
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Potential hacking devices found on Carleton University computers aka a Hardware keyboard logger https://www.thestar.com/news/canada/2017/03/28/potential-hacking-devices-found-on-carleton-university-computers.html
"加拿大卡尔顿大学 6 个教室的计算机上发现了潜在的键盘记录器: https://t.co/knlNqW6zRz"
-

[ Challenges ] Project Zero blog: "Project Zero Prize Conclusion" by @ natashenka - https://googleprojectzero.blogspot.com/2017/03/project-zero-prize-conclusion.html
" 去年 9 月,'Project Zero Prize' 计划开始,但是至今没有收到任何的漏洞提交,这篇是 Project Zero 对此的总结: https://t.co/7FMsLrs0pY"
-

[ Exploit ] Privilege Escalation: Manual privilege escalation techniques on Unix and Windows - https://helix.stormhub.org/data/Advanced%20Topics%20in%20Security/Lecture%20slides/Lecture%2010%20-%20Privilege%20Escalation.pdf #Hacking #Pentesting #PrivEsc
" Unix 和 Windows 系统中的本地提权技术总结: https://t.co/RDZ5DlHH7w "
-

[ macOS ] Third-party installer packages may not be installable by the macOS 10.12.4 OS installer: https://derflounder.wordpress.com/2017/03/29/third-party-installer-packages-may-not-be-installable-by-the-macos-10-12-4-os-installer/
" macOS 10.12.4 发布之后, OS Installer 有所更新,第三方未经过签名的 Installer Package 装不上了︰ https://t.co/rlHdJSZXGf"
-

[ Malware ] We have observed multiple #ransomware families using NSIS installers to avoid detection. See our analysis:… https://twitter.com/i/web/status/846948805308305409
" McAfee 近期发现多款勒索软件开始利用 NSIS 安装器 + 加密 Payload 的方式躲避检测: https://securingtomorrow.mcafee.com/mcafee-labs/ransomware-families-use-nsis-installers-to-avoid-detection-analysis/?utm_source=twitter&utm_campaign=Labs#sf66375875 "
-

[ Malware ] Trojanized Adobe Installer used to Install DragonOK’s New Custom Backdoor https://blogs.forcepoint.com/security-labs/trojanized-adobe-installer-used-install-dragonok%E2%80%99s-new-custom-backdoor
" Adobe Reader 的安装器被发现用于安装 DragonOK 定制后门,来自 Forcepoint: https://t.co/Dv78C3lF3n "
-

[ Mitigation ] ROP CFI RAP XNR CPI WTF? – Navigating the Exploit Mitigation Jungle (@ f0rki) - https://bsidesljubljana.si/rop-cfi-rap-xnr-cpi-wtf-navigating-exploit-mitigation-djungle-michael-rodler/ #BSidesLjubljana #video
" BSides 会议上一篇针对 ASLR/CFI 等缓解措施的总结: https://t.co/NCarLKtGf4 "
-

[ ReverseEngineering ] iaito : A Qt and C++ GUI for radare2 reverse engineering framework : https://github.com/hteso/iaito cc @ hteso https://t.co/NgQsUh143v
"iaito - 基于 Qt 和 C++,为 radare2 逆向框架写的一个 UI 交互接口: https://t.co/PqmlklCiBs https://t.co/NgQsUh143v"
-

[ Web Security ] An In-Depth Analysis (code review, alt. attack vector) of the Struts RCE Vulnerability CVE-2017-5638 https://blog.gdssecurity.com/labs/2017/3/27/an-analysis-of-cve-2017-5638.html
"struts S2-045 漏洞的深度分析(CVE-2017-5638): https://t.co/T277FZseFv "
-

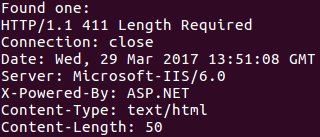
[ Windows ] How many servers are vulnerable to CVE-2017-7269 (WebDAV IIS/6.0)? roughly 60k. https://medium.com/@ iraklis/number-of-internet-facing-vulnerable-iis-6-0-to-cve-2017-7269-8bd153ef5812 https://t.co/EggcQjWVoD
"根据研究员的扫描结果,总计有 6 万台 IIS/6.0 服务器受 CVE-2017-7269 漏洞的影响: https://t.co/zZxBpOT6QQ https://t.co/EggcQjWVoD"
-

[ Windows ] The Windows 10 Creators Update is coming April 11th, with EdgeHTML 15. Begin testing today with the preview VMs on… https://t.co/v2nEfP1UV3
"Windows 10 Creators 大版本更新将于 4 月 11 号发布,同时发布的还有 EdgeHTML 15,目前可以下载测试虚拟机环境了: https://t.co/v2nEfP1UV3"
-
[ Android ] 如何通过恶意充电器控制你的 OnePlus 3/3T(译文):http://bobao.360.cn/learning/detail/3670.html
-
[ Windows ] CVE-2017-7269 IIS 6.0 远程代码执行漏洞分析及 Exploit: http://whereisk0shl.top/cve-2017-7269-iis6-interesting-exploit.html

 Xuanwu Spider via 安全客
Xuanwu Spider via 安全客