
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] Microsoft Edge Fetch API allows setting of arbitrary request headers https://goo.gl/fb/c8Kmng #FullDisclosure
"Microsoft Edge Fetch API 允许设置任意请求头可绕过SOAP限制(CVE-2017-0140): https://t.co/PverQW0xHd 漏洞细节: https://www.securify.nl/advisory/SFY20170101/microsoft_edge_fetch_api_allows_setting_of_arbitrary_request_headers.html"
-

[ Browser ] URL spoofing in UC browser. https://goo.gl/fb/S2d3BM #FullDisclosure
"Android 版 UC 浏览器中的存在 URL 欺骗: https://t.co/clUZfnayrS "
-

[ Language ] Creating Easy to Read/Actionable stack traces for non-rusteceans w/ @ rustlang , and @ getsentry https://rust-lang.life/sentry-in-rust/
"调用栈回溯信息对于快速定位 Bug 非常有用,但和 Ruby 语言不同,Rust 语言的栈回溯不够直接和清晰,所以作者尝试解决这个问题: https://t.co/u5br2Am6Au "
-

[ Language ] Future of Java 8 Language Feature Support on Android : https://android-developers.googleblog.com/2017/03/future-of-java-8-language-feature.html TL;DR; jack discontinue, java 8 added to javac and dx
"Google 开发者官方 Blog 表示将在 Android 上提供对 Java 8 语言的支持︰ https://t.co/4aKKZtqSDn "
-

[ macOS ] New macOS Proton RAT Available for Sale on Russian Hacking Forum https://www.bleepingcomputer.com/news/security/new-macos-proton-rat-available-for-sale-on-russian-hacking-forum/ #RAT #macOS #Apple https://t.co/4gjPlJDlWq
"针对 macOS 的 RAT 工具 Proton 在俄罗斯地下黑客论坛中叫卖: https://t.co/F4iUu3Ca6W "
-

[ MalwareAnalysis ] Relying on social networking as its infection vector, our new blog provides analysis of a new variant of #Dorkbot:… https://twitter.com/i/web/status/841512481029795840
"针对 Dorkbot Botnet 新变种的分析,来自 McAfee Labs: https://securingtomorrow.mcafee.com/mcafee-labs/analyzing-fresh-variant-dorkbot-botnet/"
-

[ Others ] Great Job: Heap Spraying -> https://www.exploit-db.com/docs/31019.pdf
"ActiveX 控件的构建、漏洞挖掘和利用,来自 HackSys Team 一篇 2013 年的 Paper: https://t.co/9a2bZwiy0A"
-

[ Others ] Here are the slides from my BlueHat 2016 talk on WSL in RS2/Creator's Update (many issues fixed by now): https://t.co/NjMpudURLJ
"Alex Ionescu 在 Bluehat 2016 会议关于 Windows Linux 子系统的演讲,深入分析了 WSL 子系统的实现以及潜在的安全问题,还包括 RS2 版本上 WSL 的一些变化︰ https://t.co/NjMpudURLJ"
-

[ Pentest ] Using the ELK Stack and Python in Penetration Testing Workflow https://qbox.io/blog/elk-penetration-testing-workflow-elasticsearch-python
"在渗透测试工作中使用 ELK 和 Python : https://t.co/k2bashLbtz"
-

[ Popular Software ] Adobe Flash: Use-after-free in MovieClip attach init object https://bugs.chromium.org/p/project-zero/issues/detail?id=1006
"Project Zero 爆出的一堆 Adobe 漏洞:CVE-2017-2931: https://bugs.chromium.org/p/project-zero/issues/detail?id=1005 CVE-2017-2932: https://t.co/oKkjbmRV96 CVE-2017-2934: https://t.co/SPkb1a4wfX CVE-2017-2935: https://t.co/RAhqjKbgBI"
-

[ SecurityReport ] MS17-010 - Critical: Security Update for Microsoft Windows SMB Server (4013389) - Version: 1.0 https://technet.microsoft.com/en-us/library/security/MS17-010
"Microsoft 官方发布 2017 年 3 月安全公告: https://technet.microsoft.com/en-us/library/security/ms17-mar.aspx 其中修复了一个 SMB 服务的远程代码执行漏洞: https://t.co/OlZXHxWVpc 类似该漏洞函数 SrvRestartExecuteTransaction 的补丁,还有一处相似的修复位置:SRV!ExecuteTransaction: https://twitter.com/i/web/status/841719286011850752 还有多个 Hyper-V vSMB 的远程代码执行漏洞: https://technet.microsoft.com/library/security/MS17-008 本月致谢: https://technet.microsoft.com/zh-cn/library/security/mt745121.aspx "
-

[ Tools ] Information Security Reference That Doesn't Suck https://github.com/rmusser01/Infosec_Reference
" Infosec_Reference -- 信息安全资源索引: https://t.co/JYubR1Sxdw"
-

[ Tools ] PegaSwitch - an exploit toolkit for the Nintendo Switch https://pegaswitch.com/
"PegaSwitch -- 任天堂 Switch 漏洞利用套件: https://t.co/rcs3TJ8SDw"
-

[ Tools ] McSema can run libFuzzer on binary code now. https://github.com/trailofbits/mcsema/blob/master/docs/UsingLibFuzzer.md https://twitter.com/trailofbits/status/841602710361276416
"McSema -- 将 x86 和 amd64 架构的二进制文件转化为 LLVM 位码的工具: https://t.co/UW5eBL8iDq "
-

[ Virtualization ] Path traversal to escape guest<->host VM shared folder. Vmware 2008? No Virtualbox 2017. ?cooperating VMs trick https://t.co/yEhu2XSb6p
"VirtualBox: cooperating VMs can escape from shared folder,两个 VirtualBox Guest 虚拟机可以合作,通过共享文件夹实现对 Host 机的逃逸,获得 Host 机整个文件系统的访问权限。主要是通过条件竞争实现的: https://t.co/yEhu2XSb6p"
-

[ Windows ] [Blog] Bypassing UAC using App Paths https://enigma0x3.net/2017/03/14/bypassing-uac-using-app-paths/ Works on Windows 10, specifically tested on build 15031 and later. cc/ @ 0xrhyno
"Win 10 环境下利用修改 APP 路径的方式绕过 UAC 防御的技巧: https://t.co/DjHcrKTDDm "
-

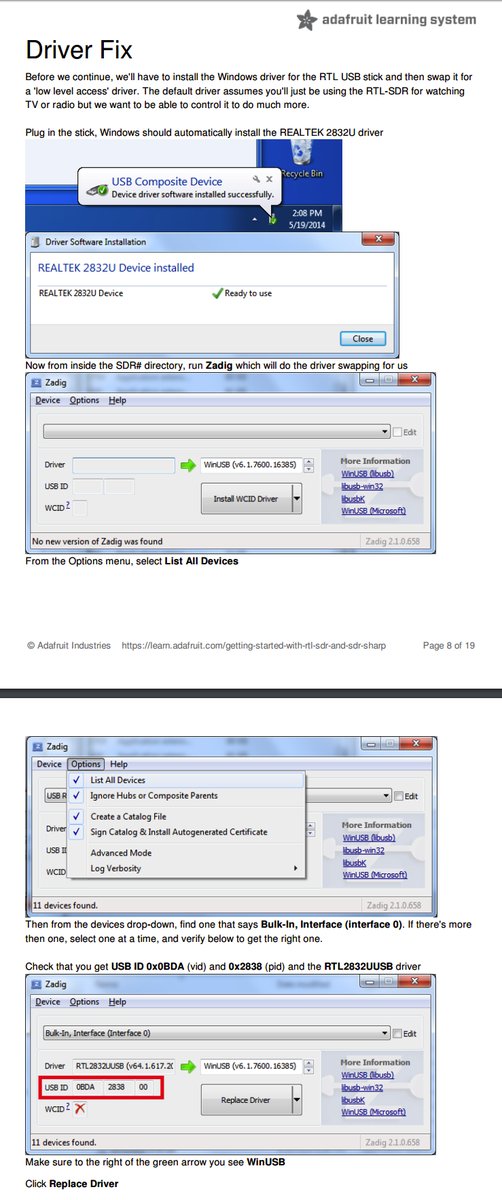
[ WirelessSecurity ] Getting Started with RTL-SDR and SDR-Sharp #SDR #RTL [PDF] https://cdn-learn.adafruit.com/downloads/pdf/getting-started-with-rtl-sdr-and-sdr-sharp.pdf https://t.co/Xka3hChqnH
"入门 RTL-SDR 及 SDR-Sharp : https://t.co/3e1qCw8SyB "
-
[ SecurityReport ] 今年的 Pwn2Own 即将开始,Google, Adobe, VMWare, Firefox, Microsoft 纷纷发布补丁来补补补;那么到底补了哪些漏洞?ZDI 带我们看看史上补了最多补丁的星期二: https://www.zerodayinitiative.com/blog/2017/3/14/the-march-2017-security-update-review
 Xuanwu Spider via seebug
Xuanwu Spider via seebug