
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Just published a new blog post! Using Android's ashmem to escalate privileges from any context. As always, exploits… https://twitter.com/i/web/status/804373455189766144
"BitUnmap: 攻击 Android 匿名共享内存(Ashmem) : https://googleprojectzero.blogspot.com/2016/12/bitunmap-attacking-android-ashmem.html"
-

[ Android ] Analysis of multiple vulnerabilities in AirDroid https://shar.es/18cttj by @ evilsocket
" Android AirDroid 的多个漏洞分析: https://t.co/TpoNIvyhmz "
-

[ Attack ] Our research projects that machine learning will be key tool for socially engineered hacks in 2017… https://twitter.com/i/web/status/804189312216690690
"McAfee 表示 2017 年机器学习将会是社会工程的一把利器: https://t.co/XBzZVJdT9G"
-

[ Browser ] MSEdge XSS Filter bypass: <embed/:script allowscriptaccess=always src=//l0.cm/xss.swf> https://vulnerabledoma.in/char_test?body=%3Cembed/:script%20allowscriptaccess=always%20src=//l0.cm/xss.swf%3E
"绕过 MSEdge 浏览器 XSS Filter︰ <embed/:script allowscriptaccess=always src=//l0.cm/xss.swf>: https://t.co/BOFGxNft3v"
-

[ Fuzzing ] Google Open Source Blog: Announcing OSS-Fuzz: Continuous fuzzing for open source software https://opensource.googleblog.com/2016/12/announcing-oss-fuzz-continuous-fuzzing.html via @ google
"Google 开源新 Fuzz 工具 OSS-Fuzz ,用来 Fuzz 开源软件: https://t.co/KfhDKHLoZC"
-

[ IoTDevice ] On the (in)security of the Latest Generation Implantable Cardiac Defibrillators and How to Secure Them (pdf) https://t.co/6flMfZrusK
"如何保障新一代的植入式心律去顫器的安全 (PDF): https://t.co/6flMfZrusK"
-

[ Malware ] New post: New SmsSecurity Variant Roots Phones, Abuses Accessibility Features and TeamViewer http://bit.ly/2gBzgDx @ TrendMicro
"SmsSecurity 变种滥用 Android 辅助功能,同时能够利用 TeamViewer 进行远程访问: https://t.co/Cx1KsX8KK3"
-

[ MalwareAnalysis ] Malicious Document Analysis – Macro to Shellcode : https://bittherapy.net/malicious-document-analysis-macro-to-shellcode/
"恶意文档分析 — — 从宏到 shellcode︰ https://t.co/keCUnz95r8"
-

[ Others ] Patch for #0day vulnerability in Firefox is now available. Manual patch available here: https://www.mozilla.org/en-US/firefox/new/
"Firefox 0day 已修复,点击链接手动更新︰ https://t.co/sRCNEb0l6U"
-

[ Others ] Decrypting http://ASP.NET 4.5 https://lowleveldesign.wordpress.com/2016/11/30/decrypting-asp-net-4-5/
"解密 ASP.NET 4.5 ,文章内容包括解密 ASP.NET Identity cookie 以及密钥的计算: https://t.co/jHcwRI0t7x"
-

[ Popular Software ] FreePBX 13 : From Cross-Site Scripting to Remote Command Execution : https://blog.ripstech.com/2016/freepbx-from-cross-site-scripting-to-remote-command-execution/
"FreePBX 13︰ 从跨站点脚本攻击到远程命令执行︰ https://t.co/CnmrOAKINg"
-

[ Popular Software ] Omnivista 8770 Unauthenticated Remote Code Execution : http://blog.malerisch.net/2016/12/alcatel-omnivista-8770-unauth-rce-giop-corba.html , Github : https://github.com/malerisch/omnivista-8770-unauth-rce cc @ malerisch
"Omnivista 8770 未认证的远程代码执行︰ http://blog.malerisch.net/2016/12/alcatel-omnivista-8770-unauth-rce-giop-corba.html Github: https://github.com/malerisch/omnivista-8770-unauth-rce "
-

[ Tools ] Use SAMRi10 to harden remote access to the SAM in Windows 10/2016 by @TalBeerySec @ItaiGrady #infosec #DFIR https://t.co/Plw0viB89k
"SAMRi10 -- 可用在 Windows 10/2016 中强化 SAM 远程访问: https://t.co/Plw0viB89k"
-

[ Tools ] The a Event Viewer UAC bypass module just landed in master. Thanks again to @enigma0x3 for the effort! https://t.co/YsHSzNeE9O
"metasploit framework 新增加了 Event Viewer UAC 绕过模块: https://t.co/YsHSzNeE9O"
-

[ Tools ] DOMFf : DOM forensics framework (Python based) : https://github.com/graniet/DOMFf cc @ graniet75
"DOMFf -- 基于 Python 的 DOM 取证框架,可从网站中提取所有 DOM 数据: https://t.co/PeBQ8quXsz"
-

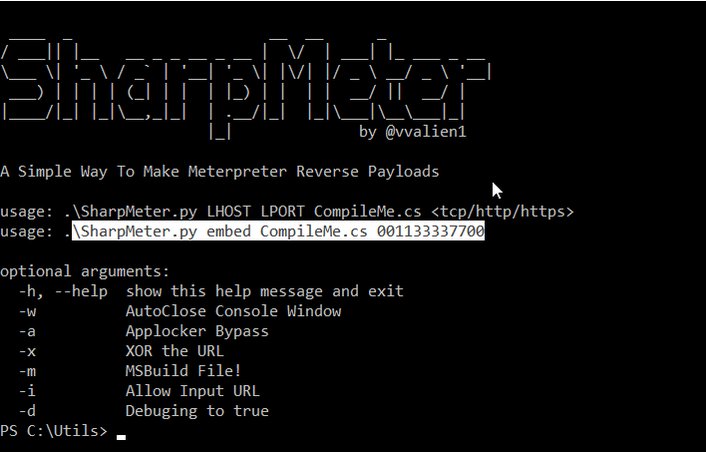
[ Tools ] Running shellcode inside msbuild... https://github.com/vvalien/SharpMeter https://t.co/Dg6oVdWlJX
"SharpMeter -- 用于生成 Meterpreter 反弹 shell 的工具,同时可绕过一些白名单限制: https://github.com/vvalien/SharpMeter"
-

[ Vulnerability ] No post-turkey naps for us. 37 new 0-days disclosed to vendors (Adobe/Foxit/ThinPrint/HPE/MSFT) this week. #whew http://bit.ly/2h08LLr
"ZDI 披漏了 37 个 漏洞 : https://t.co/qJbFWv087H"
-

[ Web Security ] HTTP/2 : In-depth analysis of the top four flaws of the next generation web protocol : https://www.imperva.com/docs/Imperva_HII_HTTP2.pdf (pdf)
"HTTP/2︰ 深入分析下一代 web 协议的四大缺陷(PDF)︰ https://t.co/XlAYkdQFs6 "
-

[ Web Security ] Bypassing CSP using polyglot JPEGs : http://blog.portswigger.net/2016/12/bypassing-csp-using-polyglot-jpegs.html cc: @ garethheyes
"利用精心构造的 JPEG 绕过 CSP: https://t.co/YbcFrWXwpU"
-

[ Windows ] Microsoft Windows Limited Bypass Of Traverse Permissions In Kernel Object Manager https://packetstormsecurity.com/files/139974/GS20161201163955.tgz
"Microsoft Windows Limited Bypass Of Traverse Permissions In Kernel Object Manager: https://bugs.chromium.org/p/project-zero/issues/detail?id=206"
-

[ Windows ] FuzzySec -> Windows Kernel Exploitation: Stack Overflow - http://www.fuzzysecurity.com/tutorials/expDev/14.html
"Windows 内核利用之栈溢出: https://t.co/xtpj0oWJFv 该网站中还有其它相关技术教程: http://www.fuzzysecurity.com/tutorials.html"
-

[ WirelessSecurity ] OpenBTS Application Suite Release 4.0 User Manual [PDF] http://openbts.org/site/wp-content/uploads/2014/07/OpenBTS-4.0-Manual.pdf #GnuRadio #SDR #GSM https://t.co/rVpOiQvOko
"OpenBTS 应用套件 4.0 版用户手册(PDF): https://t.co/xeLveIN8k3"

 Xuanwu Spider via Freebuf
Xuanwu Spider via Freebuf