腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Leftover Factory Debugger Doubles as Android Backdoor: https://threatpost.com/leftover-factory-debugger-doubles-as-android-backdoor/121302/ via @ threatpost
" 富士康生产的 Android 固件中遗留的工厂调试器被认为是后门: https://t.co/mP19NUfNs1"
-

[ Browser ] ? We just announced our intent to ship the Web Bluetooth API in Chrome 56 at https://groups.google.com/a/chromium.org/forum/#!msg/blink-dev/Ono3RWkejAA/2skvuBhSCQAJ https://t.co/jxrVGkcIU5
" Chrome 计划在 56 版本开始支持 Web Bluetooth(蓝牙)相关的 API: https://t.co/XTk1Do9UNf https://t.co/jxrVGkcIU5 "
-

[ Fuzzing ] I just released my web fuzzer (urlfuzz) written in NodeJS https://github.com/danigargu/urlfuzz
" NodeJS 写的一个 Web Fuzzer - urlfuzz: https://t.co/QbEgNbxwLu "
-

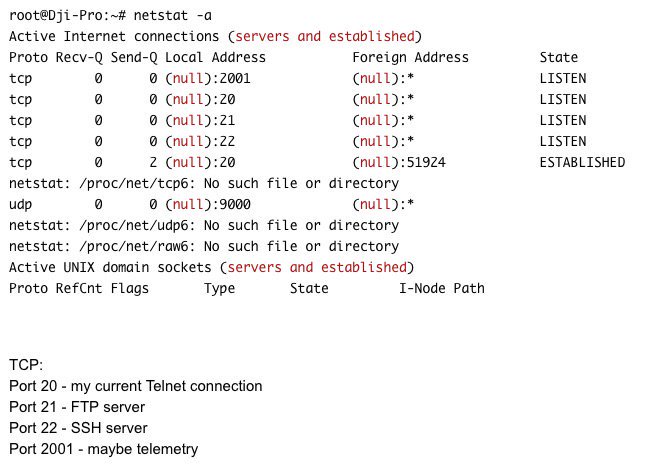
[ Hardware ] Hacking DJI Osmo http://www.g0l.ru/blog/n4101 https://t.co/C5pTobPqVT
" Hacking DJI(大疆) Osmo 云台相机: https://t.co/LR9cSVJG76 "
-

[ Linux ] Linux kernel stack corruption trigger https://bugzilla.redhat.com/attachment.cgi?id=1198213. more info https://bugzilla.redhat.com/show_bug.cgi?id=1373499
"Linux 内核在读取 '/proc/keys' 时触发的一个栈破坏漏洞: https://bugzilla.redhat.com/show_bug.cgi?id=1373499 PoC: https://t.co/AxEWnaPbEC "
-

[ Malware ] LockyDump : A PE32 Windows binary app. used for extracting embedded configurations from the Locky malware family : https://github.com/vrtadmin/Locky
" LockyDump - 用于从 Locky 勒索软件中提取其配置信息的工具︰ https://t.co/njxuANojJg"
-

[ Others ] The latest PHP5.6/7.0 release fix a unserialize() ’s UaF reported by me. https://bugs.php.net/bug.php?id=73147
" PHP 5.6.26 Use After Free in unserialize(): https://t.co/3hV8C72UA7"
-

[ Others ] Exploiting CORS Misconfigurations for Bitcoins and Bounties http://blog.portswigger.net/2016/10/exploiting-cors-misconfigurations-for.html
" 从黑客的角度检查 CORS 的配置问题: https://t.co/1mwnkmWahD "
-

[ Pentest ] Pentesting with MultiRelay, quick intro: https://g-laurent.blogspot.com/2016/10/introducing-responder-multirelay-10.html
"MultiRelay--一个可用于SMB中继攻击的渗透测试工具: https://g-laurent.blogspot.com/2016/10/introducing-responder-multirelay-10.html "
-

[ ReverseEngineering ] x64dbgbinja - Official x64dbg plugin for Binary Ninja. https://github.com/mrexodia/x64dbgbinja #x64dbg #infosec
"x64dbg 官方为二进制逆向分析工具 Binary Ninja 提供了插件支持: https://github.com/x64dbg/x64dbgbinja"
-

[ Tools ] Burp Suite 1.7.08 released, with new scan checks for CORS issues http://releases.portswigger.net/2016/10/1708.html
" Burp Suite 1.7.08 版本发布,开始支持 CORS: https://t.co/f2hAd2c0lB"
-

[ Web Security ] Whitelabel RCE insights: http://secalert.net/cve-2016-4977.html
" Pivotal Spring Security OAuth 组件的 RCE 漏洞(CVE-2016-4977)︰ https://t.co/hscdS2d28L"
-

[ Windows ] Windows: Diagnostics Hub DLL Load EoP https://bugs.chromium.org/p/project-zero/issues/detail?id=887
" Windows Diagnostics Hub DLL Load EoP(CVE-2016-7188),来自 Project Zero Issue 887: https://t.co/mqlRwkQZYk"
-

[ Windows ] Microsoft GDI+ rendering of uninitialized heap bytes as pixels when handling malformed RLE-compressed bitmaps https://bugs.chromium.org/p/project-zero/issues/detail?id=825
"Windows GDI+ RLE 压缩位图未初始化堆内存读漏洞(CVE-2016-3262): https://t.co/2RJ9fuy4HY "