
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] HackingTeam's Android implant analysis: http://rednaga.io/2016/11/14/hackingteam_back_for_your_androids/ by @ RedNagaSec
"HackingTeam 的 Android 后门组件分析: https://t.co/zsRISOUnUB"
-

[ Android ] December Android Security Bulletin: https://source.android.com/security/bulletin/2016-12-01.html. It's also the stable release of 7.1.1, which is the first Nexus 7.1.x release.
"Android 12 月安全公告, DirtyCow 漏洞被修复︰ https://t.co/uEQ0IcVugo"
-

[ Browser ] Multiple Universal XSS fixed in latest Chrome 55 : https://googlechromereleases.blogspot.in/2016/12/stable-channel-update-for-desktop.html
"最新 Chrome 55 中被修复的漏洞们: https://t.co/Rv6z0k8k22"
-

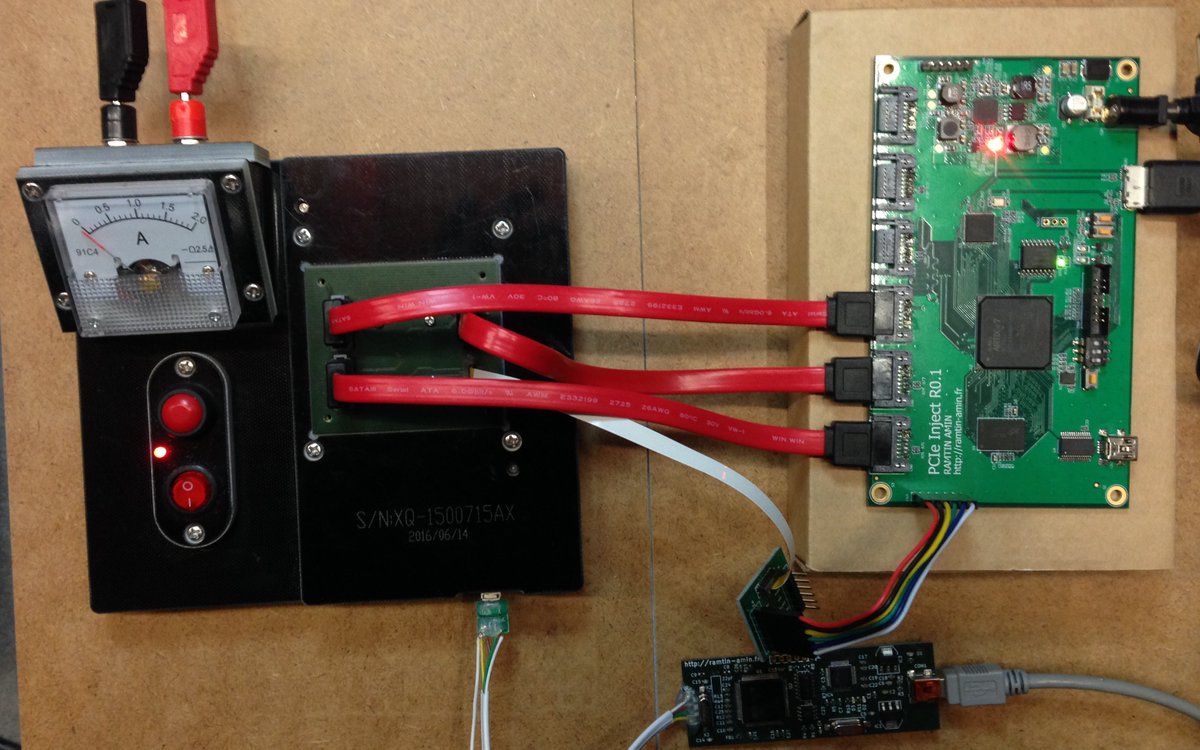
[ Firmware ] iPhone secure boot firmware component could be dumped. http://ramtin-amin.fr/#nvmedma https://t.co/ORUrGbTRtF
"提取 iPhone 6s Secure ROM: http://ramtin-amin.fr/#nvmedma"
-

[ Fuzzing ] An introduction of Use-After-Free detection in binary code by #static analysis - http://blog.amossys.fr/intro-to-use-after-free-detection.html #uaf
"在二进制代码中通过静态分析的方法检测 UAF 漏洞: https://t.co/ulcgwGkRI7"
-

[ Linux ] [1day] [PoC with $rip] Deterministic Linux heap grooming with huge allocations http://scarybeastsecurity.blogspot.com/2016/12/1day-poc-with-rip-deterministic-linux.html
"[1day] [PoC with $rip] Deterministic Linux heap grooming with huge allocations : https://t.co/jEcDe6lNk1"
-

[ MalwareAnalysis ] Cerber 5.0.1 Arrives with New Multithreading Method http://blog.fortinet.com/2016/12/02/cerber-5-0-1-arrives-with-new-multithreading-method
"病毒 Cerber 5.0.1 使用新多线程方法来袭: https://t.co/RJe1TT7GLE"
-

[ Others ] Data breach at the Japanese Shiseido, 420,000 users’ records exposed http://securityaffairs.co/wordpress/54075/data-breach/shiseido-data-breach.html
"日本化妆品巨头资生堂 42 万用户数据遭泄露: https://t.co/UYln7iMbvD"
-

[ Others ] New Blog Post - Evidence of Attackers’ Development Environment Left in Shortcut Files ^ST http://blog.jpcert.or.jp/2016/12/evidence-of-att-3388.html
"快捷方式文件中泄露的攻击者开发环境信息可以帮助溯源攻击者: https://t.co/3FAAYaIGSd"
-

[ Pentest ] PentestBox : An Opensource PreConfigured Portable Pen Testing Environment for the Windows : https://pentestbox.org/#download cc @ exploitprotocol
"PentestBox 是一款 Windows 平台下预配置的便携式开源渗透测试环境: https://t.co/RdkcOtMpgO "
-

[ Pentest ] Backslash Powered Scanning: Hunting Unknown Vulnerability Classes http://blog.portswigger.net/2016/11/backslash-powered-scanning-hunting.html
"backslash -- 一款强力扫描器,此篇文章是对扫描器的特性进行详细介绍: https://t.co/zkoAWhlDJn"
-

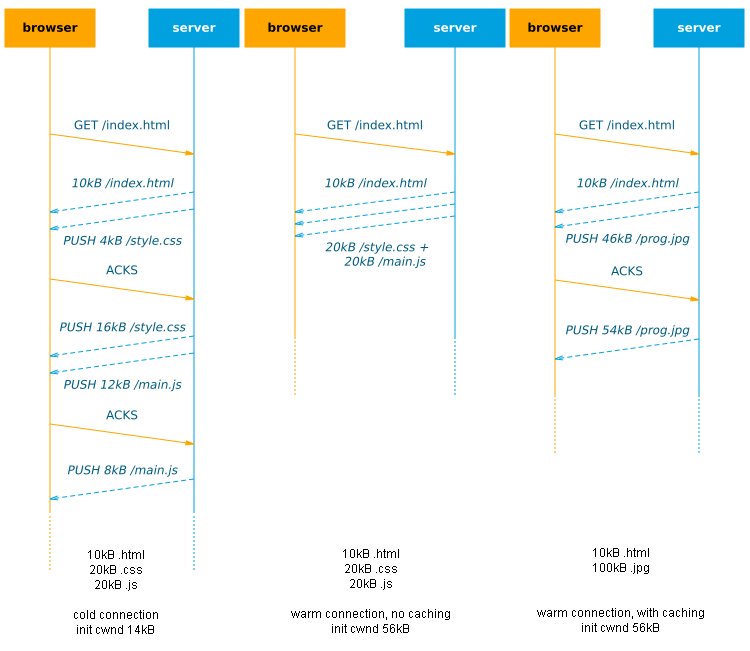
[ Protocol ] HTTP/2 Push : The details : http://calendar.perfplanet.com/2016/http2-push-the-details/ https://t.co/HHJDW5HqPe
"HTTP/2 Push 实现细节︰ https://t.co/6YIpQU5fnS "
-

[ Tools ] Results from the 2016 Volatility Plugin Contest are in! https://volatility-labs.blogspot.ru/2016/12/results-from-2016-volatility-plugin.html
"2016 年度 Volatility 插件大赏: https://t.co/tlyVWMehwn"
-

[ Tools ] PowerForensics All in one platform for live disk #forensic analysis in #PowerShell Author: @jaredcatkinson https://t.co/tDJKScn0O0
"PowerForensics 是一个硬盘驱动取证分析框架,目前支持 NTFS 和 FAT 文件系统: https://t.co/tDJKScn0O0"
-

[ Vulnerability ] [local] - Apache CouchDB 2.0.0 - Local Privilege Escalation https://www.exploit-db.com/exploits/40865/
"Apache CouchDB 2.0.0 本地提权漏洞: https://t.co/OG1BnS9eRT"
-

[ Web Security ] CVE-2016-8740, Server memory can be exhausted and service denied when HTTP… https://goo.gl/fb/medG1g #FullDisclosure
"CVE-2016-8740 Apache HTTPD web server: https://t.co/UZQSxA0NmV "
-

[ Windows ] Microsoft MSINFO32.EXE ".NFO" Files XML External Entity https://goo.gl/fb/LzXWvW #FullDisclosure
"Microsoft MSINFO32.EXE ".NFO" Files XML 外部实体攻击 : https://t.co/Wi8cuYPcro "
-

[ Windows ] Microsoft Event Viewer v1.0 XML External Entity https://goo.gl/fb/Cwqc7N #FullDisclosure
"Microsoft 事件查看器 v1.0 XML 外部实体攻击: https://t.co/c4oCGhmF09"
-

[ WirelessSecurity ] Reversing Mobile Traffic Lights: https://www.bastibl.net/traffic-lights/ https://www.bastibl.net/traffic-lights-2/ #sdr #wireless #security
"逆向移动交通信号灯︰ https://t.co/iIIj1aoBaB https://t.co/1x0asdi3D4 "
-
[ Vulnerability ] 高通辅助GPS数据存在不安全传输:http://seclists.org/fulldisclosure/2016/Dec/19?utm_source=feedburner&utm_medium=twitter&utm_campaign=Feed%3A+seclists%2FFullDisclosure+%28Full+Disclosure%29
-
[ Browser ] (CVE-2016-9079)Firefox 远程代码执行漏洞技术分析与防护方案: http://blog.nsfocus.net/analysis-protection-firefox-vulnerability/
-
[ Bug Bounty ] Mitigation Bypass and Bounty for Defense Terms(微软的缓解措施 Bounty 项目更新,RFG、CFG、ACG 等新保护特性也在奖励范围内,最高奖金 10 万美元): https://technet.microsoft.com/en-us/security/dn425049.aspx
-
[ Browser ] (CVE-2016-3377)Win10 Edge 浏览器从越界写到任意内存读写: http://www.freebuf.com/articles/system/121690.html
 Xuanwu Spider via Full Disclosure
Xuanwu Spider via Full Disclosure