
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] How to: Testing Android Application Security, Part 4 https://blogs.mcafee.com/mcafee-labs/patching-android-binary/
"来自 McAfee Blog 的系列文章《如何测试 Android APP 的安全性》,Part 4: https://t.co/ALWpJUqVpG 之前的三部分:Part 3 : https://blogs.mcafee.com/mcafee-labs/testing-android-application-security-part-3 Part 2: https://blogs.mcafee.com/mcafee-labs/testing-android-application-security-part-2 Part 1: https://blogs.mcafee.com/mcafee-labs/testing-android-application-security-part-1 "
-

[ Attack ] FuzzySec -> Anatomy of UAC Attacks - http://www.fuzzysecurity.com/tutorials/27.html
"解析 UAC 攻击: http://www.fuzzysecurity.com/tutorials/27.html"
-

[ Browser ] CFI all the Chromes! http://crbug.com/464797 http://crbug.com/469376 http://crbug.com/537386 http://crbug.com/584575 https://t.co/MfA34oVbqr
" Chrome 浏览器将要在各个平台启用 CFI: https://t.co/ugHjhbX41f https://t.co/akzjl90wUz https://t.co/hinCZK8e9d https://t.co/zlCFaTAcgM https://t.co/MfA34oVbqr"
-

[ Debug ] I recently learned how does a debugger set breakpoints. I implemented it and wrote a blog post about it - https://t.co/7f9rQVwA8U
" 调试器中的断点设置是如何实现的: http://majantali.net/2016/10/how-breakpoints-are-set/"
-

[ Hardware ] Low-cost IMSI catcher for 4G/LTE networks tracks phones’ precise locations http://arstechnica.com/security/2015/10/low-cost-imsi-catcher-for-4glte-networks-track-phones-precise-locations/
"一种通过利用手机 LTE 通信标准实现低成本手机精确定位的方法: http://arstechnica.com/security/2015/10/low-cost-imsi-catcher-for-4glte-networks-track-phones-precise-locations/"
-

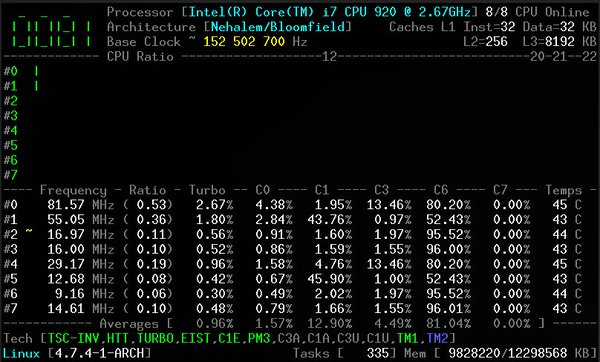
[ Linux ] A Linux kernel module which monitors the true processor frequencies https://github.com/cyring/corefreq#corefreq https://t.co/sK4diCxCOp
" 一个用于监控 CPU 频率变化的 Linux 内核模块: https://t.co/OiEItT1YFV https://t.co/sK4diCxCOp"
-

[ Mobile ] Mobile Security News Update October 2016 https://www.mulliner.org/blog/blosxom.cgi/security/mobile_security_news_update_oct2016.html OMG so many pics!
"由 Collin Mulliner 总结的 10 月份移动安全动态: https://t.co/dj821gf5Op "
-

[ Others ] We just published a post from Alex Triaca on using reflection and dynamic code loading securely https://labs.mwrinfosecurity.com/blog/securing-the-loading-of-dynamic-code/
"作者介绍了 3 种方法以实现在动态代码加载中对反射的保护: https://labs.mwrinfosecurity.com/blog/securing-the-loading-of-dynamic-code"
-

[ Vulnerability ] Malware Authors vs Analysts - How to detect local files and bypass CVE-2016-3298, evading analysts. PoC:… https://t.co/4TDrMVVgkY
"CVE-2016-3298 漏洞利用解析+PoC: https://www.brokenbrowser.com/detecting-local-files-to-evade-analysts"
-

[ Web Security ] Wordpress Hardening Guide https://github.com/ernw/hardening/blob/master/web_application/wordpress/4.4.2/ERNW_Wordpress_Hardening.md
-

[ Web Security ] 'DealersChoice’ is Sofacy’s Flash Player Exploit Platform - http://researchcenter.paloaltonetworks.com/2016/10/unit42-dealerschoice-sofacys-flash-player-exploit-platform/
"‘DealersChoice’ is Sofacy’s Flash Player Exploit Platform: http://researchcenter.paloaltonetworks.com/2016/10/unit42-dealerschoice-sofacys-flash-player-exploit-platform"
-

[ Windows ] Windows: DeviceApi CMApi PiCMOpenDeviceKey Arbitrary Registry Key Write EoP https://bugs.chromium.org/p/project-zero/issues/detail?id=872
" Windows: DeviceApi CMApi PiCMOpenDeviceKey Arbitrary Registry Key Write EoP,来自 Project Zero: https://t.co/sSylhfXdAV"
-

[ Windows ] Windows: DFS Client Driver Arbitrary Drive Mapping Elevation of Privileges https://bugs.chromium.org/p/project-zero/issues/detail?id=885
"Windows: DFS Client Driver Arbitrary Drive Mapping EoP: https://t.co/XJ9K22PKqp"
-
[ OpenSourceProject ] Foxit PDF Reader JBIG2 Parser 信息泄漏漏洞: http://blog.talosintel.com/2016/10/foxit-pdf-jbig2.html
-
[ Tools ] Hopper Disassembler ELF Section Header Size Code Execution: http://blog.talosintel.com/2016/10/hopper.html
-
[ Attack ] APT attacks —pay attention to the man behind the curtain(注意窗帘后面的人): https://community.hpe.com/t5/Security-Research/Advanced-Persistent-Threats-debunked-Pay-attention-to-the-man/ba-p/6908653#.WAbHMPRbKGc
-
[ Detect ] 通过计算 indirect branches 的密度来检测 ROP 攻击的方法: https://loccs.sjtu.edu.cn//gossip/blog/2016/10/18/2016-10-18/
-
[ iOS ] Pegasus内核漏洞分析与利用(一)(CVE-2016-4655/CVE-2016-4656) : http://mp.weixin.qq.com/s?__biz=MjM5NTc2MDYxMw==&mid=2458280200&idx=1&sn=86f7a88863154b1261c1a8ee595a94f9&chksm=b181518286f6d8942f58a1e3f42094d04ec20a9f83cf205dd5985af64cd96c6c8db61eadce1c&scene=0#wechat_redirect
 Xuanwu Spider via Cisco Talos
Xuanwu Spider via Cisco Talos