腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Backdoor ] Backdooring Your Python Programs (THOTCON 0x8 Talk Slides + Src Code) : http://www.ikotler.org/InYourPythonPath.pdf (Slides) , Github : https://github.com/SafeBreach-Labs/pyekaboo
" 如何给 Python 代码植入后门, upper() 已不是那个 upper(): http://www.ikotler.org/InYourPythonPath.pdf , Github : https://github.com/SafeBreach-Labs/pyekaboo "
-

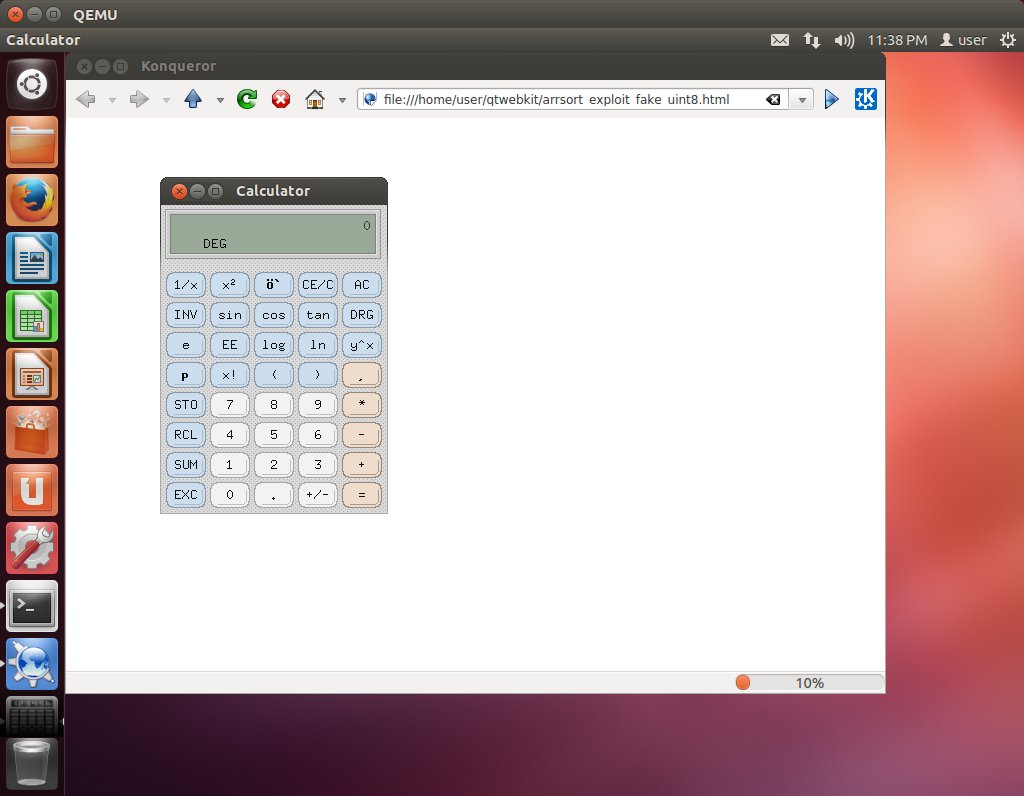
[ Browser ] [blog] [1day] Ode to the use-after-free: one vulnerable function, a thousand possibilities: https://scarybeastsecurity.blogspot.com/2017/05/ode-to-use-after-free-one-vulnerable.html https://t.co/5NyLySbP5C
" 唱给 UAF 的赞歌:WebKit Array.sort() UAF 漏洞的分析和利用(CVE-2012-3748),该漏洞曾被用于 Mobile Pwn2Own 2012,来自 Chris Evans: https://scarybeastsecurity.blogspot.com/2017/05/ode-to-use-after-free-one-vulnerable.html "
-

[ Fuzzing ] Slides for my @ stirtrek talk "High Speed Bug Discovery with Fuzzing" https://speakerdeck.com/craigstuntz/high-speed-bug-discovery-with-fuzzing
" High Speed Bug Discovery with Fuzzing: https://speakerdeck.com/craigstuntz/high-speed-bug-discovery-with-fuzzing "
-

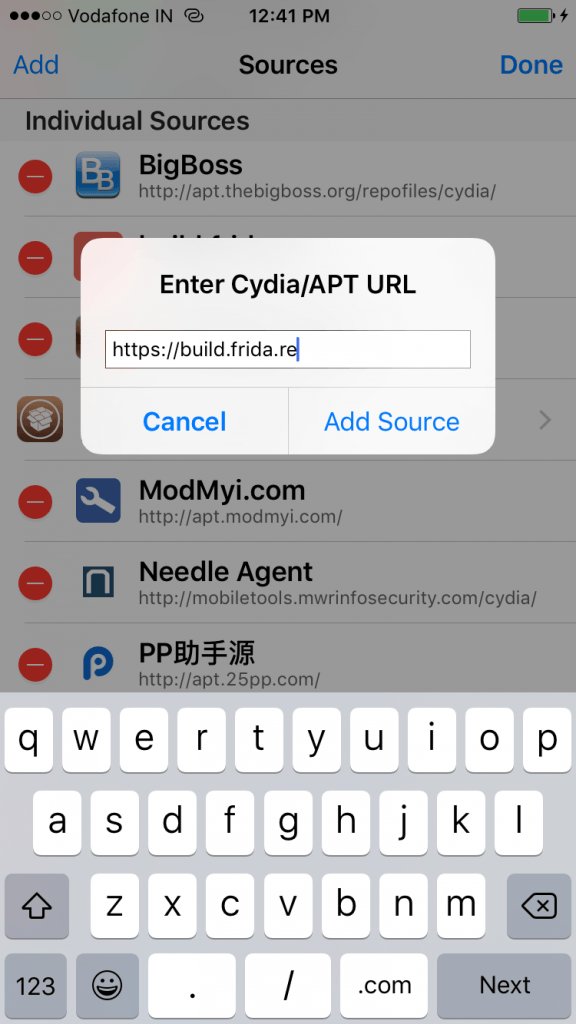
[ iOS ] Bypass Jailbreak Detection with Frida in iOS applications http://blog.attify.com/2017/05/06/bypass-jailbreak-detection-frida-ios-applications/ https://t.co/jQbTQO8kWE
" 在 iOS 应用中使用 Frida 的入门教程 : http://blog.attify.com/2017/05/06/bypass-jailbreak-detection-frida-ios-applications/ "
-

[ Operating System ] Updated Debian Linux 8: 8.8 released https://www.debian.org/News/2017/20170506 #sysadmin
" Debian 8.8 新版发布,同时提供了该版的安全更新与 bug 修复列表 : https://www.debian.org/News/2017/20170506 "
-

[ Popular Software ] First post - "From 404 and default pages to RCE via .cshtml webshell" #cybersecurity #pentest #bugbounties https://t.co/LBEs5AV7YS
" 针对 razorC.net CMS 的安全测试,篡改 .cshtml 文件以获取 WebShell: https://niemand.com.ar/2017/05/05/from-404-and-default-pages-to-rce-via-cshtml-webshell/ "
-

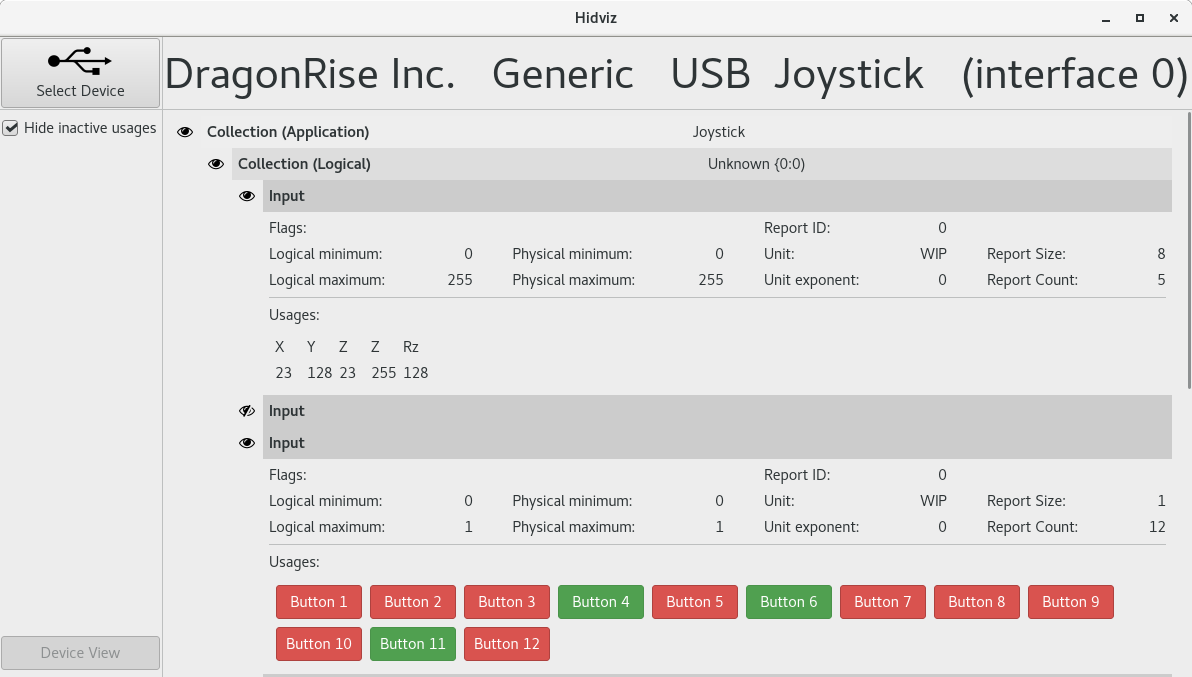
[ Tools ] hidviz : Tool for in-depth analysis of USB HID devices communication : https://github.com/ondrejbudai/hidviz/ https://t.co/LTLdsmUkwE
" Hidviz - 用于分析 USB HID 类设备通信过程的工具(有 GUI 可视化界面): https://github.com/ondrejbudai/hidviz/ "
-

[ Vulnerability ] I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way. ???
" Tavis Ormandy 表示他和同事发现了一个近期最严重的 Windows 远程代码执行漏洞: https://twitter.com/taviso/status/860679110728622080 "