腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Some Ideas about Fuzzing Android OMX Shared at #hitcon2016: http://hitcon.org/2016/CMT/slide/day2-r2-c-1.pdf @ Mingjian_Zhou @ C0RETeam
"Fuzzing Android OMX,来自 CoreTeam 研究员 Mingjian Zhou 在 HITCon 2016 会议的演讲︰ https://t.co/vri3ZQj3wJ "
-

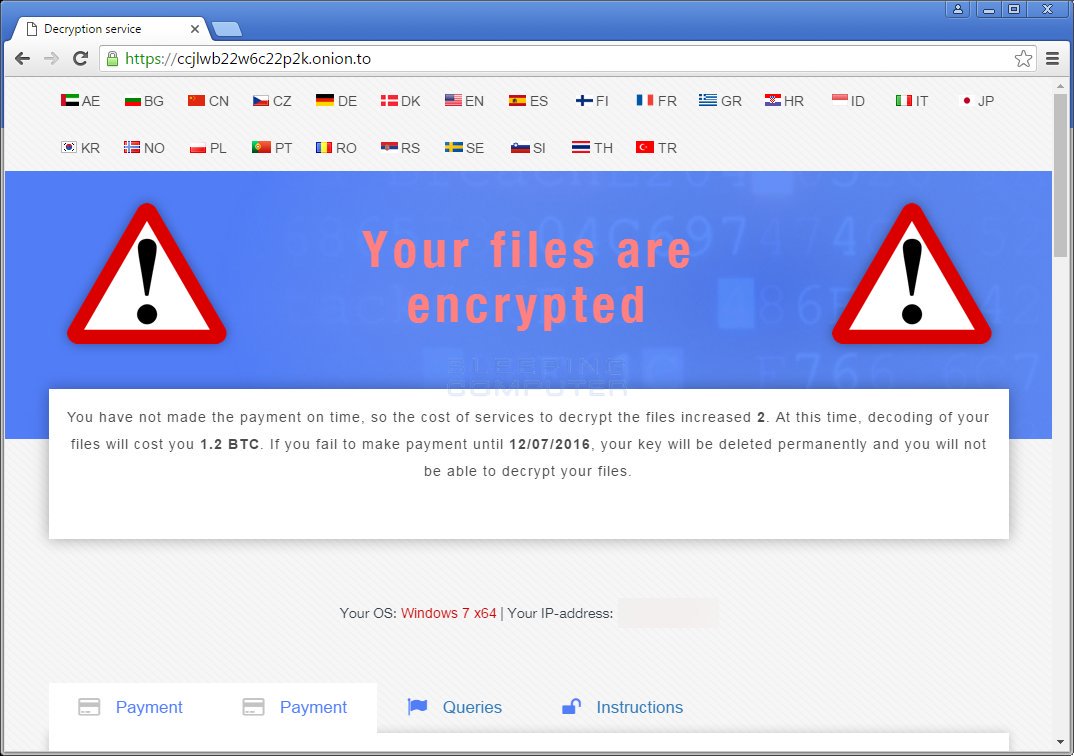
[ Malware ] A side-by-side comparison of the CryptXXX and CrypMic ransomware, by @ bleepincomputer http://www.bleepingcomputer.com/news/security/side-by-side-comparisons-of-the-crypmic-and-cryptxxx-ransomware-infections/ https://t.co/sh06bPfKxD
"CryptXXX 和 CrypMic 两款勒索软件的比较: https://t.co/qGCfnM3kWf "
-

[ Malware ] New post: Economics Behind Ransomware as a Service: A Look at Stampado’s Pricing Model http://bit.ly/2asiWqa @ TrendMicro
" 勒索软件价格背后的经济 - Stampado 勒索软件的定价模型: https://t.co/mFQhp8PNU5 "
-

[ Malware ] Keys to #Chimera #ransomware leaked: https://blog.malwarebytes.com/cybercrime/2016/07/keys-to-chimera-ransomware-leaked/
"Chimera 勒索软件 3500 个 RSA 密钥流出︰ https://t.co/j8kzjkGtD0"
-

[ Malware ] Zeus Panda Delivered By Sundown - Targets UK Banks https://blogs.forcepoint.com/security-labs/zeus-panda-delivered-sundown-targets-uk-banks
"Sundown Exploit Kit 正在传播 Zeus Panda 木马: https://t.co/9Y6mzneQ0q"
-

[ Malware ] Tracking the Actor Behind the MAN1 Crypter : http://www.threatgeek.com/2016/07/tracking-man1-crypter-actor.html https://t.co/54cbJTfWoG
" 追溯 MAN1 Crypter 背后的攻击者: https://t.co/TQirsqtPfF "
-

[ Obfuscation ] Released dex-oracle v1.0.5, android deobfuscation tool - http://buff.ly/2afJo4L https://t.co/86rysK1p8N
" dex-oracle - 基于模式的 Android Dalvik 反混淆工具: https://t.co/BlTGNgTZQ9 "
-

[ Others ] Keeping Positive - Obtaining Arbitrary Wildcard SSL Certificates from Comodo via Dangling Markup Injection https://thehackerblog.com/keeping-positive-obtaining-arbitrary-wildcard-ssl-certificates-from-comodo-via-dangling-markup-injection/index.html
"通过 HTML 注入漏洞从 Comodo 获得任意通配符的 SSL 证书: https://t.co/N4rnlmuBf1 "
-

[ Others ] Ease of use - IPhone fingerprint support! Microsoft Authenticator @ dispensa https://blogs.technet.microsoft.com/enterprisemobility/2016/07/25/microsoft-authenticator-coming-august-15th/ via @ msftmobility
" 微软认证(Microsoft Authenticator) APP 应用马上要支持指纹验证了: https://t.co/Fc4WLc975s"
-

[ Others ] Juggling hashes with your eyes closed in PHP applications : http://www.digitalloft.org/init/plugin_wiki/page/juggling-hashes-with-your-eyes-closed-in-php
" PHP 应用程序中双等号(==)相关的安全问题︰ https://t.co/65lt6WpfRt"
-

[ Others ] Slides of my #CAV2016 talk "End-to-End Verification of ARM Processors with ISA-Formal" available at https://alastairreid.github.io/alastairreid.github.io/papers/ISA-Formal-CAV2016.pdf
" ARM 处理器端到端的验证,来自 CAV2016 会议的演讲: https://t.co/0vlxhd5Az3"
-

[ Others ] The story about how we created 0patch for Foxit Reader CVE-2016-3740: https://0patch.blogspot.com/2016/07/0patching-foxit-readers-heap-buffer.html …
" 0Patch for Foxit Reader's Heap Buffer Overflow Vulnerability CVE-2016-3740︰ https://t.co/9YNvFg14rk..."
-

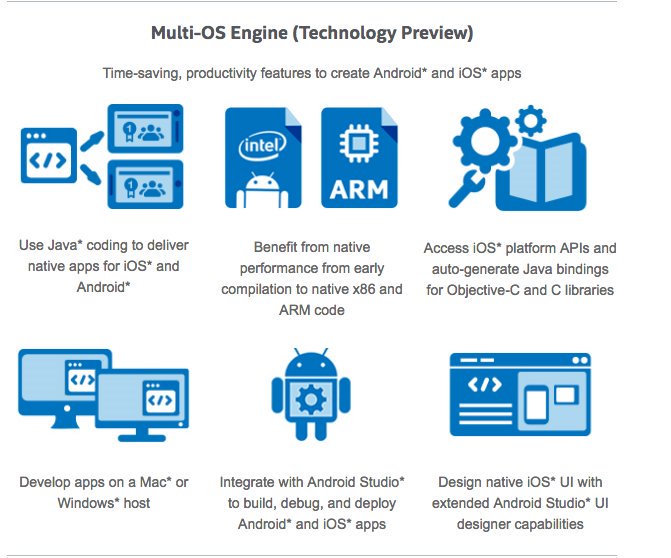
[ Others ] Intel Multi-OS Engine: Use Java to develop native mobile apps for iOS & Android on OSX & Win https://software.intel.com/en-us/multi-os-engine https://t.co/aHLA6kVxj1
" Intel Multi-OS 引擎 - 用 Java 为 iOS 和 Android 开发 Native 应用: https://t.co/zqCZVqf1aL "
-

[ Pentest ] Read this: Pentesting in the real world. It's our latest blog series by and for pentesters: http://r-7.co/2a9vuCS
" 真实世界中的渗透测试,来自 Rapid7 Blog: https://t.co/3zyCJVLoXV"
-

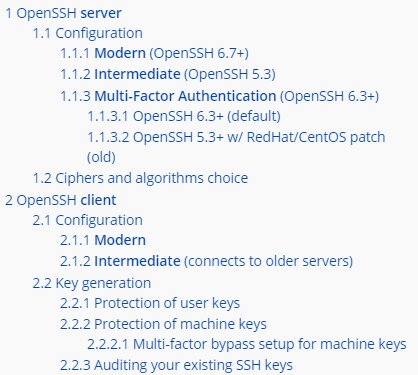
[ Popular Software ] For those who prefer a manual approach: OpenSSH security guidelines from the Mozilla Wiki https://wiki.mozilla.org/Security/Guidelines/OpenSSH https://t.co/CDmh2Pb0pI
" OpenSSH 服务器和客户端安全配置指南: https://t.co/DsUvyesD6f "
-

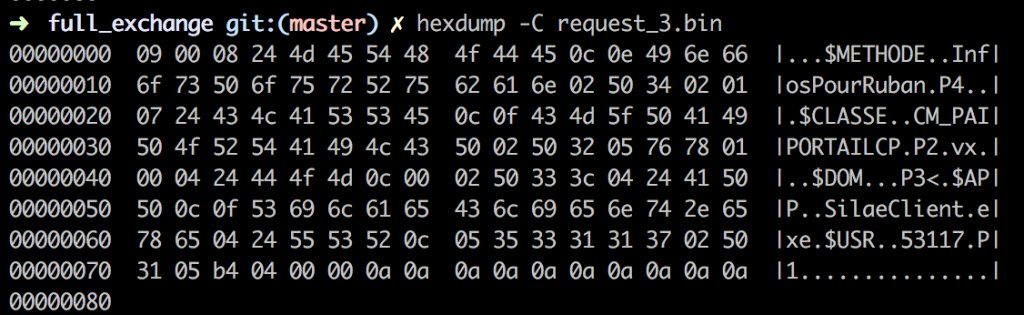
[ ReverseEngineering ] MITM Attack — Reverse Engineering an Encrypted Service : http://www.theodo.fr/blog/2016/07/mitm-attack-reverse-engineering-an-encrypted-service/ https://t.co/GtpybZNdLd
" Silaexpert 加密服务的逆向︰ https://t.co/sI33XKR030 "
-

[ Tools ] Comparison of function hooking libraries : https://github.com/frida/frida/wiki/Comparison-of-function-hooking-libraries
" 几款函数 Hook 库的比较,包括 Frida、CydiaSubstrate、Detours 等︰ https://t.co/z3jpxb7icm"
-

[ Tools ] Burp Infiltrator http://blog.portswigger.net/2016/07/introducing-burp-infiltrator.html
"最新版的 Burp 增加了一个新工具 - Burp Infiltrator: https://t.co/GfjYsg92iZ"
-

[ Tools ] Burp Suite 1.7.04 released, with Burp Infiltrator, new IAST tool http://releases.portswigger.net/2016/07/1704.html
" Burp Suite 更新 1.7.04 版本,更新日志: https://t.co/lVatXkAD3z"
-

[ Tools ] Snapper : A security tool for grabbing screenshots of many web hosts : https://github.com/dxa4481/Snapper
"Snapper - 可以为 Web 页面批量生成截图的工具︰ https://t.co/7KehXGtX1I PhantomJS 的 render() API 也可以为 Web 页面生成截图"
-

[ Virtualization ] CVE-2016-6258 / XSA-182, PV Privilege Escalation in x86, break out of VM vulnerability now public: http://xenbits.xen.org/xsa/advisory-182.html Happy reboots!
"Xen PV Guest 提权漏洞(CVE-2016-6258)︰ https://t.co/y5XyxN9X1u 还有一个拒绝服务漏洞: https://xenbits.xen.org/xsa/advisory-183.html "
-

[ Windows ] Microsoft GDI+ rendering of uninitialized heap bytes as pixels when handling malformed RLE-compressed bitmaps https://code.google.com/p/google-security-research/issues/detail?id=825
"在处理畸形 RLE 压缩位图时,Windows GDI+ 存在一个未初始化内存使用漏洞,目前状态是 WontFix,来自 Project Zero Issue 825: https://t.co/i9OWfYStXl "
-

[ WirelessSecurity ] #KeySniffer vulnerability opens wireless keyboards to remote snooping http://ow.ly/i9CE302CjHG
"KeySniffer - 无线键盘窃听漏洞,影响 8 个厂商,来自 ThreatPost 的报道: https://t.co/m3Cyzae8nx 技术细节: http://www.keysniffer.net/technical-details/ "