
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ MalwareAnalysis ] Our insights on #TorrentLocker variants that have been using new attack methods to target European nations: http://bit.ly/2nkVPPp
"TrendLabs 发现了勒索软件 TorrentLocker 的新变种及攻击目标 ︰ https://t.co/mxBuhulcrs"
-

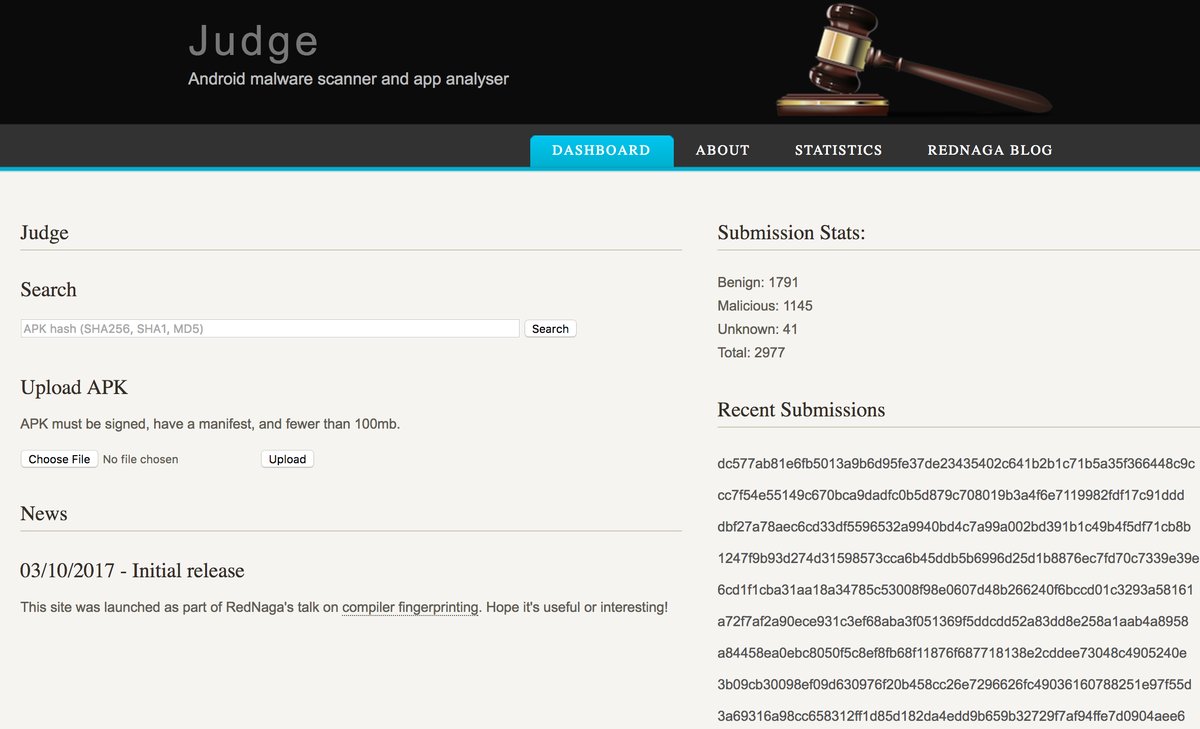
[ MalwareAnalysis ] Released Judge, an Android app analyzer and experimental malware detector: http://judge.rednaga.io/ https://t.co/Xi7HWitwmM
" Judge -- 使用机器学习,编译器指纹识别等技术的 Android 恶意软件在线检测平台︰ https://t.co/au1WyfPuT7 "
-

[ Others ] a handy dandy CIA "how to write malware" tradecraft howto. https://www.wikileaks.org/ciav7p1/cms/page_14587109.html#efmAQ6AR7AYlAZXA-VBBJBBSBCQBCbBExBHXBKGBv9Bw9ByBBy-Bz2B0OB02B1yB8mB9jCQZCR1CSmCTR
"CIA 的工具开发要求,以防御逆向分析与计算机取证: https://t.co/9WF3goqJUj"
-

[ Others ] A very nice updated list of file format signatures.. (aka "magic numbers") http://garykessler.net/library/file_sigs.html (thank you!)
"各种文件格式的文件头 Magic Header 列表: https://t.co/o2FpvV1Xra "
-

[ Programming ] Very cool hack. How to recover lost Python source code if it's still resident in-memory #programming #devops https://t.co/71RWRtpbKr
"从内存恢复 Python 代码的教程: https://t.co/71RWRtpbKr"
-

[ Tools ] Remote Windows box is x86 or x64? #kekeo misc::arch can help *without authentication* ? Thanks to @agsolino for ide… https://t.co/rtDAg5XwF8
" kekeo -- 基于 C 编写的 Microsoft Kerberos 工具箱: https://github.com/gentilkiwi/kekeo"
-

[ Tools ] Update your VMware instances: https://github.com/ivildeed/vmw_vmx_overloader
"vmw_vmx_overloader -- 利用 VMware Workstation Pro/Player 设计上的缺陷,在 Windows 10 x64 内核中加载未签名的的代码︰ https://t.co/NFfY4JRODL"
-

[ Tools ] New 'USG' Firewalls Protect USB Drives From Malicious Attacks : https://github.com/robertfisk/USG/wiki ,Technical Details :… https://twitter.com/i/web/status/840914355663360000
"USG -- USB硬件防火墙,用于防御 BADUSB 攻击︰ https://t.co/tKqcPUHgP6 技术细节: https://t.co/YzhWP1VKiF"
-

[ Windows ] This only took me 4 years to write :-) Abusing default Windows Kernel Debugging settings to bypass the login screen. https://tyranidslair.blogspot.co.uk/2017/03/getting-code-execution-on-windows-by.html
"如何滥用默认 Windows 内核调试配置实现代码执行,最终获得 SYSTEM 特权,来自 James Forshaw :: https://t.co/6QLQSlrIIX"
-
[ Windows ] 探索基于Windows 10的Windows内核Shellcode(Part 1): http://bobao.360.cn/learning/detail/3575.html 探索基于Windows 10的Windows内核Shellcode(Part 2): http://bobao.360.cn/learning/detail/3593.html
-
[ Others ] CIA 泄露文档中一篇关于利用 Junction Folders 和 COM 对象实现用户态持久控制的方法(Persistence): https://wikileaks.org/ciav7p1/cms/page_13763373.html
-
[ Linux ] 一条命令引发的思考,文章主要对 Linux SSH 后门原理进行了分析: https://xianzhi.aliyun.com/forum/mobile/read/790.html
-
[ Android ] Android 应用中 local socket 引发的安全问题总结,来自 Flanker_017 的微博,Paper《Android Unix Domain Sockets 的误用以及带来的安全问题》: http://web.eecs.umich.edu/~yurushao/pubs/sinspector_ccs2016.pdf
 Xuanwu Spider via 安全客
Xuanwu Spider via 安全客