腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ iOS ] A new iPhone bug will crash the Messages app with a single text http://securityaffairs.co/wordpress/54923/mobile-2/messages-app-bug.html
"仅用一个文本消息便可使你的 iphone Messages 应用崩溃: https://t.co/5dLEMv1HkV"
-

[ Others ] In case anyone is using libplist to parse plist files for security scanning, here are some fun parser differentials. https://t.co/rnszPXAvs8
"libplist 的 XML 解析器的存在多个 BUG: https://t.co/rnszPXAvs8"
-

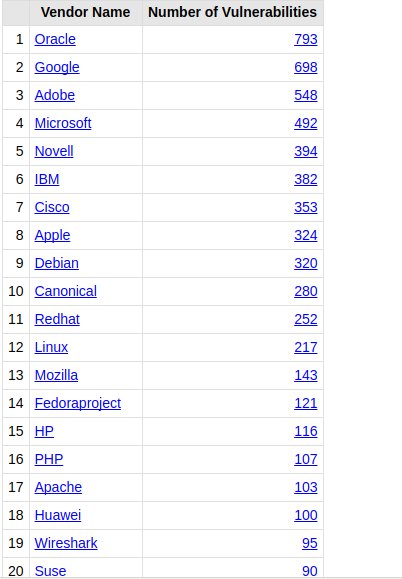
[ Others ] Top 50 Vendors By Total Number Of "Distinct" Vulnerabilities in 2016 : http://www.cvedetails.com/top-50-vendors.php?year=2016 https://t.co/tRgoYuk8aM
"CVE Details 发布 2016 年 Top 50 厂商漏洞数排名: https://t.co/o3JrO6P5Ki https://t.co/tRgoYuk8aM"
-

[ Others ] Constant-Time Callees with Variable-Time Callers: https://eprint.iacr.org/2016/1195 featuring OpenSSL 1.0.1u ECDSA P-256 key recovery vulnerability.
"Constant-Time Callees with Variable-Time Callers︰ https://eprint.iacr.org/2016/1195.pdf"
-

[ Others ] Be Careful with Python's New-Style String Format : http://lucumr.pocoo.org/2016/12/29/careful-with-str-format/ cc @ mitsuhiko
"小心使用 Python 的 str.format() 方法,错误使用将导致内部属性信息泄漏︰ https://t.co/8n1toA1Sqx"
-

[ Programming ] #happy2017 everyone :) Here's a short (and hopefully fun) read on how to pwn Lua with malicious bytecode: https://saelo.github.io/misc/pwning-lua-through-load.html #33c3ctf
"Pwning Lua through 'load'︰ https://t.co/oLG40rPIUp "
-

[ WirelessSecurity ] Dissecting modern (3G/4G) cellular modems : http://git.gnumonks.org/laforge-slides/plain/2016/cellular_modems_33c3/33c3-modems.html#(1) (Slides) ,Video : https://media.ccc.de/v/33c3-8151-dissecting_modern_3g_4g_cellular_modems https://t.co/0zv8Qa32Qr
"解剖现代 (3g/4g) 蜂窝调制解调器,来自 33c3 2016 大会议题︰ https://t.co/3zdn4cTBTB Video︰ https://t.co/GNvgP6NF4g "