腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Industry News ] 垃圾邮件行动将 Locky 勒索软件与 FakeGlobe 一起进行推送: http://blog.trendmicro.com/trendlabs-security-intelligence/locky-ransomware-pushed-alongside-fakeglobe-upgraded-spam-campaigns/
-

[ Industry News ] 黑客 Kuroi’SH 黑掉了谷歌巴西的网站并挂了黑页: http://securityaffairs.co/wordpress/63138/hacking/google-brazil-domain-defacement.html
-

[ iOS ] iXintpwn/YJSNPI 滥用 iOS 配置 Profile 文件可以使手机失去响应: http://blog.trendmicro.com/trendlabs-security-intelligence/ixintpwn-yjsnpi-abuses-ioss-config-profile-can-crash-devices/
-

[ macOS ] 《The Python Bites your Apple:Fuzzing and exploiting OSX Kernel bugs》,《蛇噬汝果:基于Python的OSX内核漏洞模糊测试挖掘和利用》,来自科恩实验室 Flanker 在 XKungfoo 2016 会议的演讲: https://papers.put.as/papers/macosx/2016/xkungfoo.pdf
-

[ Mitigation ] 恶意 Chrome 插件分析: https://blog.0day.rocks/malicious-chrome-extension-meddling-with-your-searches-581aa56ddc9c
-

[ Others ] 探测 mimikatz 以及其他可疑的 lsass 访问 - Part 1: https://www.eideon.com/2017-09-09-THL01-Mimikatz/
-

[ Others ] RDP劫持 - 如何透明地劫持 RDS 和 RemoteApp 会话: https://medium.com/@networksecurity/rdp-hijacking-how-to-hijack-rds-and-remoteapp-sessions-transparently-to-move-through-an-da2a1e73a5f6?source=linkShare-7db6d2df42a6-1505686152
-

[ Popular Software ] 攻击者利用 MS Word 未公开特性实现(打开word文件时)发起 HTTP 请求,进而可以在服务端收集客户端的操作系统和软件版本信息: https://securelist.com/an-undocumented-word-feature-abused-by-attackers/81899/
-

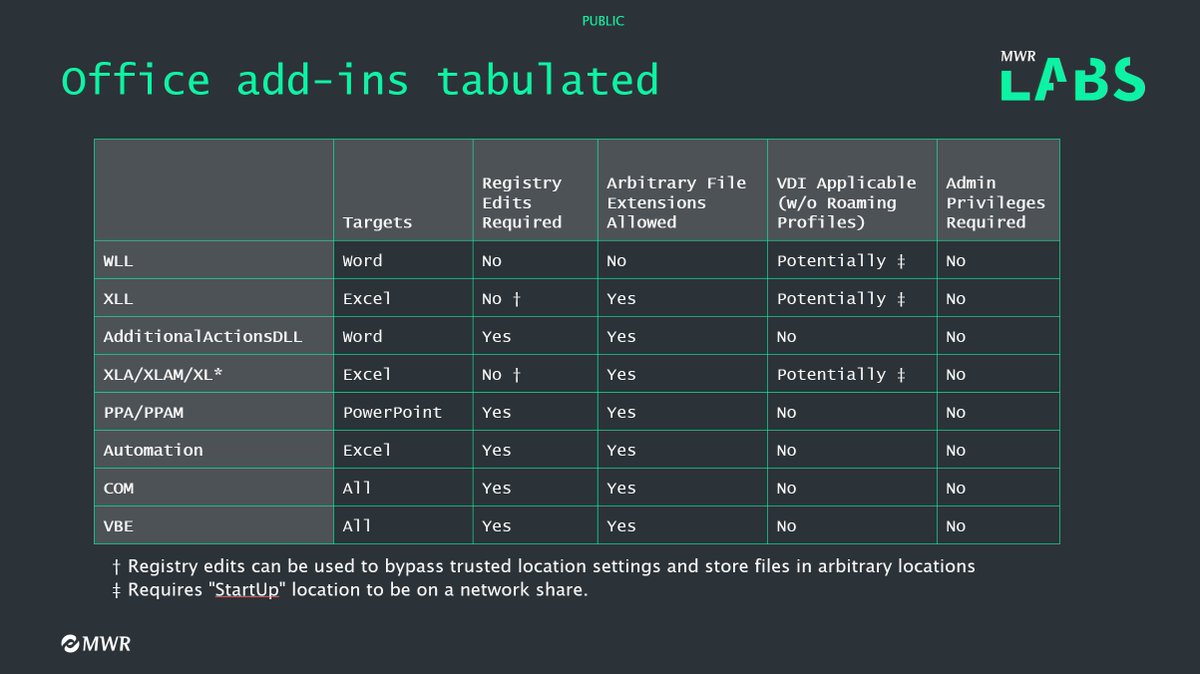
[ Popular Software ] Microsoft Office 有哪些特性可以被后门用来实现常驻(Persist),来自 MWR Labs: https://labs.mwrinfosecurity.com/publications/persisting-with-microsoft-office/
-

[ Tools ] 写一个编译器,探索 TypeScript 到 WebAssembly 的编译过程: https://medium.com/web-on-the-edge/exploring-compilation-from-typescript-to-webassembly-f846d6befc12
-
-

[ Tools ] idahunt - NCCGroup 开源的用于辅助 IDA Pro 逆向分析的工具,譬如批量分析二进制文件: https://github.com/nccgroup/idahunt
-

[ Web Security ] Optionsbleed - HTTP OPTIONS 方法可以泄露 Apache Server 的内存: https://blog.fuzzing-project.org/60-Optionsbleed-HTTP-OPTIONS-method-can-leak-Apaches-server-memory.html
-

[ Windows ] Active Directory ACL 的攻与防: https://blogs.technet.microsoft.com/enterprisemobility/2017/09/18/active-directory-access-control-list-attacks-and-defense/
-

[ Windows ] Project Zero 昨天公开了多个 Windows 内核(主要是 win32k)的漏洞详情(CVE-2017-8682/CVE-2017-8684/CVE-2017-8708/CVE-2017-8677/CVE-2017-8687/CVE-2017-8685/CVE-2017-8678): https://bugs.chromium.org/p/project-zero/issues/detail?id=1273 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1275 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1269 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1306 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1304 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1276 ; https://bugs.chromium.org/p/project-zero/issues/detail?id=1307
-

[ Windows ] Windows 系统中进程、线程的枚举以及 Image 加载通知的回调: http://www.triplefault.io/2017/09/enumerating-process-thread-and-image.html
-
-

[ Backdoor ] 基于 Logon 脚本的常驻后门方法: https://3gstudent.github.io/3gstudent.github.io/Use-Logon-Scripts-to-maintain-persistence/
-

[ Browser ] 微软 Edge Web 峰会 2017 上的一个演讲《Building a safer browser: Four guards to keep users safe》,视频: https://channel9.msdn.com/Events/WebPlatformSummit/Microsoft-Edge-Web-Summit-2017/ES03
-
-
-

[ Industry News ] 系统清理工具 CCleaner 8月15日上线的 5.33 版本被植入后门: http://www.piriform.com/news/blog/2017/9/18/security-notification-for-ccleaner-v5336162-and-ccleaner-cloud-v1073191-for-32-bit-windows-users http://blog.talosintelligence.com/2017/09/avast-distributes-malware.html http://www.freebuf.com/news/148119.html
-

[ Industry News ] 网页上的污染源:“PM2.5报告”插件实为恶意广告注射器: http://www.freebuf.com/articles/terminal/147797.html
-
-
-

[ iOS ] TenSec 2017 会议上 iPhone 6 虚拟化议题的演示视频,来自蒸米 Spark: https://twitter.com/SparkZheng/status/909610143104475139
-
-
-
-

[ Tools ] rVMI - 基于虚拟机自省(VMI)技术的全系统分析,来自 FireEye: https://www.fireeye.com/blog/threat-research/2017/09/rvmi-full-system-analysis.html
-

[ Tools ] Empire中的Invoke-WScriptBypassUAC利用分析: https://3gstudent.github.io/3gstudent.github.io/Empire%E4%B8%AD%E7%9A%84Invoke-WScriptBypassUAC%E5%88%A9%E7%94%A8%E5%88%86%E6%9E%90/
-
-
-

[ Windows ] 利用 PowerShell 找一个具有写权限的 Windows 服务: https://3gstudent.github.io/3gstudent.github.io/Use-powershell-to-find-a-writable-windows-service/