
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] Most fun exploit I ever wrote: [0day] [exploit] Redux: compromising Linux using SNES Ricoh 5A22 processor opcodes?! https://goo.gl/bwNwm2
"利用任天堂 SNES 攻破 Fedora 25 + Google Chrome: https://t.co/5aVNxI3vZP"
-

[ Browser ] UXSS on Microsoft Edge – Adventures in a Domainless World/Learn to find your own UXSS - Broken Browser https://www.brokenbrowser.com/uxss-edge-domainless-world/
"Microsoft Edge 浏览器在 about:blank 页面下的 UXSS: https://t.co/VePidlgITi"
-

[ Browser ] [advisory] Microsoft Internet Explorer HyperlinkString Out-Of-Bounds Read Information Disclosure Vulnerability https://t.co/kNq78M6cAV
"Microsoft IE 浏览器 HyperlinkString 越界读信息泄漏漏洞(CVE-2016-7278): https://t.co/kNq78M6cAV"
-

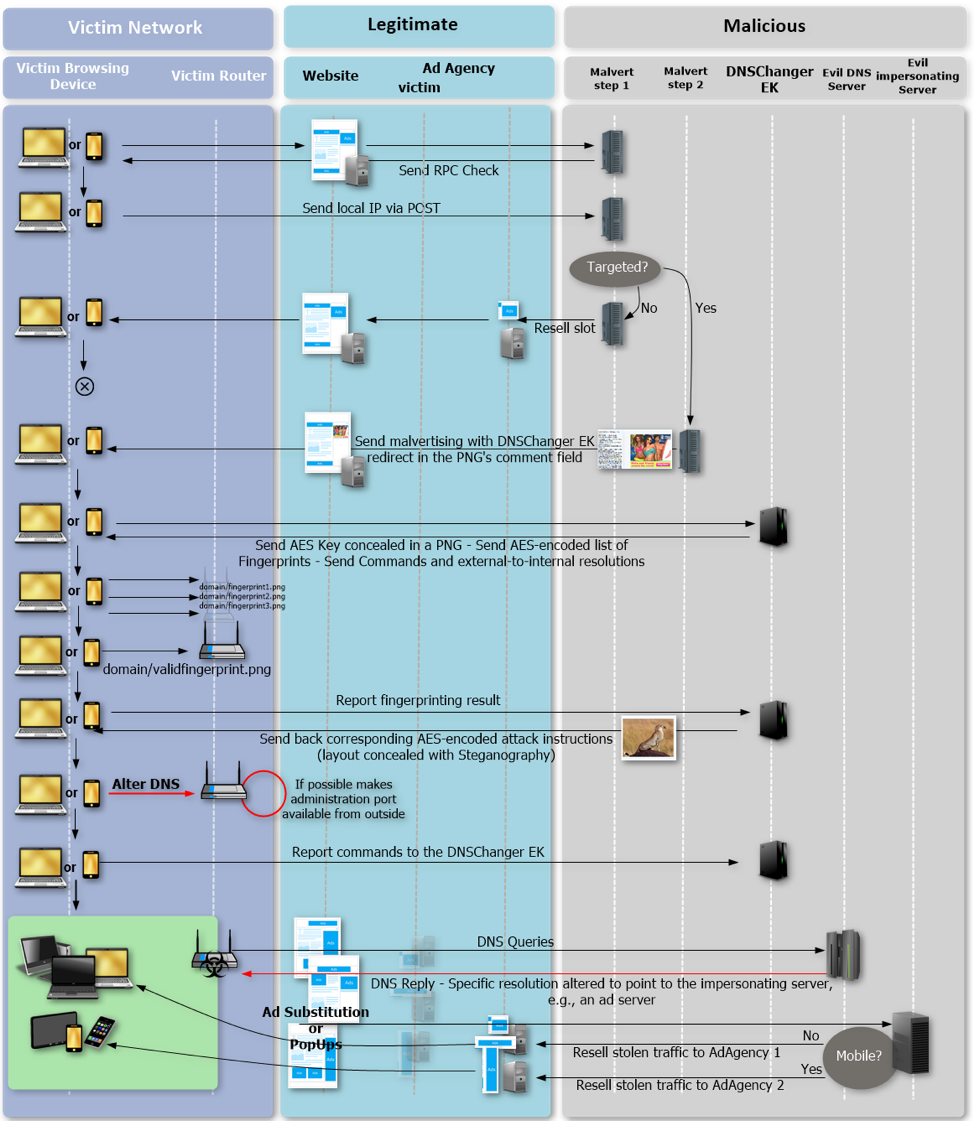
[ Hardware ] Routers under attack of an improved DNSChanger EK (via malvertising on Android and Windows) https://www.proofpoint.com/us/threat-insight/post/home-routers-under-attack-malvertising-windows-android-devices https://t.co/bkDfnwG5pj
"针对家用路由器的恶意广告攻击: https://t.co/tbRzNqCYI0 https://t.co/bkDfnwG5pj"
-

[ iOS ] iOS 10.1.x Remote memory corruption through certificate file https://cxsecurity.com/issue/WLB-2016110046
"iOS 10.1.x 证书文件导致远程破坏漏洞(CVE-2016-7626): https://t.co/6t8n7mlxbr "
-

[ MalwareAnalysis ] The rise of TeleBots: Analyzing disruptive KillDisk attacks http://www.welivesecurity.com/2016/12/13/rise-telebots-analyzing-disruptive-killdisk-attacks/
"TeleBots 的兴起︰ KillDisk 攻击分析: https://t.co/xTfqzfANze"
-

[ Mobile ] Mobile Application Testing Cheatsheet and Testing Checklist - https://github.com/sh4hin/MobileApp-Pentest-Cheatsheet
"移动应用渗透测试备忘录: https://t.co/joUS0jcCoG"
-

[ Network ] The Network Capture Playbook (Part 5) : https://blog.packet-foo.com/2016/12/the-network-capture-playbook-part-5-network-tap-basics/ , 4 : https://blog.packet-foo.com/2016/11/the-network-capture-playbook-part-4-span-port-in-depth/ , 3 :… https://twitter.com/i/web/status/808615882058448896
"The Network Capture Playbook(part 5): 网络 TAP 设备基础: https://t.co/04BYvQUsbh"
-

[ Others ] I just published a new blog about "Using MBAE To Disable MBAE, and Subverting ASLR/DEP" http://reveralabs.com/2016/11/using-mbae-to-disable-mbae-and.html
"Using MBAE To Disable MBAE, and Subverting ASLR/DEP: https://t.co/Q0SIk9YUMl"
-

[ Others ] #PatchTuesday - #Security updates available for #Adobe #Flash Player: https://adobe.ly/2guYZfA
"Adobe 12 月安全公告︰ https://t.co/c672wqy9hb"
-

[ Popular Software ] SQL injection in Joomla extension DT Register https://goo.gl/fb/z5Q66H #FullDisclosure
" Joomla extension DT 寄存器存在 SQL 注入漏洞: https://t.co/jYelocnqAx "
-

[ Popular Software ] [blog] Word Up! Microsoft Word OneTableDocumentStream Underflow http://srcincite.io/blog/2016/12/13/word-up-microsoft-word-onetabledocumentstream-underflow.html … Analysis of CVE-2016-7290 / MS16-148 #research #0d
"Microsoft Word OneTableDocumentStream 整数下溢漏洞分析(CVE-2016-7290): http://srcincite.io/blog/2016/12/13/word-up-microsoft-word-onetabledocumentstream-underflow.html "
-

[ Popular Software ] How to Protect Against OpenSSL 1.1.0a Vulnerability CVE-2016-6309 https://securingtomorrow.mcafee.com/mcafee-labs/how-to-protect-against-openssl-1-1-0a-vulnerability-cve-2016-6309/
"针对 OpenSSL 1.1.0a CVE-2016-6309 的漏洞分析: https://t.co/iMUY29SR3t"
-

[ SecurityReport ] 12 Bulletins fixing 47 CVEs released by #Microsoft. Analysis of those plus 9 from #Adobe coming soon. https://t.co/D7UV0eB75s
"Microsoft 12月安全公告发布,修复了 47 个 CVE 漏洞: https://t.co/D7UV0eB75s"
-

[ Tools ] Free tool from @ facebook checks public #CTlogs for issues with certs. https://threatpost.com/facebook-releases-free-certificate-transparency-monitoring-tool/122433/ via @ threatpost
"facebook 发布了免费的 Certificate Transparency 监视工具: https://t.co/Ngi7B5Tuws"
-

[ Tools ] For Windows64 memory analysis. Native types reflected into Python. Nested hypervsior support etc... https://github.com/ShaneK2/inVtero.net/blob/master/quickdumps/publish.zip
"可用于 dump 内存并自动化分析的工具: https://t.co/72uid6idph"
-

[ Vulnerability ] PHP 7.0.13 Use After Free unserialize() PoC https://cxsecurity.com/issue/WLB-2016120073
"PHP 7.0.13 UAF unserialize() PoC(CVE-2016-9936): https://t.co/49I8VlLp6T"
-

[ Windows ] @hosselot My new writeup (Ms16-147, CVE-2016-7274) Remote gdi32full.dll memory corruption in Windows 10 and below: https://t.co/fTeKIv3Iqm
"Windows LoadUvsTable() 函数堆溢出漏洞细节(CVE-2016-7274)︰ https://t.co/fTeKIv3Iqm"
-
[ Tools ] iOSSecAudit:一个iOS APP安全审计工具: http://www.freebuf.com/sectool/122512.html#0-tsina-1-78051-397232819ff9a47a7b7e80a40613cfe1
-
[ Hardware ] 最新盗窃手法:ETC里的钱竟被POS机隔空刷光,专家已确认: http://www.leiphone.com/news/201612/MduSJvFZQpaGwo9N.html
 Xuanwu Spider via Freebuf
Xuanwu Spider via Freebuf