腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Technical analysis by @ anestisb for Android CVE-2016-0835 now available here: https://census-labs.com/news/2016/07/22/android-stagefright-impeg2d_dec_pic_data_thread-overflow/ #CENSUS_SA
" Android Stagefright impeg2d_dec_pic_data_thread 整数溢出漏洞(CVE-2016-0835)︰ https://t.co/PS38iOTp8T "
-

[ Android ] YADD - Yet another Android Dex bytecode Disassembler https://github.com/ZSShen/YADD by @ AndyZSShen
" YADD - Android Dex 字节码反编译工具: https://t.co/0inGgNKZqx "
-

[ Android ] Semi-Offline Attack on the Android Full-Disk Encryption : http://area41.io/downloads/slides/area41_16_kunz_semioffline_attack.pdf (Slides)
"针对 Android 全盘加密的半离线攻击︰ https://t.co/vhyVRMaJTo "
-

[ Browser ] Breaking Bad CSP : http://www.slideshare.net/LukasWeichselbaum/breaking-bad-csp (Slides)
" Breaking Bad CSP: https://t.co/5xrChkGQIJ "
-

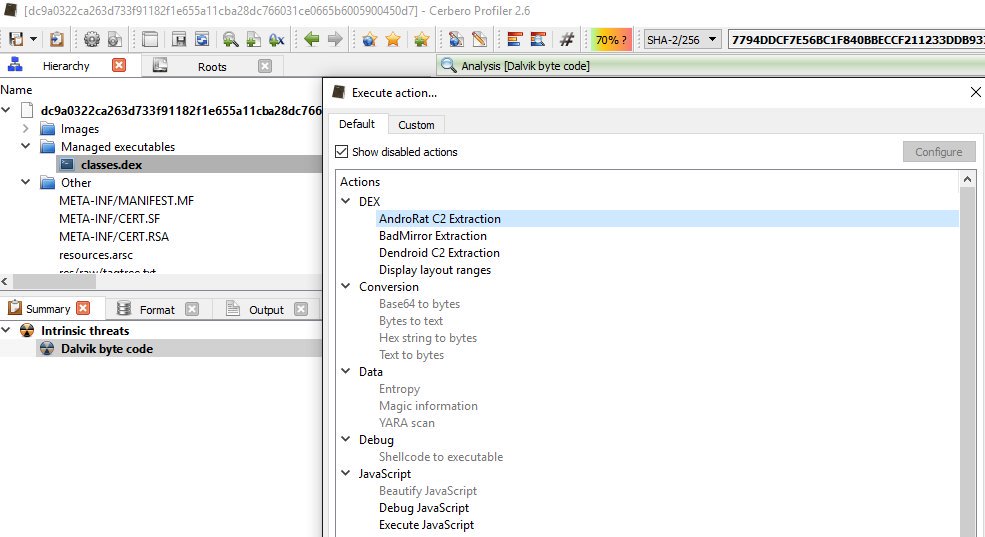
[ Detect ] Extracting C&C from Android Malware: http://cerbero-blog.com/?p=1633 https://t.co/SPsgulzLLq
"利用 Cerbero 工具从 Android 恶意软件中提取 C&C 服务器地址: https://t.co/CSvhtuDNwx "
-

[ Malware ] Kovter click-fraud malware updates: now (almost) file-less, creates a new file type, gets some new certificates http://ow.ly/8RCi302wqxY
"Kovter 点击欺诈恶意软件的常驻方法分析,来自微软 Blog: https://t.co/gNTFbrpVZa"
-

[ Network ] HOnions : Towards Detection and Identification of Misbehaving Tor HSDirs : https://www.securityweek2016.tu-darmstadt.de/fileadmin/user_upload/Group_securityweek2016/pets2016/10_honions-sanatinia.pdf (pdf)
"HOnions - 行为鬼祟(如窃听) 的 Tor 隐藏服务目录(HSDirs)的检测和识别,Paper: https://t.co/8YTSpaG1Xl "
-

[ Others ] CSV Injection Mitigations Revisited https://blog.zsec.uk/csv-dangers-mitigations/
"CSV 注入漏洞: https://t.co/vaZrVo9n0P"
-

[ Others ] Fuzzing Unserialize https://www.evonide.com/fuzzing-unserialize/
" Fuzz 反序列化漏洞: https://t.co/9guVyyrBXS"
-

[ Others ] Non-root GPU passthrough setup http://www.evonide.com/non-root-gpu-passthrough-setup/
"非 Root GPU passthrough 方案搭建教程: https://t.co/ZhvA4ObtxL"
-

[ Protocol ] IMSecure – Attacking VoLTE (and other Stuff) : http://area41.io/downloads/slides/area41_16_ERNW_IMSecure.pdf (Slides) https://t.co/ep8wlfRlje
"IMSecure — Attacking VoLTE︰ https://t.co/hI5AEoN0LG "
-

[ Rootkit ] LibZeroEvil & the Research Rootkit project. https://github.com/NoviceLive/research-rootkit
"LibZeroEvil Rootkit 研究项目: https://t.co/1DfRZZB0iV 中文: https://github.com/NoviceLive/research-rootkit/blob/master/README-zh_CN.rst "
-

[ SecurityProduct ] Barracuda Web App Firewall / Load Balancer Remote Root https://packetstormsecurity.com/files/138020/barracuda_webappfw_and_loadbal_postauth_remote_root.rb.txt
" Barracuda(梭子鱼) Web 应用防火墙负载均衡 Root Exploit: https://t.co/8rfqjFBCxw"
-

[ Web Security ] Drupal module Coder < 7.x-1.3, 7.x-2.6 RCE exploit (SA-CONTRIB-2016-039) https://gist.github.com/Raz0r/7b7501cb53db70e7d60819f8eb9fcef5
"Drupal Coder 模块的一个 RCE 漏洞(SA-CONTRIB-2016-039): https://t.co/fkK9hEDbX9 "
-

[ Web Security ] Exploiting Google Clickjacking Vulnerability to steal user cookies : http://jasminderpalsingh.info/single.php?p=87#.V5LbaWR96tE
"利用 Google 的点击劫持漏洞,窃取用户 cookie: https://t.co/X18p8LYYGk"
-

[ Web Security ] Could finally publish our article about how we pwned Pornhub. Hint: it involved PHP 0day :) https://www.evonide.com/how-we-broke-php-hacked-pornhub-and-earned-20000-dollar/
" 我是如何发现 Pornhub 网站漏洞并获得 2 万刀奖励的: https://t.co/SpeU3HGVp6"
-

[ Windows ] Fun with the Windows Subsystem for Linux : https://blogs.windows.com/buildingapps/2016/07/22/fun-with-the-windows-subsystem-for-linux/ https://t.co/cx5dsIA6uV
"把玩 Windows 新加入的 Linux 子系统: https://t.co/rSetyq6nRs "