
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] I wrote up some thoughts on what I view as the limitations of Android N's new device encryption: https://t.co/MSma9g8gPP
" Android N 加密的局限性︰ https://t.co/MSma9g8gPP"
-

[ Attack ] Practical Phishing Automation with PhishLulz : http://www.slideshare.net/micheleorru2/practical-phishing-automation-with-phishlulz-kiwicon-x (Slides) cc @ antisnatchor
"利用自动化钓鱼框架 PhishLulz 进行钓鱼实战,来自 KiwiCon 2016 大会议题: https://t.co/MMGhDIfZ3p "
-

[ Industry News ] We expand our Android #0day acquisitions (RCE or LPE) from the usual Samsung/Google/Sony to other devices: Huawei, Lenovo, Xiaomi, Oppo, HTC
"Zerodium 开始收购国产 Android 手机 0day,包括: 华为、 联想、 小米、 Oppo、 HTC"
-

[ IoTDevice ] Get started with Zigbee security analysis and setting up a vulnerable Zigbee lab with this blog post - http://blog.attify.com/2016/11/23/zigbee-security-exploitation-iot-devices/
"Zigbee 的安全性与 IoT 设备的漏洞利用: https://t.co/sTWVTpwcyg"
-

[ Linux ] Linux Kernel 2.6.32-642 / 3.16.0-4 'inode' Integer Overflow PoC https://cxsecurity.com/issue/WLB-2016110205
"Linux Kernel 2.6.32-642 / 3.16.0-4 'inode' 整数溢出漏洞 PoC : https://t.co/12dC50qXMk"
-

[ Linux ] Wget < 1.18 Access List Bypass / Race Condition Vuln. Exploit : https://legalhackers.com/advisories/Wget-Exploit-ACL-bypass-RaceCond-CVE-2016-7098.html
"GNU Wget < 1.18 条件竞争漏洞(含 PoC)︰ https://t.co/sdzDcW997m"
-

[ Linux ] Possible Integer Overflow in Kernel Linux - IPV4 - ip_tunnel.c http://bit.ly/2fbF4X6 http://bit.ly/2fvfDP3 #kernel #linux #infosec
"Kernel Linux - IPV4 - ip_tunnel.c Integer Overflow: https://t.co/w3midmwOEj https://t.co/Tm0If0tU0Y "
-

[ Malware ] Gatak #malware "In 62% of incidents, lateral movement across the victim’s network occurs within 2hrs of infection,” https://t.co/Br2UhOjL6t
"医疗行业成为 Gatak 木马主要目标: https://t.co/Br2UhOjL6t"
-

[ Others ] Command Injection/Elevation – Environment Variables Revisited https://breakingmalware.com/vulnerabilities/command-injection-and-elevation-environment-variables-revisited/
"代码注入/提权 – 再谈环境变量: https://t.co/EuC8MXUYZ6"
-

[ Others ] KASLRfinder writeup: Windows 10 KASLR recovery with TSX http://blog.frizk.net/2016/11/windows-10-kaslr-recovery-with-tsx.html
"利用 TSX 突破 Windows 10 KASLR : https://t.co/wfEO6V4kiM"
-

[ Others ] Derandomizing latest Windows 10 Kernel (CVE-2016-7255 exploit): https://github.com/IOActive/I-know-where-your-page-lives ,Slides : https://github.com/IOActive/I-know-where-your-page-lives/blob/master/I%20Know%20Where%20Your%20Page%20Lives%20-%20De-Randomizing%20the%20Latest%20Windows%2010%20Kernel.pdf cc @ kiqueNissim
"利用 CVE-2016-7255 攻破 Windows 10 Kernel ASL︰ https://t.co/MVdEfTEib7 ,此利用来自 ZeroNights 2016 大会议题:I Know Where Your Page Lives - De-Randomizing the Latest Windows 10 Kernel(slides)︰ https://t.co/hnaOWHg2WK "
-

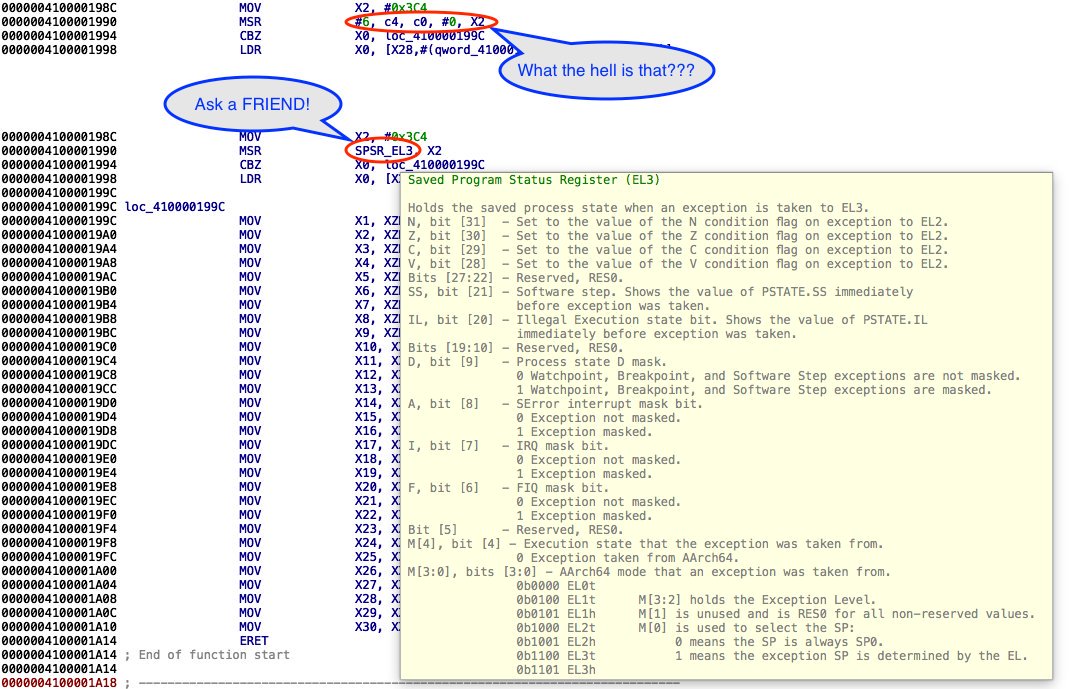
[ Tools ] FRIEND - Flexible Register/Instruction Extender aNd Documentation : https://github.com/alexhude/FRIEND cc @ getorix https://t.co/bbozelo4Xy
"FRIEND -- 一个灵巧的寄存器/指令文档 IDA 插件: https://github.com/alexhude/FRIEND"
-

[ Tools ] unlinker - A program for extracting functions from a PE file for later reuse https://github.com/jonwil/unlinker
"unlinker -- rip functions out of Visual C++ compiled binaries and produce Visual C++ COFF object files: https://t.co/G8Ssn1Ntu6 "
-

[ Tools ] xAnalyzer Reviewed by @ yunietps http://x64dbg.com/blog/2016/11/24/xanalyzer-reviewed.html #x64dbg #blog #infosec
"x64dbg xAnalyzer Reviewed: https://t.co/IeReQJ6VuA "
 Xuanwu Spider via seebug
Xuanwu Spider via seebug