腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] ProbeDroid - A dynamic binary instrumentation kit targeting on Android(Lollipop) 5.0 and above - https://github.com/ZSShen/ProbeDroid
"ProbeDroid - Android 动态二进制插桩工具,支持 5.0 及以上版本: https://t.co/pMEY2z5LbU "
-

[ Android ] JEB 2.2.5 is out with ARM 64 and MIPS Android debuggers - https://www.pnfsoftware.com/jeb2cl
"JEB 2.2.5 版本发布,加入对 ARM 64 和 MIPS 的调试支持: https://t.co/d1PsriPJyA"
-

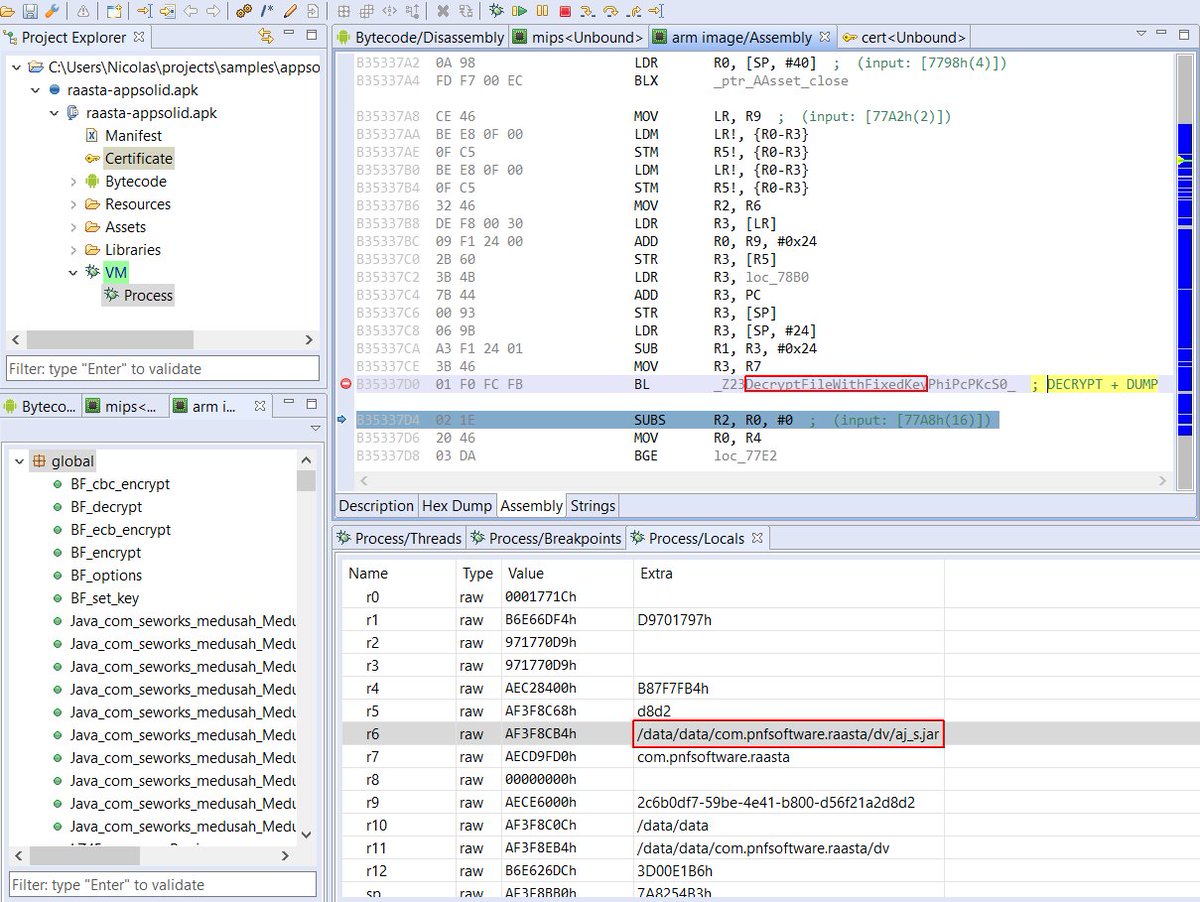
[ Android ] How to recover the orig. code of an Android app protected by AppSolid, tutorial and demo at https://www.pnfsoftware.com/blog/defeating-appsolid-android-protector/ https://t.co/oMoVTZ6SE3
" 还原 AppSolid 加固后的文件: https://t.co/VVSTni2CfQ "
-

[ Attack ] Dell Official Website Subdomains Hacked By Kurdish Hackers http://www.tapscape.com/dell-official-website-subdomains-hacked-kurdish-hackers/
"库尔德黑客黑掉了戴尔官方网站的子域名站点: https://t.co/i11dF9r9zu"
-

[ Attack ] Our June Threats Report is out! Dive into the findings: http://intel.ly/1UwCXpL
" McAfee 发布第二季度威胁报告︰ https://t.co/pDyEuKeg3B"
-

[ Attack ] ScarCruft APT deploys Adobe Flash Player zero-day in Operation Daybreak: https://securelist.com/blog/75082/cve-2016-4171-adobe-flash-zero-day-used-in-targeted-attacks/
" APT 组织 ScarCruft 在 Daybreak 定向攻击行动中用了一个 Flash 0Day(CVE-2016-4171),来自 Kaspersky Blog ︰ https://t.co/Kon7jBtM4j Adobe 为该漏洞发布公告: https://helpx.adobe.com/security/products/flash-player/apsa16-03.html "
-

[ Attack ] Crooks can clone payments cards with a hi-tech contactless device http://securityaffairs.co/wordpress/48355/cyber-crime/cloning-contactless-device.html
" 骗子可以通过非接触式设备克隆支付卡,来自 SecurityAffairs 的报道: https://t.co/gl81T6fK7X"
-

[ Attack ] #Unit42 finds new #sofacy attacks against US government agency http://bit.ly/1U6GfjL
" APT 组织 Sofacy 针对美国政府机构的新一波攻击,来自 Palo Alto Blog: https://t.co/Vw7Skd1Ye9"
-

[ Browser ] Just posted "Exploiting IE’s MS15-106, Part 2: JScript ArrayBuffer.slice Mem Disclosure(CVE-2015-6053)" + CFG bypass https://blog.coresecurity.com/2016/06/14/exploiting-internet-explorers-ms15-106-part-ii-jscript-arraybuffer-slice-memory-disclosure-cve-2015-6053/
" Exploit IE MS15-106 Part 2︰ JScript ArrayBuffer.slice 内存信息泄漏(CVE-2015-6053),来自 CoreSecurity Blog: https://t.co/AIokgXmlAZ"
-

[ Conference ] EnFuse 2016 Slides Open #enfuse2016, https://www.guidancesoftware.com/enfuse-conference/2016/presentations
" Enfuse 2016 会议 PPT 下载: https://t.co/r2eSDu5pYE"
-

[ Detect ] Identifying DNS sinkholes is important when tracking threat actors, here are some tips on finding them http://blog.passivetotal.org/kyf-if-might-be-a-sinkhole-if/ #FIRSTCON16
" 识别 DNS Sinkhole,追踪攻击者: https://t.co/tt3a70B7PY "
-

[ Detect ] Advanced Malware Evasion Techniques HTTP-Evader http://blogs.cisco.com/security/advanced-malware-evasion-techniques-http-evader
" 检测逃逸工具 HTTP-Evader 所用的逃逸技术: https://t.co/y1oYwzc9Pe"
-

[ iOS ] Another risky iOS advertisement SDK "Vpon" affected 36 apps in App Store: https://www.fireeye.com/blog/threat-research/2016/06/pwned_by_vpon.html Good job @ jxiej!
" 又一款存在风险的 iOS 广告 SDK - Vpon,攻击者可以实现远程截屏、录音、位置获取等,App Store 中 36 款 APP 受影响,来自 FireEye Blog︰ https://t.co/qr7sM1J5LR 受影响的 APP 列表: https://gist.github.com/chilik/11ffc141c0830ce6d8cea77bc1cdcf13 用一张图展示受影响 APP: https://pbs.twimg.com/media/Ck7pGYBXEAEsi8G.jpg:large "
-

[ iOS ] iOS 9.3 to iOS 10.0 API Differences https://developer.apple.com/library/prerelease/content/releasenotes/General/iOS10APIDiffs/index.html
"iOS 9.3 与 iOS 10.0 API 的差异: https://t.co/5gYzMat9D7"
-

[ iOS ] Digging into APFS, Apple’s new file system @ Lee_Ars | http://arstechnica.com/apple/2016/06/digging-into-the-dev-documentation-for-apfs-apples-new-file-system/
" WWDC 会议上,苹果公开了一种新的文件系统 APFS,来自 ArsTechnica 的报道: https://t.co/UZioAj0ob8"
-

[ iOS ] Continuing my annual tradition: "Notes from #iOS10 and the Mac #OSX 10.12 Preview" - http://newosxbook.com/forum/viewtopic.php?f=8&t=16692 … - v0.1 (more to follow later)
" iOS 10 和 Mac OS X 10.12 预览版的一些新变化: http://newosxbook.com/Articles/10-10.12.html "
-

[ macOS ] A new Python project 'macholibre' could parse CodeSignature and symbols in Mach-O file: https://github.com/aaronst/macholibre code clearer than macholib.
" macholibre - 一个用于解析 Mach-O 文件代码签名和符号信息的工具, GitHub Repo︰ https://t.co/FRnBnESPoz "
-

[ Malware ] RAA - An entirely new JS #ransomware delivering #Pony malware: https://rqt.io/1m https://t.co/7vcPOfEtBv
"RAA - 一款全新的 JS 勒索软件 ︰ https://t.co/61sqzvdz5X https://t.co/7vcPOfEtBv"
-

[ Malware ] New threat actor uses VBA macros in targeted attacks http://www.malware-reversing.com/2016/06/new-threat-actor-uses-vba-macros-in.html #Malware #Miskip
" 攻击者在定向攻击中使用恶意宏代码,来自 Malware Reversing Blog: https://t.co/Ttr9aQ6sGi "
-

[ Malware ] zCrypt Ransomware: under the hood https://blog.malwarebytes.org/threat-analysis/2016/06/zcrypt-ransomware/
"zCrypt 勒索软件分析: https://t.co/5pH1JW0Waa"
-

[ Obfuscation ] Obfuscator for the x86 assembler : https://www.pelock.com/products/obfuscator
" x86 汇编混淆器 ︰ https://t.co/tMg71CcCpr"
-

[ Others ] Project @ MSFTResearch : Checked C http://research.microsoft.com/en-us/projects/checkedc/ spec & code: https://github.com/Microsoft/CheckedC from David Tarditi, former Midori team member
" 微软 Checked C 项目: https://t.co/IXVAOTHty8 该项目的目的是为 C 代码加入边界检查, GitHub Repo︰ https://t.co/JaaJGOJbkv "
-

[ Others ] For those who missed my #FIRSTCON16 talk yesterday, the slides are online. Be sure to read through the references!! http://www.first.org/resources/papers/conf2016/FIRST-2016-122.pdf
" 基于 Java 的木马 - Mac 系统也跑不了,来自 FIRST 会议: https://t.co/Rj8y1EQBK8 FIRST 会议的其他 PPT 下载: http://www.first.org/resources/papers/conf2016 "
-

[ Others ] Critical Vulnerability Compromising Verizon Email Accounts (Again) https://randywestergren.com/critical-vulnerability-compromising-verizon-email-accounts/
" Verizon Webmail 门户网站存在严重漏洞,可以劫持任意用户收件箱中的邮件: https://t.co/QMd8r8Ze7N"
-

[ Pentest ] Common Malware Persistence Mechanisms http://resources.infosecinstitute.com/common-malware-persistence-mechanisms/
" 恶意软件常用的持久控制方法: https://t.co/QJiy6xPd1I"
-

[ Protocol ] Mobile communications: practical attacks using cheap equipment - http://www.synacktiv.ninja/ressources/synacktiv_mobile_communications_attacks.pdf @ FlUxIuS
" 基于廉价硬件设备的移动通信攻击: https://t.co/todwn2Xrwy "
-

[ SecurityProduct ] okay, finally wrote up my notes on my ClamAV scan http://blog.erratasec.com/2016/06/scanning-for-clamav-0day.html
" 在互联网上搜索 ClamAV 0Day: https://t.co/XciY3ygJ2Q ClamAV 会监听本地端口,等待执行命令"
-

[ Tools ] I've made a small script to dump functions from IDA into compilable C++ for re-usage purposes. https://github.com/agustingianni/Utilities#dumpfunctionbytespy
" 将 IDA 中的函数转储成 C++ 格式代码的工具: https://t.co/RxvzEuXOI1"
-

[ Web Security ] Cross-Site Content Hijacking PoC project has been updated to support CORS as well :) https://github.com/nccgroup/CrossSiteContentHijacking #XSCH
" CrossSiteContentHijacking - NCCGroup 开源的跨站数据劫持项目, GitHub Repo: https://t.co/WjPOlFiuES "
-

[ Web Security ] Online CSRF PoC Generator: A web alternative to the Burp Suite Pro and ZAP CSRF PoC generators https://security.love/CSRF-PoC-Genorator/
" CSRF PoC 生成器(在线工具): https://t.co/Kg3lBJ6nad "
-

[ Windows ] Cisco talks about Microsoft Patch Tuesday – 16 bulletins addressing 44 vulnerabilities ~ http://bit.ly/1XnVlqU via @ ciscosecurity
" 微软发布 6 月份补丁更新,本次共发布 16 个补丁,修复 44 个漏洞,来自 Cisco Blog 的讨论: https://t.co/hJ2dEjs7i4 ; 官方的补丁摘要信息: https://technet.microsoft.com/en-us/library/security/Mt733206.aspx 本次更新修复了由玄武实验室 tombkeeper 发现的一个影响 Win95 - Win10 所有版本的漏洞,该漏洞被命名为 'BadTunnel',来自 Forbes 的报道: http://www.forbes.com/sites/thomasbrewster/2016/06/14/microsoft-badtunnel-big-brother-windows-vulnerability/#587a45e25c64 "
-

[ WirelessSecurity ] Hamnet - A large scale high speed radio network : https://www.tapr.org/pdf/DCC2014-TheEuropeanHAMNET-DG8NGN.pdf (pdf) https://t.co/zXeW0WVUU6
" Hamnet - 大型高速无线电网络︰ https://t.co/V94vMtFmAo https://t.co/zXeW0WVUU6"