腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] From APK to Golden Ticket - 通过 Android 手机渗透企业内网: https://docs.google.com/document/d/1XWzlOOuoTE7DUK60qTk1Wz1VNhbPaHqKEzyxPfyW4GQ/edit#heading=h.2m380ikv89me
-

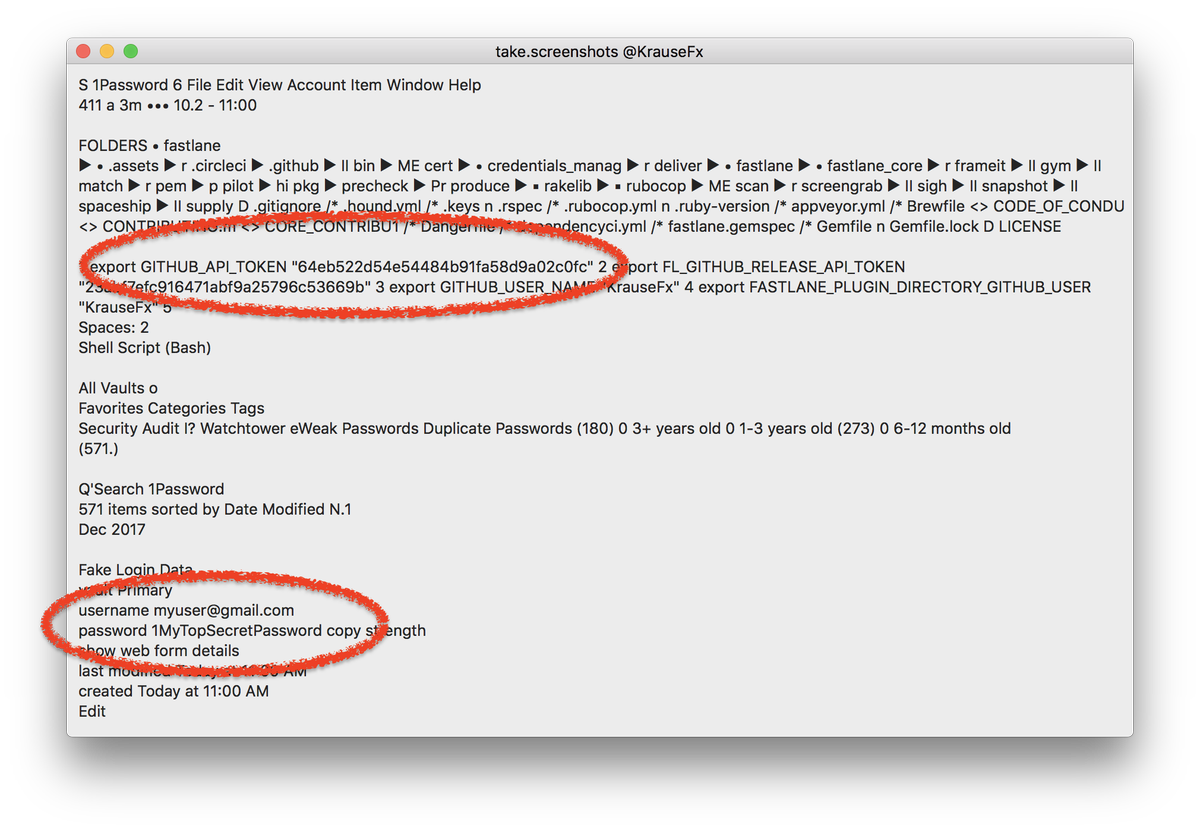
[ macOS ] macOS 沙箱内的 APP 可以在任何时间截屏,并且用户无感知: https://krausefx.com/blog/mac-privacy-sandboxed-mac-apps-can-take-screenshots
-
-

[ Popular Software ] Spotify 刚刚修复了一个 RCE 漏洞,PoC: https://twitter.com/steventseeley/status/962719615930466304
-
-

[ Windows ] 利用微软基于 RPC 实现的 DNS Server 管理协议,在域控服务器上实现 SYSTEM 代码执行,微软表示这个是个 Feature,不是 Bug: https://medium.com/@esnesenon/feature-not-bug-dnsadmin-to-dc-compromise-in-one-line-a0f779b8dc83
-

[ Windows ] WinLogon Windows 7 x64 COM 劫持的一种方法,这个怎么找到的呢?打开 ProcMon,过滤 NAME NOT FOUND 和 HKCU: https://gist.github.com/anonymous/3929d9df4035abec725bcdc36659fce5
-

[ macOS ] 利用 jtool 对 Apple File Conduit daemon 的逆向分析: http://newosxbook.com/articles/afcdecomposed.html
-
-

[ Processor ] CPUMicrocodes - Intel, AMD & VIA CPU 微码更新补丁文件收集: https://github.com/platomav/CPUMicrocodes
-

[ ReverseEngineering ] 反编译分析吃鸡辅助器外挂:无外挂功能,疑诈骗钱财: http://www.freebuf.com/articles/terminal/162190.html
-

[ Sandbox ] 通过跨进程通信逃逸 Adobe Reader 的沙箱,来自 sandboxescaper: http://sandboxescaper.blogspot.com/2018/02/how-to-escape-sandboxes-without.html?m=1
-