腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Twitter leaked database: 32 million accounts http://slexy.org/view/s22uHdUCdG (Not verified)
"Twitter 数据库泄露(待验证): https://t.co/nMZtp7CbLH "
-

[ Browser ] New blog post: Decoding Chrome's HTTPS UX: https://noncombatant.org/2017/02/15/decoding-chromes-https-ux/
" Chrome 浏览器与 HTTPS、SSL、证书安全相关的用户体验问题: https://t.co/WKGvs7MYB4"
-

[ Browser ] Web Inspector JavaScript Debugger has better stepping, breakpoints, async call stacks, and new Web Worker support!… https://twitter.com/i/web/status/831941571608248321
" WebKit 的 JavaScript 调试器在单步调试、断点处理、异步调用栈分析等方法有了改进: https://t.co/ZeQgttuk9z"
-

[ Detect ] Here are the slides from the Sysmon presentation I just delivered at @ RSAConference https://1drv.ms/p/s!AubxkJFptCbQlhvLwkUygf1dSeaM
" 从应急响应到威胁检测 - 基于 Sysinternals 的 Sysmon 工具实现: https://t.co/jeS1gbU5gu "
-

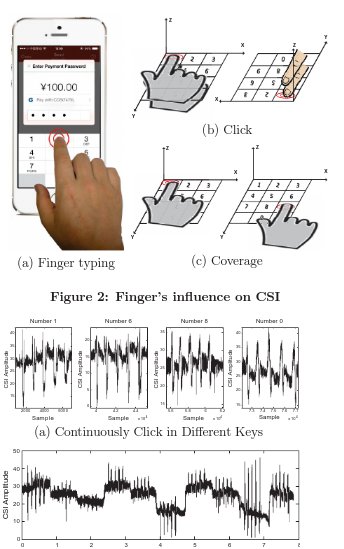
[ Hardware ] Inferring Your Mobile PhonePassword via WiFi Signals : http://fermatslibrary.com/s/when-csi-meets-public-wifi-inferring-your-mobile-phone-password-via-wifi-signals (pdf) https://t.co/3JMWUhJpc0
" 通过手势移动对 WiFi 信号的影响推断手机密码,Paper︰ https://t.co/Wz6nRQun4h https://t.co/3JMWUhJpc0"
-

[ IoTDevice ] Phwning the boardroom: hacking an Android conference phone http://www.contextis.co.uk/resources/blog/phwning-boardroom-hacking-android-conference-phone/ #cybersecurity #hacking #infosec… https://t.co/WD06G3SJNj
"黑掉会议室中的 Android 会议电话: https://t.co/OvVwsAQIzd "
-

[ Linux ] Exploit Dev 0x01 | 64-bit Linux Stack Buffer Overflow http://badbytes.io/2017/02/15/exploit-dev-0x01-64-bit-linux-stack-buffer-overflow/
"64 位 Linux 栈缓冲区溢出漏洞利用代码开发: https://t.co/oHqdfEMtrb"
-

[ MachineLearning ] Slides from my "Advances in Cloud-Scale Machine Learning for Cyber-Defense" session at @RSAConference yesterday: https://t.co/56nCPVtALs
" 基于云的机器学习在网络防御方面的优势,来自 RSA大会︰ https://t.co/56nCPVtALs"
-

[ Malware ] Let’s Unpack: Dridex Loader https://www.malwaretech.com/2017/02/lets-unpack-dridex-loader.html
" Let's Unpack Dridex Loader: https://t.co/zwRKVQiylx"
-

[ Malware ] ChChes – Malware that Communicates with C&C Servers Using Cookie Headers http://blog.jpcert.or.jp/2017/02/chches-malware--93d6.html
"2016 年 10 月,日本 CERT 发现了一款利用 Cookie Headers 实现 C&C 通信的恶意软件 - ChChes: https://t.co/plKnxhfXwl"
-

[ MalwareAnalysis ] #Unit42's @ r0bf4lc analyzes Sofacy’s XAgent macOS Tool: http://bit.ly/2lIjs7I
"Sofacy 组织的 XAgentOSX 木马分析,来自 Unit42︰ https://t.co/2EHkIReNx2"
-

[ MalwareAnalysis ] Malware Analysis with OllyDbg http://resources.infosecinstitute.com/malware-behavior-code-analysis-part-3/
"借助 OllyDbg 工具分析恶意软件: https://t.co/w91I9mkO7D"
-

[ MalwareAnalysis ] Here is the full 40+ page Google report into likely Russian state malware https://www.documentcloud.org/documents/3461560-Google-Aquarium-Clean.html https://t.co/XDv0SfcX1m
" Google 安全团队在 2014 年发过一篇分析 Aquarium 高级恶意软件的报告,提到其与俄罗斯有关: https://t.co/oANp39aupz https://t.co/XDv0SfcX1m"
-

[ Mitigation ] Four Ways to bypass Control Flow Guard (CFG) in Microsoft Edge + Source code: https://medium.com/@ mxatone/mitigation-bounty-4-techniques-to-bypass-mitigations-2d0970147f83
" Bypass CFG 缓解措施的 4 种方法,这几种方法被微软的 Bounty 计划拒绝了,所以作者放在了这里︰ https://t.co/Z3vmkcVND1"
-

[ OpenSourceProject ] Advisory X41-2017-002: Multiple Vulnerabilities in ytnef - https://www.x41-dsec.de/lab/advisories/x41-2017-002-ytnef/
"Outlook winmail.dat 文件解析库 ytnef 被发现多个漏洞: https://t.co/QLYKD5Xe9i"
-

[ Others ] [Technical Advisory] Privilege Escalation in CA Common Services casrvc due to Arbitrary Write https://www.nccgroup.trust/us/our-research/advisory-craigsblackie-cve-2016-9795/?research=Technical+advisories
"CA Common Services casrvc 存在任意写入漏洞可导致权限提升: https://t.co/mFq8AOj6PC "
-

[ Pentest ] Compromising Domain Admin in Internal Pentest https://goo.gl/7NnxBX #Bloodhound #Powersploit #Pentest #LazyKatz #Powershell
"内网渗透中获取域管权限: https://t.co/vObQmjNobP "
-

[ Popular Software ] Arbitrary command/code execution bugs in RVM. Hooking cd can be hazardous to your health. https://github.com/justinsteven/advisories/blob/master/2017_rvm_cd_command_execution.md
" RVM(Ruby Version Manager) 1.28.0 版本存在多个任意代码执行漏洞: https://t.co/o1lZr0600f"
-

[ Rootkit ] Chapters 2-14 of Rootkits and Bootkits are available now in Early Access! https://www.nostarch.com/rootkits https://t.co/CjioDa2lDi
" 一本新书《Rootkits and Bootkits》: https://t.co/pVxOv44aBs https://t.co/CjioDa2lDi"
-

[ SecurityProduct ] Cisco ASA: Buffer overflows in WebVPN cifs handling https://bugs.chromium.org/p/project-zero/issues/detail?id=998
"思科 ASA WebVPN cifs 存在缓冲区溢出: https://t.co/ybYkJJdhH6"
-

[ Tools ] Writing a basic C# decompiler. Good Read http://www.codeandux.com/writing-a-simple-decompiler-for-net-part-1/
"写个简单的 C# 反编译器, Part 1: https://t.co/bRJWx4pmg4 Part 1b: http://www.codeandux.com/writing-a-simple-decompiler-for-net-part-1b/ "
-

[ Tools ] How to #backdooring with #TheFatRat: post-exploitation attack for Windows, Android, Mac. Integrated with… https://t.co/m01My1aWkC
" TheFatRat - 基于 Metasploit 的 msfvenom,快速生成后门的工具: https://github.com/Screetsec/TheFatRat"
-

[ Tools ] IoTSeeker Perl script to #scan a network for specific types of #IoT by @Rapid7 Author: @jinq102030 https://t.co/CGaw0zJYpz
"IoTSeeker - 用于扫描特定类型 IoT 设备是否保留出厂时的密码设置的工具: https://t.co/CGaw0zJYpz"
-

[ Vulnerability ] Coppermine Gallery (all versions) <= 1.5.44 arbitrary file download 0day exploit https://github.com/HackerFantastic/Public/blob/master/exploits/cpg15x-dirtraversal.txt
" PHP Coppermine Gallery 图片处理库 1.5.44 及之前版本存在任意文件下载漏洞: https://t.co/tnO3Ou4Weo"
-

[ Web Security ] 5 ways to Exploit LFi Vulnerability http://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability/
"LFi(本地文件包含)漏洞利用的五种方法: https://t.co/g3upf78P73 "
-

[ Web Security ] How SSL affects search rankings https://blog.detectify.com/2017/02/15/ssl-search-rankings/
"网站启用 SSL 会提高在 Google 中的搜索排名: https://t.co/Q5600Ub0r6"
-

[ Windows ] Here are my slides from the .Net Hijacking to Defend PowerShell Talk #bsidessf2017 http://www.slideshare.net/AmandaRousseau1/net-hijacking-to-defend-powershell-bsidessf2017
" 从 .Net 劫持到 PowerShell 攻击防御,来自 BsidesSF 2017 会议: https://t.co/uFWzeFSIKD"
-

[ Windows ] Windows GDI32.dll Heap Based out of bounds Memory disclosure, Google Project Zero. https://bugs.chromium.org/p/project-zero/issues/detail?id=992&q=
"Windows GDI32.dll 在处理 EMF 的 DIB 时存在一个堆上的越界读信息泄露漏洞(CVE-2017-0038): https://t.co/gSsP2K1ink"
-

[ Windows ] Windows Kernel Fuzzing for Beginners is pretty high level, still has some relevant stuff. https://m.youtube.com/watch?v=FY-33TUKlqY https://t.co/pwkljbLOJ4
"Windows Kernel Fuzzing 入门,来自 RuxCon 2013 会议的演讲视频: https://t.co/3Rtgp33ASN https://t.co/pwkljbLOJ4"
-

[ Windows ] Windows Kernel Exploitation : http://www.hacking-training.com/download/WKE.pdf (pdf) cc @ GranetMan
"基于 HackSys Extreme Vulnerable Windows Driver,介绍 Windows 内核漏洞利用的 Paper︰ https://t.co/QiCA48GLog "
-

[ Windows ] LLMNR / NBT-NS Spoofing Attack https://www.aptive.co.uk/blog/llmnr-nbt-ns-spoofing/
"LLMNR/NBT-NS 欺骗攻击: https://t.co/JeXlobPZAt"
-

[ Windows ] Attack Windows Kernel Graphics 1: https://www.blackhat.com/docs/us-14/materials/us-14-vanSprundel-Windows-Kernel-Graphics-Driver-Attack-Surface.pdf 2: http://2015.zeronights.org/assets/files/11-Tarakanov.pdf 3: https://googleprojectzero.blogspot.nl/2017/02/attacking-windows-nvidia-driver.html
"Windows 内核图形驱动攻击面相关的几篇 Paper,分别来自 BlackHat 2014: https://t.co/Q4qoNz9DIs ZeroNights 2011: https://t.co/r9vCBz2v6R Project Zero Blog: https://t.co/Uj4pVQ5Vq5"