
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Escape compilation technology - http://blogs.360.cn/360mobile/2016/10/24/android_escape/ (Chinese)
" Android逃逸技术汇编: https://t.co/rppWIJjEAv "
-

[ Android ] #Rowhammer vulnerability comes to #Android - http://bit.ly/2enXxOV
" 利用 Rowhammer 漏洞在 Android 系统上实现 Root 提权,来自 Threatpost 的报道: https://t.co/ZoFFYKdkhU ; 技术细节: https://www.vusec.net/projects/drammer/ ; https://vvdveen.com/publications/drammer.pdf ; https://github.com/vusec/drammer "
-

[ Android ] DRAMMER - Deterministic Rowhammer privilege escalation on Android https://www.vusec.net/projects/drammer/
"Drammer: flip feng shui gose mobileflip: https://t.co/f8FYlzbzsW "
-

[ iOS ] iOS 10.1 security fixes: https://support.apple.com/en-us/HT207271
"iOS 发布 10.1 版本,本次更新的补丁公告︰ https://t.co/Z8JfZa98oI macOS Sierra 10.12.1 版本的补丁公告: https://support.apple.com/kb/HT207275 Safari 10.0.1: https://support.apple.com/kb/HT207272 "
-

[ IoTDevice ] Chinese manufacturer recalls #IOT gear following @ Dyn #DDoSAttack - http://bit.ly/2eLPeKU #Xiongmai
"中国制造商雄迈决定召回其在美国地区销售的摄像头,原因是这些摄像头被漏洞利用并参与针对 Dyn 的 DDoS 攻击: https://t.co/qSVyVFRicu "
-

[ Linux ] Capturing Packets in Linux at a Speed of Millions of Packets per Second without Using Third Party Libraries - http://kukuruku.co/hub/nix/capturing-packets-in-linux-at-a-speed-of-millions-of-packets-per-second-without-using-third-party-libraries
"不借助第三方库来实现每秒捕获百万个 Linux 数据包: https://t.co/pQfSlG6XLA"
-

[ macOS ] Apple macOS 10.12.1/iOS 10 SecureTransport SSL handshake OCSP MiTM and DoS https://goo.gl/fb/ogrhHH #FullDisclosure
"Apple macOS 10.12.1/iOS 10 SecureTransport SSL handshake OCSP MiTM and DoS: http://seclists.org/fulldisclosure/2016/Oct/86?utm_source=feedburner&utm_medium=twitter&utm_campaign=Feed%3A+seclists%2FFullDisclosure+%28Full+Disclosure%29"
-

[ macOS ] How to detect malicious activities on your Mac OS X system with system logs and grep, sort, awk: http://sud0man.blogspot.fr/2016/10/new-version-of-checkout4mac-02.html #macosx #forensics
"一款检测 Mac OS X 系统上安全隐患的工具︰ https://t.co/ljl89Po5Zd #macosx #forensics"
-

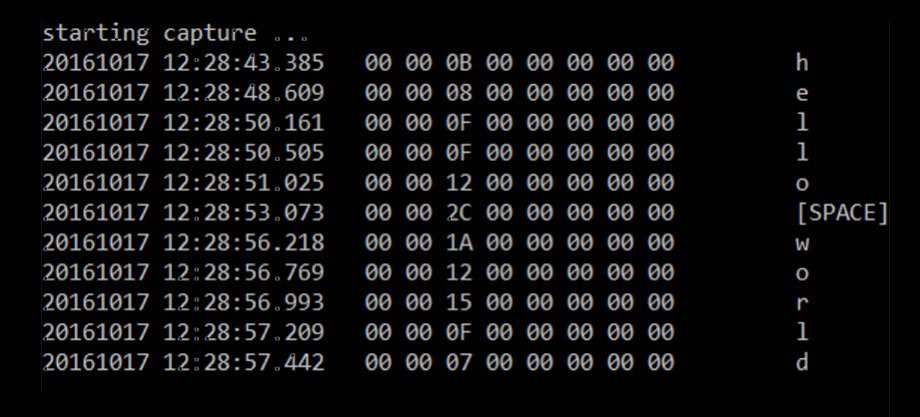
[ Malware ] New Keylogging Method: Event Tracing for Windows (ETW): https://www.cyberpointllc.com/srt/posts/srt-logging-keystrokes-with-event-tracing-for-windows-etw.html https://t.co/CaRksq7BVp
"利用Windows 事件追踪(ETW)来进行键盘记录: https://t.co/r9zng5cOiX https://t.co/CaRksq7BVp"
-

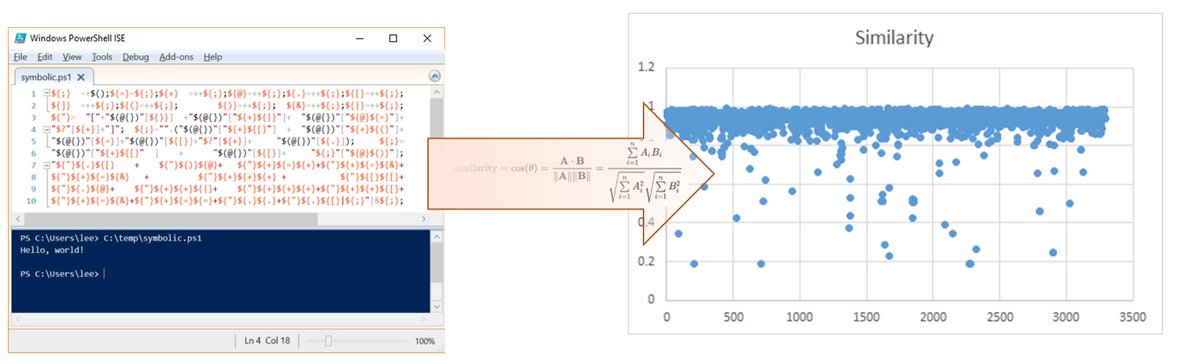
[ Obfuscation ] Neat post by @ Lee_Holmes on using #PowerShell to find obfuscated Powershell with math :) http://www.leeholmes.com/blog/2016/10/22/more-detecting-obfuscated-powershell/ https://t.co/ruLNL5lg8x
"利用 PowerShell 的 tokenizer 检测被混淆的 PowerShell : https://t.co/p3oV5KfSwb https://t.co/ruLNL5lg8x "
-

[ Tools ] Intel Engine Firmware Analysis Tool: MEAnalyzer https://n0where.net/intel-engine-firmware-analysis-tool-meanalyzer/ #InfoSec #CyberSecurity
"一款英特尔引擎固件分析工具 -- MEAnalyzer: https://t.co/G8TXrNQF6x "
-

[ Tools ] Introducing Birdwatcher: A data analysis and #OSINT framework for Twitter. http://michenriksen.com/blog/birdwatcher-twitter-osint-framework/
"Birdwatcher -- 一款用于对 Twitter 进行数据分析的工具: https://t.co/UkhbjE2scL"
-

[ Tools ] Using WinDBG to tap into JavaScript and help with deobfuscation and browser exploit detection - https://lnkd.in/eCqgx5s
"使用 WinDBG 调试器辅助检测 JavaScript 恶意代码以及浏览器 Exploit: https://t.co/sRpen4RaD2"
-

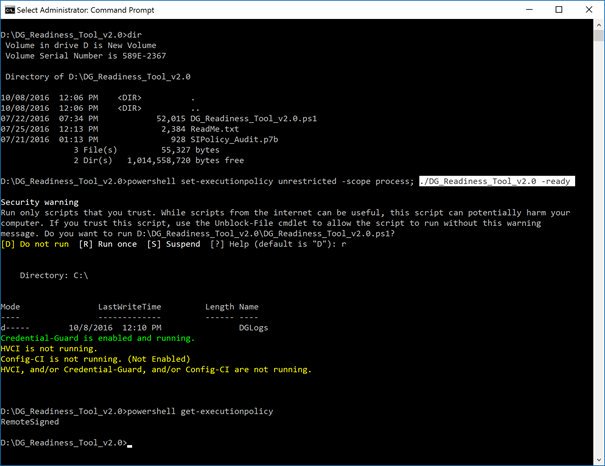
[ Windows ] Credential Guard Made Easy for Windows 10 Enterprise Version 1607 https://yungchou.wordpress.com/2016/10/10/credential-guard-made-easy-in-windows-10-version-1607 https://t.co/QQdmtPu9l8 https://t.co/YskxQSMzYc
"在 Windows 10 Enterprise Version 1607 版上配置 Credential Guard : https://t.co/O86K5mZFSj https://t.co/QQdmtPu9l8 https://t.co/YskxQSMzYc"
-
[ Challenges ] 打破结界之战:“机器特工挑战赛”和“极棒跨次元 CTF”:http://mp.weixin.qq.com/s?__biz=MzI0NDA5MDYyNA==&mid=2648256705&idx=1&sn=8a195bc99b02cc7883ee9b90585af21b&scene=1&srcid=0821g5KNq44VvdoZF5guFu7f
 Xuanwu Spider via GitHub
Xuanwu Spider via GitHub