腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Adaptive Kernel Live Patching: An OpenCollaborative Effort toAmeliorate AndroidN-day Root Exploits : https://www.blackhat.com/docs/us-16/materials/us-16-Zhang-Adaptive-Kernel-Live-Patching-An-Open-Collaborative-Effort-To-Ameliorate-Android-N-Day-Root-Exploits.pdf #BlackHat2016
" 自适应内核实时 Patch 技术 - 针对 Android NDay Root Exploits 的解决方案,来自 BlackHat 会议︰ https://t.co/hYSi3l4ljS "
-

[ Android ] Courier scam prods victims to download malicious app. Here's the report: http://bit.ly/2aCMrlP
" 2016 年第一季度,很多新加坡用户收到快递诈骗电话,他们被诱导下载恶意 APP,来自趋势科技的分析︰ https://t.co/qx2kCOrmSI"
-

[ Android ] BHUSA16 - OAuth Demystified for Mobile Application Developers [PDF] https://www.blackhat.com/docs/us-16/materials/us-16-Tian-1000-Ways-To-Die-In-Mobile-OAuth-wp.pdf [SLIDES] https://www.blackhat.com/docs/us-16/materials/us-16-Tian-1000-Ways-To-Die-In-Mobile-OAuth.pdf
"手机 OAuth 认证中的 1000 种死法,来自 BlackHat 会议的演讲, Paper: https://t.co/lNHR5HF95S PPT: https://t.co/GNSnCqy1Py"
-

[ Attack ] Lack of #encryption leads to large scale cookie exposure - http://ow.ly/C3z0302WiI6 #BHUSA
" 无加密导致的大规模 Cookie 泄漏对安全和隐私的影响: https://t.co/hPHmHsZWig PPT: https://www.blackhat.com/docs/us-16/materials/us-16-Sivakorn-HTTP-Cookie-Hijacking-In-The-Wild-Security-And-Privacy-Implications.pdf Paper: https://www.blackhat.com/docs/us-16/materials/us-16-Sivakorn-HTTP-Cookie-Hijacking-In-The-Wild-Security-And-Privacy-Implications-wp.pdf "
-

[ Attack ] Paper and slides from our #BHUSA presentation are available at https://iranthreats.github.io
-

[ Attack ] Security considerations for compromised Slack user tokens http://sites.udel.edu/mdevans/2016/08/04/beware-an-attack-on-slack/
" 小心针对 Slack 用户的攻击: https://t.co/U1TULF5hJL "
-

[ Attack ] Israeli security firm hacks ISIS forum, discloses future targets https://www.grahamcluley.com/2016/08/israeli-security-firm-hacks-isis-forum-discloses-future-targets/
"以色列安全公司声称,他们黑掉了一个 ISIS 论坛,发现了一些潜在的 ISIS 攻击目标: https://t.co/cYzRiWJKUl"
-

[ Attack ] Operation #Manul / Unveiling a Campaign of Intimidation, Kidnapping, and #Malware in Kazakhstan [PDF] https://www.eff.org/files/2016/08/03/i-got-a-letter-from-the-government.pdf
" Manul 攻击 - 某天,我收到了一封伪装成哈萨克斯坦政府的钓鱼邮件: https://t.co/b3EkxqHeFm "
-

[ Browser ] Proof-of-concept JavaScript malware implemented as a Proxy Auto-Configuration (PAC) File https://github.com/SafeBreach-Labs/pacdoor
" 通过邪恶的 PAC 窃取浏览器的 HTTPS URLs,PAC 指代理自动配置文件。作者在 BlackHat 会议的演讲 PPT: https://www.blackhat.com/docs/us-16/materials/us-16-Kotler-Crippling-HTTPS-With-Unholy-PAC.pdf PoC 代码实现 PacDoor: https://t.co/L72uZa9mhh "
-

[ Browser ] Microsoft extends bug bounty to cover Edge remote code exec http://www.theregister.co.uk/2016/08/05/microsoft_opens_15k_remote_code_exec_edge_preview_pwn_party/
"微软扩充了 Bug Bounty 计划的覆盖面,这次涵盖 Edge 浏览器 Preview 版本的 RCE 漏洞: https://t.co/30FRPJbx7H "
-

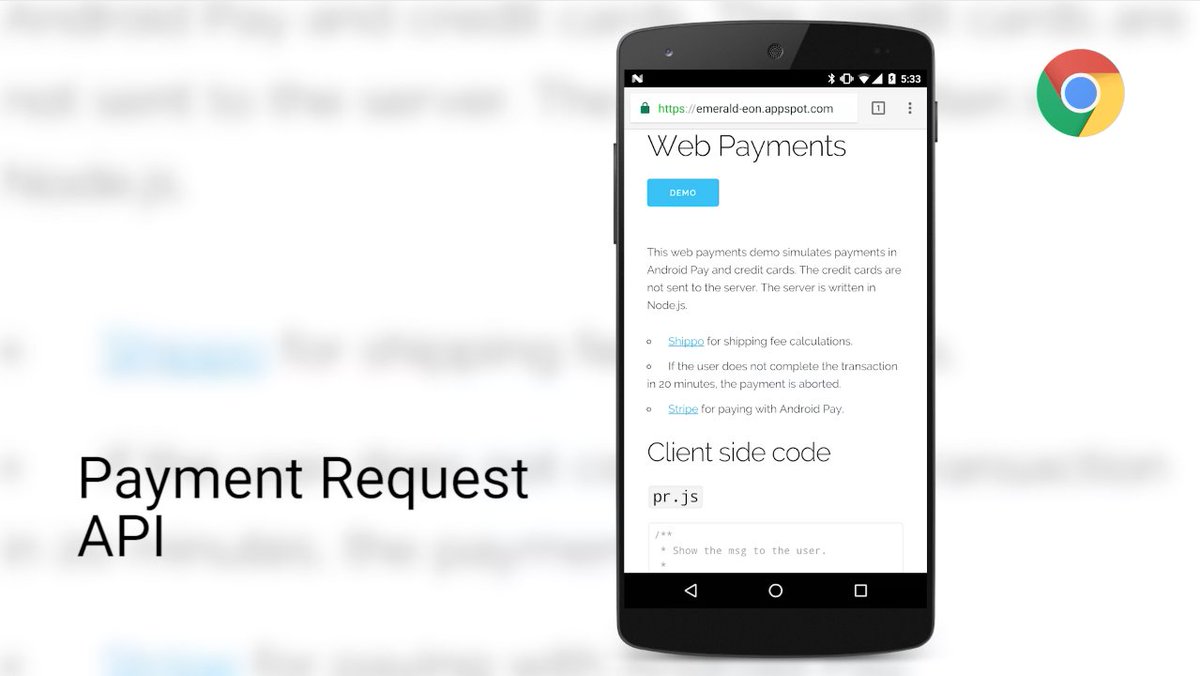
[ Browser ] Payment Request API is coming to Chrome Beta. Check out this introduction article: https://developers.google.com/web/updates/2016/07/payment-request https://t.co/AG8eBMavXU
" Chrome Beta 版马上将会提供对支付相关 API 的支持︰ https://t.co/YCYAtjYcJI "
-

[ Browser ] Let's Encrypt Root to be Trusted by @ mozilla (Firefox v50) https://letsencrypt.org/2016/08/05/le-root-to-be-trusted-by-mozilla.html
" Firefox v50 版本开始,将添加对 Let's Encrypt 根证书密钥的信任,v50 版本将于 2016 年第 4 季度发布: https://t.co/ALw2vN5x0P"
-

[ Cloud ] Post infection persistency & Lateral Movement in AWS : https://www.blackhat.com/docs/us-16/materials/us-16-Amiga-Account-Jumping-Post-Infection-Persistency-And-Lateral-Movement-In-AWS.pdf (Slides) #BlackHat2016
" 亚马逊 AWS 云中的攻击维持和横向穿梭,来自 BlackHat 2016 会议: https://t.co/gSZ1wjl7Hc"
-

[ Defend ] slides of our #BHUSA talk on SGX https://aumasson.jp/data/talks/sgx_bh16.pdf CLI tools + paper https://github.com/kudelskisecurity/sgxfun Reencryption PoC https://github.com/kudelskisecurity/sgx-reencrypt
" Intel SGX 防护扩展 Review 及其 SDK 的使用实践,来自 BlackHat 2016 会议: https://t.co/06wZn9S685 工具 sgxfun: https://t.co/yugxK5ZX1r 基于 SGX 加密的 App PoC: https://t.co/MKfmvQbfa0"
-

[ Detect ] Certificate Bypass : Hiding and Executing Malware from a Digitally Signed Executable : https://www.blackhat.com/docs/us-16/materials/us-16-Nipravsky-Certificate-Bypass-Hiding-And-Executing-Malware-From-A-Digitally-Signed-Executable-wp.pdf (wp) #BlackHat2016
" 在有有效数字签名的可执行程序中藏恶意代码,来自 BlackHat 2016 会议︰ https://t.co/GkVy0uEFG2 "
-

[ Hardware ] Brute-Forcing Lockdown Harddrive PIN Codes : https://www.blackhat.com/docs/us-16/materials/us-16-OFlynn-Brute-Forcing-Lockdown-Harddrive-PIN-Codes.pdf (Slides) #BlackHat2016 https://t.co/gI3UuFEjFe
" 暴力破解 Lockdown 加密硬盘的 PIN 码,来自 BlackHat 2016 会议︰ https://t.co/GYwKFEKCW8 "
-

[ Hardware ] Drone attacks on Industrial Wireless: A new front in Cyber Security : https://www.blackhat.com/docs/us-16/materials/us-16-Melrose-Drone-Attacks-On-Industrial-Wireless-A-New-Front-In-Cyber-Security.pdf (Slides) #BlackHat2016
" 利用无人机攻击工业无线网络,来自 BlackHat 会议︰ https://t.co/m5liHrqVt1 "
-

[ iOS ] Pangu 9 Internals : http://blog.pangu.io/wp-content/uploads/2016/08/us-16-Pangu9-Internals.pdf (Slides)
" Pangu 9 越狱工具的技术内幕,来自盘古团队在 BlackHat 会议的演讲: https://t.co/DgscqpM3i7 "
-

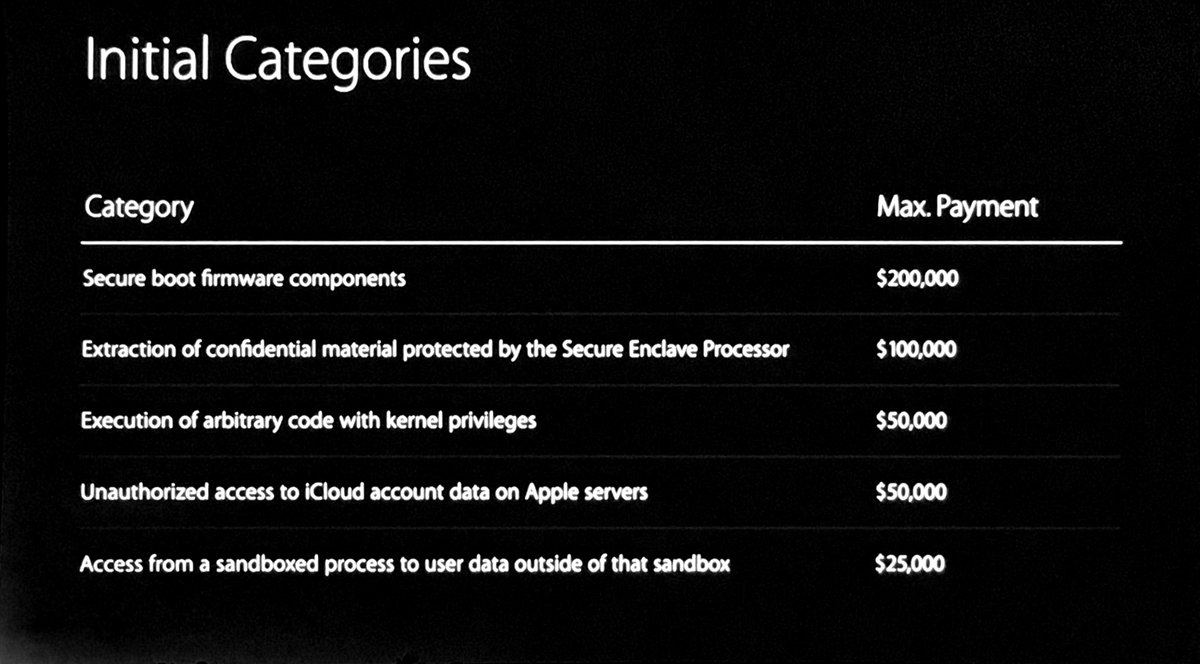
[ iOS ] Apple Security Bounty program initial categories - opens in September https://t.co/XH8rFmpHI9
"苹果将从 9 月份开始启动漏洞奖励计划,固件安全启动组件的漏洞最高可奖励 20 万美金 https://t.co/XH8rFmpHI9"
-

[ iOS ] Demystifying the Secure Enclave Processor : https://www.blackhat.com/docs/us-16/materials/us-16-Mandt-Demystifying-The-Secure-Enclave-Processor.pdf (Slides) #BlackHat2016
" 剖析 Apple SEP(Secure Enclave Processor,安全专用协处理器),来自 BlackHat 会议︰ https://t.co/U8BbxegvKr "
-

[ IoTDevice ] A Lightbulb Worm ? - A teardown of the Philips Hue : https://www.blackhat.com/docs/us-16/materials/us-16-OFlynn-A-Lightbulb-Worm.pdf (Slides) #BlackHat2016
" 飞利浦 Hue 智能灯泡拆解,来自 BlackHat 会议︰ https://t.co/Iyn1NOOQPN "
-

[ macOS ] OS X 10.11.6 now available: http://opensource.apple.com/release/os-x-10116/
"苹果公开了 OS X 10.11.6 的源码︰ https://t.co/rNZIShdxHT"
-

[ Malware ] Cracking HawkEye Keylogger Reborn http://blog.deniable.org/blog/2016/08/04/cracking-hawkeye-keylogger-reborn/
" HawkEye Keylogger '重生'版本的分析: https://t.co/K5xDUXk2kY"
-

[ Malware ] Smoke Loader – downloader with a smokescreen still alive https://blog.malwarebytes.com/threat-analysis/2016/08/smoke-loader-downloader-with-a-smokescreen-still-alive/
" MalwareBytes 对 Smoke Loader Bot 的分析: https://t.co/VVQ9rgmFQC "
-

[ MalwareAnalysis ] AVLeak : Fingerprinting Antivirus Emulators For Advanced Malware Evasion : https://www.blackhat.com/docs/us-16/materials/us-16-Bulazel-AVLeak-Fingerprinting-Antivirus-Emulators-For-Advanced-Malware-Evasion.pdf (Slides)
"AVLeak - 通过为反病毒软件模拟器建立指纹库的方法逃逸检测,来自 BlackHat 2016 会议: https://t.co/UKexh7YeqO "
-

[ Mitigation ] DrK : Breaking Kernel Address Space Layout Randomization with IntelTSX : https://www.blackhat.com/docs/us-16/materials/us-16-Jang-Breaking-Kernel-Address-Space-Layout-Randomization-KASLR-With-Intel-TSX.pdf (Slides) #BlackHat2016
"DrK - 用 Intel TSX 突破内核 KASLR,TSX 指事务性同步扩展机制,来自 BlackHat 会议: https://t.co/63yQeERyYV "
-

[ Network ] Open Source Command line Network Diagnostic Tool : http://mylg.io/
" 网络诊断工具 myLG 更新 0.21 版本︰ https://t.co/OMXDN9oYae"
-

[ Network ] Attacking SDN Infrastructure: Are We Ready for the Next-Gen Networking? : https://www.blackhat.com/docs/us-16/materials/us-16-Yoon-Attacking-SDN-Infrastructure-Are-We-Ready-For-The-Next-Gen-Networking.pdf (Slides) #BlackHat2016
"攻击 SDN 基础设施:我们为下一代网络做好准备了吗?来自 BlackHat 会议: https://t.co/70IaxSXzyu"
-

[ NetworkDevice ] Several 0 day RCE in Nuuo and Netgear NVR, including ARM ROP exploit http://seclists.org/bugtraq/2016/Aug/45
" Nuuo 网络视频监控设备和 Netgear 监控 APP 被曝多个远程漏洞,来自 FullDisclosure 的公告: https://t.co/QGZ7tgMwXs"
-

[ NetworkDevice ] Netis Router Backdoor UDP 53413 http://neonprimetime.blogspot.com/2016/08/netis-router-backdoor-udp-53413.html
"Netis 路由器的 UDP 53413 端口后门: https://t.co/EyjrMLGgpx"
-

[ OpenSourceProject ] https://github.com/d0lph1n98/Defeating-PHP-GD-imagecreatefromgif Exploiting PHP-GD imagecreatefromgif()
" Exploiting PHP-GD imagecreatefromgif(): https://t.co/PV0C9JmIwa "
-

[ Others ] The different ways of hooking - http://www.rohitab.com/discuss/topic/41855-tutorial-the-different-ways-of-hooking/
" Hook 代码实现的不同方式: https://t.co/iqdEPOmUzI"
-

[ Others ] Notes on concurrency bugs http://danluu.com/concurrency-bugs/
" 跟并发有关的一些 Bug: https://t.co/CwjZndkRi0 "
-

[ Others ] The future of vuln discovery, perspective from Google. #BountyCraft https://t.co/wa30sIbazn
" Google 研究员对未来漏洞挖掘发展趋势的看法(图): https://t.co/wa30sIbazn"
-

[ Others ] Slides are now online from @ granick's and my #BHUSA2016 talk on law enforcement technical assistance demands. https://www.blackhat.com/docs/us-16/materials/us-16-Granick-When-The-Cops-Come-A-Knocking-Handling-Technical-Assistance-Demands-From-Law-Enforcement.pdf
" 当被警方求助收集用户信息时,需要考虑的法律问题,来自 BlackHat 会议: https://t.co/dIPruE008y"
-

[ Others ] New blogpost: Ruby on Rails 脆弱性解説 - CVE-2016-0752(前編) - DARK MATTER http://io.cyberdefense.jp/entry/2016/08/05/Ruby_on_Rails_%E8%84%86%E5%BC%B1%E6%80%A7%E8%A7%A3%E8%AA%AC_-_CVE-2016-0752%EF%BC%88%E5%89%8D%E7%B7%A8%EF%BC%89
" Ruby on Rails CVE-2016-0752 漏洞分析(日文): https://t.co/aZ8ODAUEqN"
-

[ Others ] Breaking Hardware-Enforced Security with Hypervisors : https://www.blackhat.com/docs/us-16/materials/us-16-Sharkey-Breaking-Hardware-Enforced-Security-With-Hypervisors.pdf (Slides) #BlackHat2016
" 用 Hypervisors 打破硬件强化的安全性,来自 BlackHat 会议︰ https://t.co/XL4Rrfiroh "
-

[ Others ] Slides, code and paper for our #BH2016 posted https://goo.gl/BBPb5F @ rohitwas @ BlackHatEvents
" DPTrace - Crash 的可利用性分析,PPT 和相关的代码: https://github.com/rrbranco/BlackHat2016 "
-

[ Others ] Remote Butler Attack resources are available on @ BlackHatEvents site Preso: https://www.blackhat.com/docs/us-16/materials/us-16-Beery-The-Remote-Malicious-Butler-Did-It.pdf WP: https://www.blackhat.com/docs/us-16/materials/us-16-Beery-The-Remote-Malicious-Butler-Did-It-wp.pdf #BHUSA
" 之前有人提出过针对全盘加密的 Evil Maid 攻击,这次作者提出了一种称为 Remote Butler 的新攻击,来自 BlackHat 会议︰ https://t.co/nXdCj8aC1y Paper︰ https://t.co/CKYyZHZKk6 "
-

[ Others ] BHUSA16 - Attacking BYOD enterprise mobile security solutions - https://www.blackhat.com/us-16/briefings.html#bad-for-enterprise-attacking-byod-enterprise-mobile-security-solutions
" 攻击企业 BYOD 移动安全解决方案,来自 BlackHat 会议,PPT: https://www.blackhat.com/docs/us-16/materials/us-16-Tan-Bad-For-Enterprise-Attacking-BYOD-Enterprise-Mobile-Security-Solutions.pdf Paper: https://www.blackhat.com/docs/us-16/materials/us-16-Tan-Bad-For-Enterprise-Attacking-BYOD-Enterprise-Mobile-Security-Solutions-wp.pdf 工具下载: https://www.blackhat.com/docs/us-16/materials/us-16-Tan-Bad-For-Enterprise-Attacking-BYOD-Enterprise-Mobile-Security-Solutions-tool.zip "
-

[ Others ] BHUSA16 - Samsung Pay: tokenized numbers flaws and issues [SLIDES] https://www.blackhat.com/docs/us-16/materials/us-16-Mendoza-Samsung-Pay-Tokenized-Numbers-Flaws-And-Issues.pdf [PDF] https://www.blackhat.com/docs/us-16/materials/us-16-Mendoza-Samsung-Pay-Tokenized-Numbers-Flaws-And-Issues-wp.pdf
" Samsung Pay 标记化数字(Tokenized Numbers)相关的漏洞,来自 BlackHat 会议,PPT: https://t.co/ih48GR70YL Paper: https://t.co/fIpxfFq60B"
-

[ Pentest ] Socat cheat sheet for #Pentesting https://stuff.mit.edu/afs/sipb/machine/penguin-lust/src/socat-1.7.1.2/EXAMPLES
" 渗透测试工具 Socat 使用手册: https://t.co/0a3zsQ0CJv "
-

[ Popular Software ] THE YEAR IN FLASH (flash vulnerability research results): https://www.blackhat.com/docs/us-16/materials/us-16-Silvanovich-The-Year-In-Flash.pdf
" Project Zero 女黑客 Natalie Silvanovich 过去一年 Flash 的研究成果︰ https://t.co/3kXXnTc582"
-

[ ReverseEngineering ] Latest PPT for the art of reverse engineering Flash exploits - https://www.dropbox.com/s/7aomaul20nfckgn/us-16-Oh-The-Art-of-Reverse-Engineering-Flash-Exploits.pdf?dl=0 Full Paper: https://www.dropbox.com/s/zydd5q474e9usbf/us-16-Oh-The-Art-of-Reverse-Engineering-Flash-Exploits-wp.pdf?dl=0
" Flash Exploits 逆向的艺术,来自 BlackHat 2016 会议,PPT: https://t.co/BCJ20MlkRn Paper︰ https://t.co/KogXNzEa8T"
-

[ SCADA ] PLC-Blaster Worm Targets Industrial Control Systems https://threatpost.com/plc-blaster-worm-targets-industrial-control-systems/119696/
"BlackHat 会议上,有黑客公开了一个攻击工控系统的蠕虫病毒 - PLC Blaster,来自 ThreatPost 的报道: https://t.co/6hSMIRVgC3 PPT: https://www.blackhat.com/docs/asia-16/materials/asia-16-Spenneberg-PLC-Blaster-A-Worm-Living-Solely-In-The-PLC.pdf Paper: https://www.blackhat.com/docs/asia-16/materials/asia-16-Spenneberg-PLC-Blaster-A-Worm-Living-Solely-In-The-PLC-wp.pdf "
-

[ Tools ] Salesforce's open-source pentesting management and automation platform : http://vulnreport.io/
"Vulnreport - Salesforce 开源的一个渗透测试管理和自动化协作平台︰ https://t.co/WwRKND7JEC"
-

[ Tools ] AVulnerabilityChecker - check vulnerable to exploitable constant RWX addresses (AVs vulnerability).Based on wiappdbg https://github.com/BreakingMalware/AVulnerabilityChecker
"AVulnerabilityChecker - 检查进程是否存在连续 RWX(可读、可写、可执行)内存地址的工具: https://t.co/0jFSG8yXnY"
-

[ Windows ] Some fun with vintage bugs and driver signing enforcement : http://kat.lua.cz/posts/Some_fun_with_vintage_bugs_and_driver_signing_enforcement/
" 通过一些驱动的老漏洞禁用 DSE(Driver Signing Enforcement)︰ https://t.co/6U1xEfcEfT"
-

[ Windows ] Uninitialized Stack Variable - Windows Kernel Exploitation http://www.payatu.com/uninitialized-stack-variable/
" Windows 内核栈上变量未初始化漏洞的利用: https://t.co/vQLyRxMzE3"
-

[ Windows ] AMSI : How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does It : https://www.blackhat.com/docs/us-16/materials/us-16-Mittal-AMSI-How-Windows-10-Plans-To-Stop-Script-Based-Attacks-And-How-Well-It-Does-It.pdf (Slides) #BlackHat2016
"AMSI - Windows 10 打算如何解决基于脚本的攻击,又是如何做的,来自 BlackHat 会议: https://t.co/Rw5yuiMcxp "
-

[ Windows ] Analysis of the Attack Surface of Windows 10 Virtualization-Based Security : https://www.blackhat.com/docs/us-16/materials/us-16-Wojtczuk-Analysis-Of-The-Attack-Surface-Of-Windows-10-Virtualization-Based-Security.pdf (Slides) #BlackHat2016
" Windows 10 基于虚拟化的安全架构的攻击面分析,来自 BlackHat 2016 会议,PPT︰ https://t.co/8DLuSWe22u Paper: https://www.blackhat.com/docs/us-16/materials/us-16-Wojtczuk-Analysis-Of-The-Attack-Surface-Of-Windows-10-Virtualization-Based-Security-wp.pdf "
-

[ Windows ] I posted the slides, setup script and walkthrough for our DefCon Windows Breakout & Privesc workshop on GitHub - https://github.com/FuzzySecurity/DefCon24
" FuzzySecurity 公开的他们在 DefCon 24 用于 Windows 权限逃逸的资料和工具: https://t.co/7g8D4AyJzN"
-

[ Windows ] Presentation slides for my Black Hat talk on WSL/LXSS: "The Linux Kernel Hidden Inside Windows 10" are up at https://github.com/ionescu007/lxss
" 藏在 Windows 10 中的 Linux 内核,来自 Alex Ionescu 在 BlackHat 会议的演讲: https://t.co/ig2L3lBaRY"
-

[ Windows ] WINDOWS 10 SEGMENT HEAP INTERNALS: https://www.blackhat.com/docs/us-16/materials/us-16-Yason-Windows-10-Segment-Heap-Internals.pdf https://www.blackhat.com/docs/us-16/materials/us-16-Yason-Windows-10-Segment-Heap-Internals-wp.pdf
" Windows 10 Segment Heap Internals,来自 BlackHat 2016 会议︰ https://t.co/hcYnmqOTZs Paper: https://t.co/s1E7xdk7FT"
-

[ Windows ] WINDOWS 10 MITIGATION IMPROVEMENTS: https://www.blackhat.com/docs/us-16/materials/us-16-Weston-Windows-10-Mitigation-Improvements.pdf
"Windows 10 在漏洞利用缓解措施方面的改进,来自微软研究员在 BlackHat 会议的演讲︰ https://t.co/8h4Ju7T5tM BlackHat 会议,除了演讲,还有一个称为 '兵器库' 的部分,其中很多工具也值得看看: https://www.blackhat.com/us-16/arsenal.html "