
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Firmware ] Our slides "UEFI Firmware Rootkits: Myths and Reality" with @ vxradius. Revisited and Updated version for #ZeroNights https://github.com/REhints/Publications/blob/master/Conferences/ZeroNights_2016/UEFI_Rootkits_ZN_2016.pdf
"UEFI Firmware Rootkits: Myths and Reality(slides): https://t.co/yEPKBYYuBT"
-

[ Hardware ] Tenda, Dlink & Tplink TD-W8961ND - DHCP XSS Vulnerability https://goo.gl/fb/8ygS5p #FullDisclosure
"Tenda, Dlink & Tplink TD-W8961ND - DHCP XSS 漏洞: https://t.co/wOx57b9olu "
-

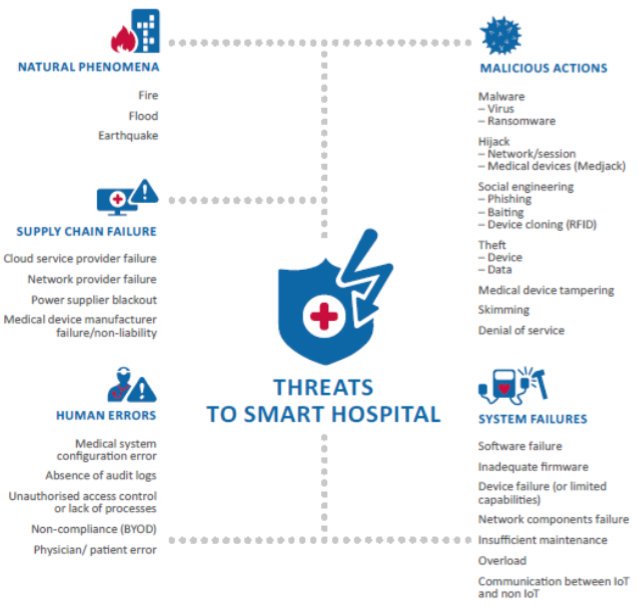
[ IoTDevice ] Protecting smart hospitals: A few recommendations - http://bit.ly/2gB6WS3 - @ enisa_eu #EU https://t.co/yOzeFSQJpb
-

[ Linux ] Linux ntpd 4.2.8 derive_nonce Stack Overflow https://packetstormsecurity.com/files/139900/ntp-sof.pl.txt
"Linux ntpd 4.2.8 derive_nonce 栈溢出 poc: https://t.co/aR7aVN3XwW"
-

[ Linux ] Using CHIPSEC with Kali Linux: https://github.com/chipsec/chipsec/wiki/Using-CHIPSEC-with-Kali-Linux
"在 Kali Linux 下安装平台安全框架 CHIPSEC 的方法: https://t.co/ucENUH2TxD"
-

[ Malware ] A New All-in-One Botnet : Proteus http://blog.fortinet.com/2016/11/28/a-new-all-in-one-botnet-proteus
"Fortinet 近日发现了一个多功能的僵尸网络︰ Proteus: https://t.co/PUh2qGZP3p"
-

[ Others ] Database of a complete X86/X64 instruction set. http://buff.ly/2g4Rmjz
"一个完整的 X86/X 64 指令集数据库: https://t.co/T4TKmR4ApV"
-

[ Others ] #osdi Kraken: Live traffic tests to identify & resolve resource utilization bottlenecks in web svcs by @adriancolyer https://t.co/erVPELsYpL
"利用实时流量测试来识别和解决大规模Web服务中的资源利用率瓶颈: https://t.co/erVPELsYpL"
-

[ Others ] Oooops.... incorrect fix for my FLIC exploit. So a new post: [0day] [PoC] Incorrect fix for gstreamer FLIC decoder: https://t.co/8XA3xFL4Pt
"由于错误修复 gstreamer FLIC decoder 所带来的新漏洞︰ https://t.co/8XA3xFL4Pt"
-

[ Others ] Egg Hunter - Twist in Buffer Overflow - BisonWare FTP Server v3.5 http://hacksys.vfreaks.com/research/egg-hunter-twist-in-buffer-overflow-bisonware-ftp-server-v3-5.html vía @ HackSysTeam
"Egg Hunter – Twist in Buffer Overflow – BisonWare FTP Server v3.5: https://t.co/dQUaoPeFZs"
-

[ Others ] All your Paypal OAuth tokens belong to me - localhost for the win http://blog.intothesymmetry.com/2016/11/all-your-paypal-tokens-belong-to-me.html
"Paypal OAuth token 劫持: https://t.co/Z7KtDPRi5I"
-

[ Others ] New post by @ 0vercl0k "Token Capture via an Llvm-based Analysis Pass" https://doar-e.github.io/blog/2016/11/27/clang-and-passes/
"以 Fuzzing 为目的,基于 LLVM pass 实现的 token finder: https://t.co/9Fsk6cETuY"
-

[ Others ] Code Integrity on Nano Server: Tips/Gotchas http://www.exploit-monday.com/2016/11/Nano-Server-Code-Integrity.html
"Nano Server 上的代码完整性︰ 提示/陷阱: https://t.co/idhM2FE9el"
-

[ Protocol ] Analysis of OpenSSL ChaCha20-Poly1305 Heap Buffer Overflow (CVE-2016-7054) https://blog.fortinet.com/2016/11/23/analysis-of-openssl-chacha20-poly1305-heap-buffer-overflow-cve-2016-7054
"OpenSSL ChaCha20 Poly1305 堆缓冲区溢出漏洞分析 (CVE-2016-7054): https://t.co/ZIVNTZvU4m "
-

[ ReverseEngineering ] An analysis walkthrough for the latest macros used by #HANCITOR #malware to load shellcode directly into memory: https://t.co/1ahBGSFjZW
"Analysing the Hancitor Maldoc︰ https://t.co/1ahBGSFjZW"
-

[ Tools ] libfuzzer-workshop - Repository for materials of "Modern fuzzing of C/C++ Projects" workshop. https://github.com/dor1s/libfuzzer-workshop
" 'Modern fuzzing of C/C++ Projects' 研讨会材料,来自 ZeroNights 2016 大会: https://t.co/gJKB7EKu7Z"
-

[ Tools ] My small tool for converting #PE files dumped from the memory into their raw form: https://github.com/hasherezade/malware_analysis/tree/master/pe_unmapper https://t.co/d1Jv3ulAl5
"pe_unmapper -- 可将 PE 文件执行后分配的虚拟内存还原成可执行文件的小工具︰ https://github.com/hasherezade/malware_analysis/tree/master/pe_unmapper"
-

[ Tools ] New blog post "Update: xor-kpa.py Version 0.0.4" https://blog.didierstevens.com/2016/11/27/update-xor-kpa-py-version-0-0-4/
"xor-kpa.py Version 0.0.4 发布更新: https://t.co/kzrbs4P7BX"
-

[ Tools ] Another nice tool from Intel use Capstone: SATT to trace & analyze Linux process on Intel Processor Trace hardware. https://t.co/LL82FWsSL6
"SATT Software Analyze Trace Tool: https://t.co/LL82FWsSL6"
-

[ Vulnerability ] Full exploit of CVE-2016-6754(BadKernel) and slide of @ SyScan360 2016 shanghai <BadKernel: exploit V8 with a typo> https://github.com/secmob/BadKernel
"BadKernel --- exploit V8 with a typo, 来自 SyScan360 2016 大会: https://t.co/gzdvmDvHJt"
-

[ Vulnerability ] Schoolhos CMS v2.29 - userberita SQL injection Vulnerability https://goo.gl/fb/bRvmNm #FullDisclosure
"学校内容管理系统 Schoolhos CMS v2.29-userberita SQL 注入漏洞(含 PoC): https://t.co/2bOAzz2tSL"
 Xuanwu Spider via 阿里聚安全
Xuanwu Spider via 阿里聚安全