
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Technical in-depth analysis of Sednit operation. https://twitter.com/nyx__o/status/789077774367535104
"ESET 安全研究人员对于网络间谍组织 Sednit 的分析研究: http://www.welivesecurity.com/2016/10/20/new-eset-research-paper-puts-sednit-under-the-microscope/"
-

[ Attack ] [Blog] Rotten Apples: Resurgence http://bddy.me/2ekkkve #phishing https://t.co/3YHBC0K3lo
"针对中国 Apple 用户的钓鱼活动再次复活: https://www.fireeye.com/blog/threat-research/2016/10/rotten_apples_resur.html"
-

[ Attack ] 3.2 million Indian debit cards compromised. Malware found on Hitachi Payment Services ATM network. http://economictimes.indiatimes.com/articleshow/54945561.cms
"印度320万信用卡数据泄漏,SBI、HDFC、ICICI、YES 和 Axis 银行用户均严重受其影响: http://economictimes.indiatimes.com/industry/banking/finance/banking/3-2-million-debit-cards-compromised-sbi-hdfc-bank-icici-yes-bank-and-axis-worst-hit/articleshow/54945561.cms"
-

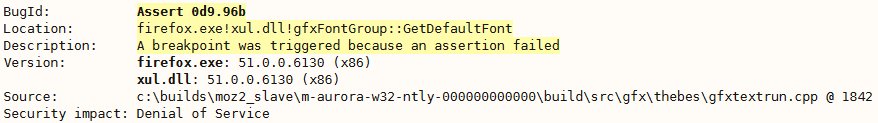
[ Browser ] #DailyBug #Firefox assert on x86 Windows https://bugzilla.mozilla.org/show_bug.cgi?id=1311612 https://t.co/zClvU1glZ9
"Assert in gfxFontGroup։։GetDefaultFont on x86: https://bugzilla.mozilla.org/show_bug.cgi?id=1311612"
-

[ Browser ] [Paper] Bypassing XSS Filters using XML internal entities http://www.davidlitchfield.com/BypassingXSSFiltersusingXMLInternalEntities.pdf
"利用 XML internal entities 绕过 Chrome 和 IE 浏览器的 XSS 过滤器: https://t.co/KANNEb09VB"
-

[ Browser ] A Study of WebRTC Security https://webrtc-security.github.io/
"WebRTC(Web Real-Time Communications) 技术的安全性研究: https://t.co/aHwT47VHus"
-

[ Conference ] Use-After-Use-After-Free (UAUAF), a novel & relatively universal exploit technique for UAF vulns in Flash #BHEU http://ow.ly/moaK305lMDs
" 下个月 4 号的 BlackHat Europe 会议上,有研究员会讲 UAUAF - 针对 Flash 的通用利用技术: https://t.co/zfIWn4khRt"
-

[ Crypto ] A. Jana, G. Paul, "Revisiting RC4 Key Collision: Faster Search Algorithm and New 22-byte Colliding Key Pairs" https://eprint.iacr.org/2016/1001
" RC4 密钥碰撞攻击,Paper: https://t.co/XZl8WIOCXt"
-

[ Hardware ] How to fool an ADC, part II or attacks against sigma-delta data converters by @ dark_k3y @ IOActive http://youtu.be/yzRJKzFl_ZA?a
" How to fool an ADC: https://t.co/g9DhEM7VKM"
-

[ IoTDevice ] .@ hardwear_io 2016 : Analyzing vehicle networks with CANToolz by Michael Elizarov. https://www.youtube.com/watch?v=FqrQUthne3k
"来自 2016 hardwear.io 大会的议题之一:使用 CANToolz 工具分析车联网: https://t.co/AjKg4ube5N"
-

[ Linux ] [BLOG] No Tears, No Fears: using #lkvm to provide invisible isolation http://blog.quarkslab.com/no-tears-no-fears.html
" 没有眼泪,也没有恐惧 - 利用 lkvm 提供透明隔离: https://t.co/p7tta278iA"
-

[ Linux ] Dirty COW (CVE-2016-5195) Linux Kernel privilege escalation vulnerability. https://t.co/Ql5ReZyZST
" Dirty COW(脏牛) (CVE-2016-5195) Linux 内核提权漏洞: http://dirtycow.ninja/ "
-

[ Linux ] The Linux COW bug is likely a Chrome/ChromeOS sandbox escape as well: https://cs.chromium.org/chromium/src/sandbox/linux/seccomp-bpf-helpers/baseline_policy.cc?l=176&dr=C
"Linux Dirty Cow 非常像 Chrome/ChromeOS 的一个沙箱逃逸漏洞︰ https://t.co/P3iWYojm7f"
-

[ Malware ] Short summary of my talk @ Day_Con_X / Dayton Security Summit on the Mirai Botnet Bot https://insinuator.net/2016/10/a-quick-insight-into-the-mirai-botnet/
"Mirar Botnet 的分析: https://insinuator.net/2016/10/a-quick-insight-into-the-mirai-botnet"
-

[ OpenSourceProject ] OpenSSH : Memory exhaustion issue http://cvsweb.openbsd.org/cgi-bin/cvsweb/src/usr.bin/ssh/kex.c?rev=1.127&content-type=text/x-cvsweb-markup #infosec #openssh #vulnerability
"OpenSSH 内存耗尽 Bug: https://t.co/CuZ4nMAjPg "
-

[ Others ] We just published @nwalsh_sec work! Great blog post and new @Burp_Suite Extension to detect SOME vulnerabilities https://t.co/xPU5bLkUbh
" 利用 BurpSuite 挖掘同源方法执行漏洞(Same Origin Method Execution): https://t.co/xPU5bLkUbh"
-

[ Others ] Windows Kernel Registry Hive loading: negative RtlMoveMemory size in nt!CmpCheckValueList https://bugs.chromium.org/p/project-zero/issues/detail?id=873
"Windows 内核注册表文件加载:nt!CmpCheckValueList 中的 RtlMoveMemory size 出现负值,来自 Project Zero: https://t.co/mJ7lyPNsLk"
-

[ Others ] We detail the modification of an app’s source code for bypass SSL pinning, checking for tampering protection, & mor… https://twitter.com/i/web/status/788971276706742272
"McAfee Blog 对《如何测试 Android APP 的安全性》Part 4 文章修改后的版本: https://blogs.mcafee.com/mcafee-labs/patching-android-binary/?utm_source=twitter&utm_campaign=Labs#sf39112482"
-

[ Popular Software ] Experts devised a method to capture keystrokes during Skype calls http://securityaffairs.co/wordpress/52493/breaking-news/skype-calls.html
"一组安全专家发现在 Skype 通话期间可捕获用户按键: https://t.co/hmzsi1wQ9W"
-

[ Popular Software ] Oracle fixed some of the issues discussed in "OLAP DML Injection" (http://www.davidlitchfield.com/OLAPDMLInjection.pdf) in Apr2016 but forgot to tell me (CVE-2016-0681)
"Oracle 修复了几个 'OLAP DML Injection' 类型的漏洞: https://t.co/ic3GUrlK2a "
-

[ Protocol ] New blog post: A journey into the depths of VoWiFi Security https://insinuator.net/2016/10/a-journey-into-the-depths-of-vowifi-security/
" Voice over WiFi (VoWiFi) 安全性分析: https://t.co/FIq6RsuO2w "
-

[ Web Security ] Slack Access Control Bypass ($9k) http://secalert.net/slack-security-bug-bounty.html
" Slack Bug Bounty 中一个 9000 刀的漏洞分析: https://t.co/NHm5zBZDsX"
-

[ Web Security ] https://sites.google.com/site/bughunteruniversity/best-reports/openredirectsthatmatter nice chained bug! #xss #openredirect #google #vrp #bugbounty
" 关于 Open redirects 的讨论,有人认为它不算漏洞,但它又可以辅助其他漏洞实现利用: https://t.co/ZwKjbuZxS0 "
-

[ Web Security ] Chaining queries to execute SQL as SYS from SQL injection in web apps built on eBusiness Suite http://www.davidlitchfield.com/oracle-apps-to-sys.pdf
"在甲骨文 eBusiness Suite 应用中以 sys 权限执行 SQL 语句的几种方法[paper]: http://www.davidlitchfield.com/oracle-apps-to-sys.pdf "
-

[ Web Security ] http://securityaffairs.co/wordpress/52468/hacking/jja-k2-filter-search-joomla.html
" Joomla ja-k2-filter-and-search 组件的 SQL 注入漏洞: https://t.co/vjn6sTBUyj"
-

[ Web Security ] Everything You Need to Know About Certificate Pinning : https://2016.appsec.eu/wp-content/uploads/2016/07/AppSecEU2016-John-Kozyrakis-Certificate-Pinning.pdf by @ ikoz
"来自2016 AppSecEU 大会议题: 关于证书锁定你需要知道的方方面面: https://t.co/Et3slZyTa2"
-

[ Windows ] Windows EoP zero-day exploit used in targeted attacks by FruityArmor APT. https://securelist.com/blog/research/76396/windows-zero-day-exploit-used-in-targeted-attacks-by-fruityarmor-apt/ https://t.co/ASbbrAkKxG
"在使用的 Windows EoP-零日漏洞有针对性攻击由 FruityArmor 公寓: https://t.co/xwhJ8ixZ21 https://t.co/ASbbrAkKxG"
-

[ Windows ] Windows and Ubuntu Interoperability https://blogs.msdn.microsoft.com/wsl/2016/10/19/windows-and-ubuntu-interoperability/
"Windows 与 Ubuntu 的互操作性: https://t.co/XcSCQ2Yhsf"
-

[ Windows ] Windows Kernel Registry Hive loading: relative arbitrary read in nt!RtlValidRelativeSecurityDescriptor https://bugs.chromium.org/p/project-zero/issues/detail?id=876
"Windows Kernel Registry Hive loading: relative arbitrary read in nt!RtlValidRelativeSecurityDescriptor: https://bugs.chromium.org/p/project-zero/issues/detail?id=876"
-

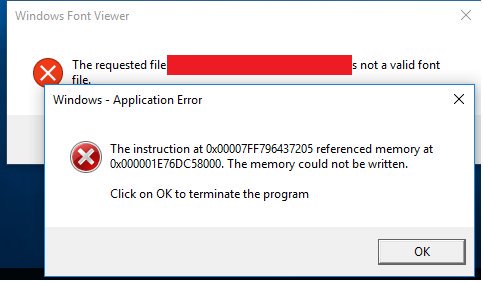
[ Windows ] Windows Kernel win32k.sys TTF font processing: use-after-free in win32k!sbit_Embolden / win32k!ttfdCloseFontContext https://bugs.chromium.org/p/project-zero/issues/detail?id=868
"Windows 内核 win32k.sys 在处理 TTF 字体文件时导致崩溃: https://bugs.chromium.org/p/project-zero/issues/detail?id=868"
-

[ Windows ] Windows Kernel win32k.sys TTF font processing: out-of-bounds read in the RCVT TrueType instruction handler https://bugs.chromium.org/p/project-zero/issues/detail?id=864
"Windows 内核 win32k.sys 处理 TTF 字体时存在越界读漏洞: https://t.co/CZwufA0LO6"
-

[ WirelessSecurity ] RTL-SDR Tutorial: Receiving and Decoding Data from the Outernet http://www.rtl-sdr.com/rtl-sdr-tutorial-receiving-and-decoding-data-from-the-outernet/ https://t.co/kmOHyuP7sI
"RTL-SDR 教程︰从 Outernet 接收和解码数据: http://www.rtl-sdr.com/rtl-sdr-tutorial-receiving-and-decoding-data-from-the-outernet/"
-
[ Browser ] 上面推送了《Bypassing Chrome's and IE's XSS Filters using XML Internal Entities》,知道创宇研究员把它翻译成中文了,《使用 XML 内部实体绕过 Chrome 和 IE 的 XSS 过滤器》: http://paper.seebug.org/80/


 Xuanwu Spider via GitHub
Xuanwu Spider via GitHub