腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android: KASLR bypass in "pm_qos" https://bugs.chromium.org/p/project-zero/issues/detail?id=971
" Samsung: KASLR bypass in "pm_qos": https://t.co/NPSthDjmPp"
-

[ Pentest ] The slides from my @BlueHatIL talk "The Travelling Pentester: Diaries of the Shortest Path to Compromise" are up at https://t.co/9ygQpqXTB1
"旅行中的渗透测试工程师与渗透的最短路径: https://t.co/9ygQpqXTB1"
-

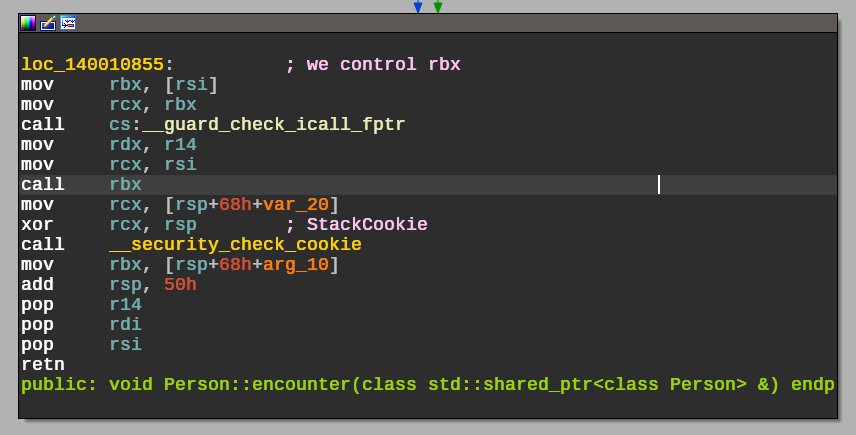
[ Windows ] Exploiting a misused C++ shared pointer on Windows 10 : https://blog.scrt.ch/2017/01/27/exploiting-a-misused-c-shared-pointer-on-windows-10/ https://t.co/xOtAy0uMtr
" Exploiting Windows 10 系统一个误用的共享指针,这是一道 CTF 题的解答:: https://t.co/RzOlwP2NhJ https://t.co/xOtAy0uMtr"
-

[ Windows ] Papers, blogposts, tutorials for learning about Windows kernel exploitation, internals & (r|b)ootkits : https://github.com/sam-b/windows_kernel_resources cc @ _samdb_
"Sam Brown 整理的 Windows 内核相关的资料,目前有驱动、内存破坏漏洞相关资料: https://t.co/PPMfmLEWFb "
-

[ Windows ] Uploaded our @BlueHatIL slide deck "The Enemy Within: Stopping Advanced Attacks Against Local Users" https://t.co/Sc7qnzXcJM via @SlideShare
" BlueHatIL 会议的一篇演讲《内部敌人-阻断针对本地用户的高级攻击》: https://t.co/Sc7qnzXcJM "