腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Want to fuzz Android applications? Drozer has a new module for that: https://github.com/mwrlabs/drozer-modules/blob/master/intents/fuzzinozer.py Crashes browser in 30s https://t.co/P6AR2ev6dt
"Drozer 新增了一个用于 Fuzz Android 应用的脚本: https://t.co/sfCRmvxvIk , 这个 Drozer-Modules 项目来自 MWR Labs,用于评估 Android 应用的安全性"
-

[ Attack ] [Ebook] What makes APT groups so persistent? #infosec http://bddy.me/1RlSo6L https://t.co/stWvQRa5Ce
"是什么让 APT 攻击者们如此执着? - 了解网络攻击以及他们的动机。 来自 FireEye 的报告: https://t.co/BDMrEtpMFt https://t.co/stWvQRa5Ce"
-

[ Debug ] Flare Script Series: Flare-Dbg Plug-ins https://www.fireeye.com/blog/threat-research/2016/02/flare_script_series.html #RE #malware
"FireEye Flare 脚本系列文章: 这次介绍其中的三个插件 injectfind、membreak 和 importfind: https://t.co/BoXAsfsCcA "
-

[ Detect ] Dealing with Linux Malware, the blog post (insights by the author of rkhunter). http://linux-audit.com/dealing-with-linux-malware-insights-by-the-author-of-rkhunter/ #malware #linux CC @ MalwareMustDie
"rkhunter 作者谈如何检测和防护 Linux 恶意软件: https://t.co/LR1qR9Ms5M "
-

[ Exploit ] Awesome Windows Exploitation : https://github.com/enddo/awesome-windows-exploitation
"Awesome Windows Exploitation, Github Repo: https://t.co/cbEYI1lphF"
-

[ Linux ] randkit : Random number rootkit for the Linux kernel : https://github.com/vrasneur/randkit
"randkit - 通过影响 Linux 内核随机数实现的 rootkit Demo, Github Repo: https://t.co/7CwQ8WKmqq"
-

[ Mac OS X ] Apple Pages, Numbers, Keynote Input Validation and XXE (CVE-2015-7032) http://nahamsec.com/apple-pages-numbers-keynote-input-validation-and-xxe-cve-2015-7032/ https://t.co/RuNsqREB2P
"Apple Pages、 Numbers、 Keynote 三个应用在解析文件时缺乏验证,存在 XXE 漏洞(CVE-2015-7032), 来自 NahamSec Blog 2015 年 11 月份的一篇文章: https://t.co/gmNfCXqF8C "
-

[ Malware ] Bedep Lurking in Angler's Shadows http://blog.talosintel.com/2016/02/bedep-actor.html
"潜伏在 Angler 阴影中的恶意软件下载器 Bedep, 来自 Talos Blog https://t.co/d0XLhfv0bw"
-

[ MalwareAnalysis ] Grammar and Spelling Errors in Phishing and Malware https://labs.opendns.com/2016/02/08/grammar-and-spelling-errors-in-phishing-and-malware/ #infosec
"钓鱼软件中的语法和拼写错误, 来自 OpenDNS Blog: https://t.co/mXVpbDXOgP "
-

[ MalwareAnalysis ] Technıcal Teardown: Maybank Phıshıng Malware – Part 1 http://www.vxsecurity.sg/2016/02/06/technical-teardown-maybank-phishing-malware/ #RE #malware
"Maybank 钓鱼恶意软件分析 Part 1, 来自 VXSecurity Blog: https://t.co/f0BFenrxky "
-

[ MalwareAnalysis ] REMnux v6 for Malware Analysis (Part 1): VolDiff : http://malwology.com/2015/06/25/remnux-v6-for-malware-analysis-part-1-voldiff/ , Part 2 : Static file analysis : http://malwology.com/2016/02/09/remnux-v6-for-malware-analysis-part-2-static-file-analysis/
"用 REMnux v6 分析恶意软件 Part 1: VolDiff : https://t.co/9oMutJEv8N Part 2 : 静态文件分析 : https://t.co/7EKSCM1uke"
-

[ MalwareAnalysis ] #Unit42 finds #NanoCoreRAT is behind an increase in tax-themed phishing e-mails http://bit.ly/1XgM80O
"NanoCoreRAT - 几乎每个事件或新闻都会伴有相关主题的钓鱼邮件出现, Palo Alto 发现最近税收主题的钓鱼邮件数量开始上升: https://t.co/Sxix6NIfzd "
-

[ Others ] The .NET File Format - http://www.ntcore.com/files/dotnetformat.htm
".NET 文件格式, 来自 NTCore: https://t.co/mjrX7BTxtN"
-

[ ThirdParty ] ACEDcup : Payload generator for Java Binary Deserialization attack : https://github.com/GrrrDog/ACEDcup
"ACEDcup: Apache Commons FileUpload 1.3 以前版本 Java 反序列化攻击 Payload 生成器, Github Repo: https://t.co/rD5EMwTTAB"
-

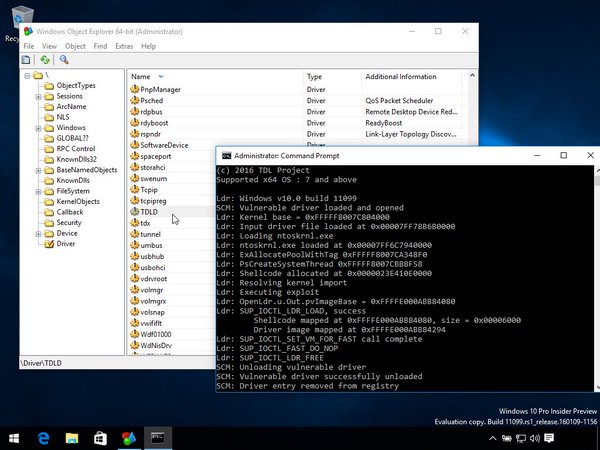
[ Tools ] Turla Driver Loader, bypassing Windows x64 Driver Signature Enforcement w/o kernel patch https://github.com/hfiref0x/TDL https://t.co/aeUKjtOVQw
"TDL - Turla 驱动加载器,可以绕过 Windows x64 驱动签名检查, Github Repo: https://t.co/N9FmtZo3oV "
-

[ Web Security ] SQL Injection: Exploitation : http://www.gracefulsecurity.com/sql-injection-exploitation/
"SQL 注入漏洞利用, 来自 Graceful Security Blog: https://t.co/F6rNfzvb0f"
-

[ Windows ] MS16-012 - Critical: Security Update for Microsoft Windows PDF Library to Address Remote Code Execution https://technet.microsoft.com/en-us/library/security/MS16-012
"微软 MS16-012 补丁修复了一个 Windows PDF 库的 RCE 漏洞,影响 Windows 8.1 及以后版本。 来自微软公告: https://t.co/oWDD8UgQ0Q 这个月所有公告的摘要信息: https://technet.microsoft.com/en-us/library/security/ms16-feb.aspx "
-

[ Windows ] PhoneInfo.dll DLL Hijacking Vulnerability in pretty graphs #infosec #exploits #MS16014 https://t.co/4WLlsy6tVa
"PhoneInfo.dll DLL 劫持漏洞调用序列图(MS16-014), 该 DLL 劫持漏洞的细节: https://github.com/CyberPoint/advisories/blob/master/SRT-VR-24DEC2015.txt "