
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android - IOMXNodeInstance::enableNativeBuffers unchecked index https://bugs.chromium.org/p/project-zero/issues/detail?id=932
"Android IOMXNodeInstance::enableNativeBuffers 未检查索引: https://t.co/tOlo4i11xD"
-

[ Browser ] Brave Browser 1.2.16/1.9.56 - Address Bar URL Spoofing (iOS + Android) : https://www.exploit-db.com/exploits/40994/ cc @ aaditya_purani || @ thehackerledge
"Brave Browser 1.2.16/1.9.56 存在地址栏 URL 欺骗漏洞︰ https://t.co/mNM8yZAXSc "
-

[ Browser ] The Official Tor Browser For iOS Is Free To Use http://arstechnica.com/security/2017/01/tor-onion-browser-ios-vpn/
"iOS 版官方 Tor Browser 现在可以免费使用了: https://t.co/kKb4o0fR1r"
-

[ Cloud ] Our #NDSS17 paper "Hello from the Other Side: SSH over Robust Cache Covert Channels in the Cloud" is now online:… https://t.co/XBTGVq5luX
"SSH over Robust Cache Covert Channels in the Cloud: https://cmaurice.fr/pdf/ndss17_maurice.pdf"
-

[ Industry News ] 27k MongoDB Instances Have Now Been Hacked http://www.zdnet.com/article/mongodb-ransacked-now-27000-databases-hit-in-mass-ransom-attacks/
"上万 MongoDB 数据库被黑,数据库所有者遭遇勒索 : https://t.co/BGcHgPR4VC"
-

[ Industry News ] .@ HelloKitty database of 3.3M breached credentials surfaces - http://bit.ly/2jvYKqK
"HelloKitty 母公司 Sanrio 数据库泄漏,330 万用户凭证受影响: https://t.co/weeHEdeIc2"
-

[ IoTDevice ] Internet of Things IoT radio frequency RF Analysis With Software Defined Radio Kevin Bong #SDR #HackRF #IoT… https://twitter.com/i/web/status/818292136370061316
"利用 SDR 分析 无线电频率,来自 GrrCon 2016 大会: https://t.co/VpVCokqF8E"
-

[ IoTDevice ] Hacking The IoT (Internet of Things) - PenTesting RF Operated Devices [PDF] #SDR #GnuRadio #RFcat… https://twitter.com/i/web/status/818294066886496258
"Hacking The IoT (Internet of Things) - PenTesting RF Operated Devices (PDF): https://t.co/eMMO1fayrv"
-

[ IoTDevice ] How to Build a Command Injection Exploit for the Netgear R7000 https://www.hackingloops.com/netgear-r7000-exploit/
"Netgear R7000 命令注入漏洞利用: https://t.co/c5SLvqOPsL "
-

[ Others ] Cracking The 12+ Character Password Barrier, Literally : http://www.netmux.com/blog/cracking-12-character-above-passwords
"Hash 破解的多个技巧︰ https://t.co/8LEaaRU0u0"
-

[ Others ] A great article by @s4sh_s on setup GDT table & X86 segments (so you can emulate Windows shellcode) with Unicorn: https://t.co/rXwQ4tSOwL
"在 Unicorn 模拟器中创建 GDT 表︰ https://t.co/rXwQ4tSOwL"
-

[ Programming ] Open-sourced our research on C++ hierarchy reconstruction in binaries https://github.com/RUB-SysSec/Marx
"揭开 C++ 程序的类层次结构: https://t.co/G10xYwNiyN"
-

[ SecurityProduct ] Bypass all the AV's!! https://www.youtube.com/watch?v=EYuHAqY0xSw
"Bypass all the AV's: https://t.co/sZ2w4CmY6u"
-

[ SecurityReport ] The ZDI 2016 Retrospective: 674 advisories, 54 0-days, $2,000,000 paid out: http://blog.trendmicro.com/zdi-2016-retrospective/ #vulnerabilities #exploits #0days #0day
"ZDI 回顾过去 2016 : https://t.co/WroxgRBcV2 "
-

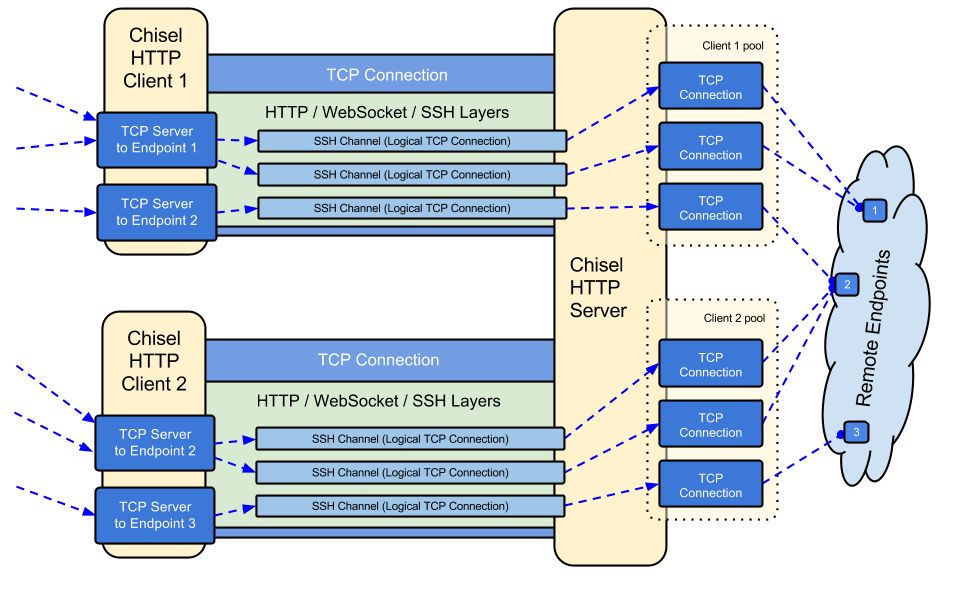
[ Tools ] chisel : A fast TCP tunnel over HTTP : https://github.com/jpillora/chisel https://t.co/SvjUU5g9vf
"chisel -- 基于 HTTP 的高速 TCP 隧道工具 : https://t.co/Z3YfCNdAWE https://t.co/SvjUU5g9vf"
-

[ Tools ] TruffleHog high-entropy key hunter released to the masses http://www.zdnet.com/article/trufflehog-high-entropy-key-hunter-released-to-the-masses/#ftag=RSSbaffb68
"Truffle Hog -- 从 Github 中扫描私钥 : https://t.co/gHwCXzJDQF,GitHub: https://github.com/dxa4481/truffleHog"
-

[ Tools ] Rux - A hobbyist microkernel written in Rust - https://github.com/sorpaas/rux
"Rux -- 一个 Rust 语言编写的微内核 : https://t.co/U4v7lheVUm"
-

[ Vulnerability ] Cemu v1.6.4b infoleak + buffer overflow = emulator breakout (code exec on host) https://gist.github.com/Wack0/cf10d061880b4597181796f843651e52
"利用任天堂 Wii U 模拟器(Cemu)上两个漏洞实现在 host 机上执行代码 : https://t.co/eIXKdPZOFr"
-

[ Vulnerability ] Gaming network @ ESEA breached, 1.5M profiles leaked - http://bit.ly/2jvKldV https://t.co/C2zDiUhOS1
"ESEA 游戏平台上百万用户信息遭泄露 : https://threatpost.com/gaming-network-esea-breached-1-5m-profiles-leaked/122933/"
-

[ Web Security ] Remote Exploit - Shellcode without Sockets : https://0x00sec.org/t/remote-exploit-shellcode-without-sockets/1440
"Remote Exploit - Shellcode without Sockets︰ https://t.co/XfrXY5XjR7"
-

[ Web Security ] Web Application Penetration Testing : Local File Inclusion (LFI) Testing Techniques : https://www.exploit-db.com/docs/40992.pdf (pdf) https://t.co/DPkJm8hLg1
"PHP 本地包含漏洞测试技巧︰ https://t.co/u2GNTQVH0n "
-

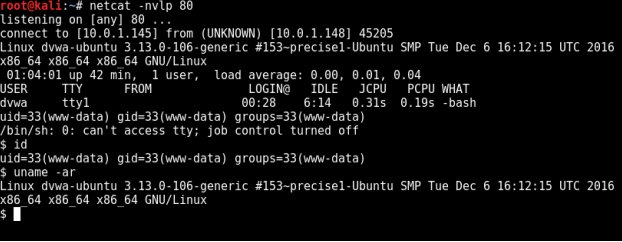
[ Web Security ] Damn Vulnerable Web Sockets - vulnerable web application which works on web sockets for client-server communication: https://github.com/interference-security/DVWS
" DVWS --针对 Web Sockets 的 web 应用安全测试实验环境︰ https://t.co/agF4QSgg3I"
-
[ ReverseEngineering ] Sublime Text 3 3114 编辑器的逆向破解过程:http://blog.fernandodominguez.me/cracking-sublime-text-3/
-
[ iOS ] Frida 9.0 发布,支持在越狱 iOS 10.1.1 上启动 APP(不依赖 Substrate): https://twitter.com/fridadotre/status/818278080095678464
-
[ Mobile ] 有研究者研究发现,小米的 Bootloader 锁并不安全,包括最新的 Mi Mix:https://gist.github.com/anonymous/5fd967b3fe5d9201e0ec7a1d35c03a19
-
[ Private ] WSL team fixed the non-elevated vs elevated vulnerability in build 15002:https://twitter.com/aionescu/status/818593743079178240
-
[ MalwareAnalysis ] ForcePoint 对 MM Core 后门的分析:https://blogs.forcepoint.com/security-labs/mm-core-memory-backdoor-returns-bigboss-and-sillygoose
-
[ iOS ] Racing for everyone: descriptor describes TOCTOU,苹果iOS/OSX内核中的新型漏洞: http://keenlab.tencent.com/zh/2017/01/09/Racing-for-everyone-descriptor-describes-TOCTOU-in-Apple-s-core/
 Xuanwu Spider via 腾讯安全联合实验室
Xuanwu Spider via 腾讯安全联合实验室