腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Detect ] Major updates of CIRCL AIL - Analysis Information Leak framework https://github.com/CIRCL/AIL-framework including a simpler way to create new modules
"AIL-Framework - 信息泄露分析框架,主要是用于监控企业在类似 Pastebin 网站的信息泄露: https://t.co/dTLEwEuaG5"
-

[ Exploit ] CVE-2015-2545 ITW EMET Evasion https://twitter.com/r41p41/status/695309284092088320
"FireEye 检测到的 CVE-2015-2545 Docx 野外样本可以逃逸 EMET: https://t.co/WDSnmcEKR8"
-

[ Forensics ] Volume Shadow Copy and Registry Forensics https://montcs.bloomu.edu/~bobmon/DigFor/2012.HTCIA-conference/Talks/HTCIA%202012%20-%20VSC%20and%20Registry.pdf #DFIR
"卷影拷贝和注册表取证, 来自 HTCIA 2012 会议的演讲: https://t.co/HGTZ8cnISQ "
-

[ Hardware ] The micro architecture of Intel,AMD & VIA CPUs - Optimization guide for assembly programmers & compiler makers http://goo.gl/Tp4MEP (pdf)
"Intel、 AMD 和 VIA CPU 微体系架构与汇编、编译器开发者优化手册 (PDF): https://t.co/64TqsJQLLm "
-

[ Mac OS X ] Inside Mac Security : https://www.sans.org/reading-room/whitepapers/sysadmin/mac-security-34525 (pdf)
"Mac OS X 安全内幕, 来自 Sans 2014 年的一篇 Paper: https://t.co/jaa5NWv4BH "
-

[ Mac OS X ] Mondays are meh, but here's a new blog post! "Analyzing the Anti-Analysis Logic of an Adware Installer" https://objective-see.com/blog/blog_0x0C.html
"一款 OS X 平台伪装成 Flash 的广告安装包的反调试逻辑分析, 来自 Objective-See Blog: https://t.co/ss1TZxXqgh"
-

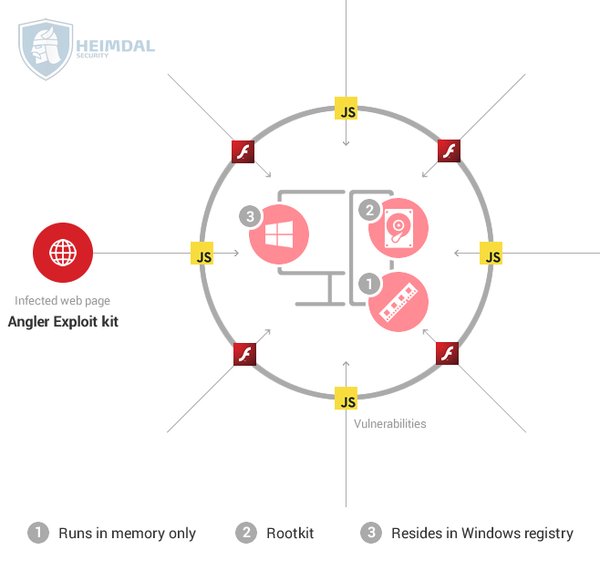
[ MalwareAnalysis ] Not all malware uses files. An introduction into fileless infections https://heimdalsecurity.com/blog/fileless-malware-infections-guide/ https://t.co/YwNuZTyrLp
"无文件型恶意软件的感染过程, 来自 Heimdal Security Blog: https://t.co/C95zi0C55A "
-

[ MalwareAnalysis ] Group-IB has published a report on the Corkow financial malware: http://www.group-ib.ru/brochures/Group-IB-Corkow-Report-EN.pdf https://t.co/0jNOc6TpW3
"Group-IB 关于 Corkow 金融恶意软件的分析报告: https://t.co/AXxHhavhhf https://t.co/0jNOc6TpW3"
-

[ Others ] rom dumping via the vibration motor #ReverseEngineering http://www.sodnpoo.com/posts.xml/mediatek_mt6261_rom_dumping_via_the_vibration_motor.xml
"通过振动电机 Dump ROM, Blog: https://t.co/7kWtuzeQuj "
-

[ Tools ] BIOS Implementation Test Suite - http://biosbits.org/ - https://github.com/biosbits/bits
"用于测试 BIOS 实现的套件: https://t.co/JVkERL9GmJ Github Repo: https://t.co/5cL8EcRE5d"
-

[ Tools ] gcc-explorer - interactive compiler - editable code and generated assembly - https://github.com/mattgodbolt/gcc-explorer demo: http://gcc.godbolt.org/
"gcc-explorer 交互式编译器, 支持直接编辑代码: https://t.co/6M6LaFk2w9 在线版: https://t.co/Rnt9GOPfSu"