provider: https://t.co/gKasxXTWcT "
-

[ Windows ] Ok #Bash & #WSL fans - drop everything! New post & video on Bash/WSL #filesystem features! https://blogs.msdn.microsoft.com/commandline/2016/06/15/new-post-and-video-on-wsl-filesystem-features/ https://t.co/GIePELQNIn
" WSL(Windows Subsystem for Linux) 是如何在 NTFS 之上提供一个 Linux 兼容的文件系统的,来自 MSDN 的视频: https://t.co/kNoIs35nZd https://t.co/GIePELQNIn"