腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

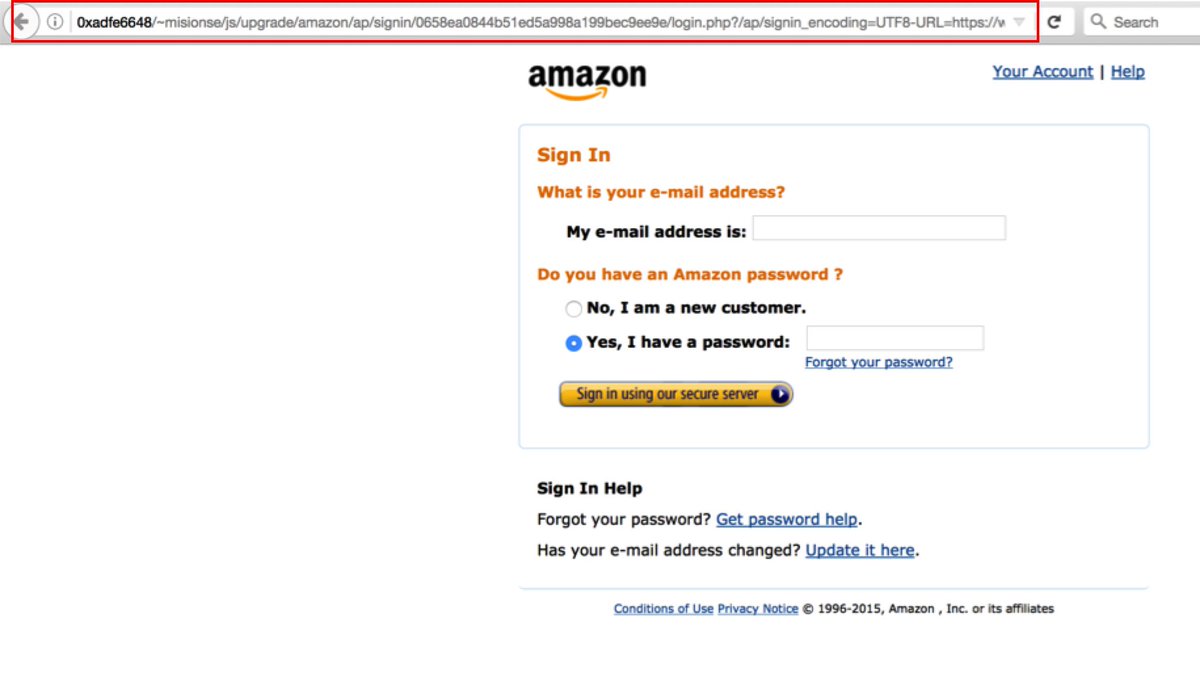
[ Attack ] FireEye researchers look at an Amazon phishing campaign https://www.fireeye.com/blog/threat-research/2016/07/amazon-credential-shipping.html https://t.co/KHjJBvTWCG
"FireEye 对 Amazon 钓鱼攻击事件的分析: https://t.co/fgE08YLkWk https://t.co/KHjJBvTWCG"
-

[ Browser ] #Firefox to block #Flash in August, disable by default in 2017 - http://ow.ly/kuif302u4gU https://t.co/QVG61kxoxD
" 从 8 月份开始,Firefox 将会对 Flash 的加载弹框确认,至 2017 年默认禁用 Flash,来自 ThreatPost 的报道: https://t.co/f6ZLUzx4WX Firefox 的官方说明: https://blog.mozilla.org/futurereleases/2016/07/20/reducing-adobe-flash-usage-in-firefox/ "
-

[ Browser ] Google fixed 48 bugs, including a sandbox escape, in the latest version of Chrome - http://ow.ly/c57l302u4cq
" Chrome 浏览器更新 52.0.2743.82 版本,本次更新修复了 48 个漏洞,来自 ThreatPost 的报道: https://t.co/axAJvx08pe 官方的公告: http://googlechromereleases.blogspot.com/2016/07/stable-channel-update.html "
-

[ Browser ] #pets16 New & old website fingerprinting attacks and defenses https://crysp.uwaterloo.ca/software/webfingerprint/ [Tor; code/papers] https://t.co/O7uAzTCCl2
" Web 指纹技术(Fingerprint)的攻击与防御: https://t.co/Si8K9SxoMm https://t.co/O7uAzTCCl2"
-

[ Conference ] Our OWASP AppSec EU16 presentation about "Static Code Analysis of Complex PHP Application Vulnerabilities" is online http://2016.appsec.eu/?page_id=914
" OWASP AppSec Europe 2016 会议的所有 PPT 下载: https://t.co/iWZB4eSYn6"
-

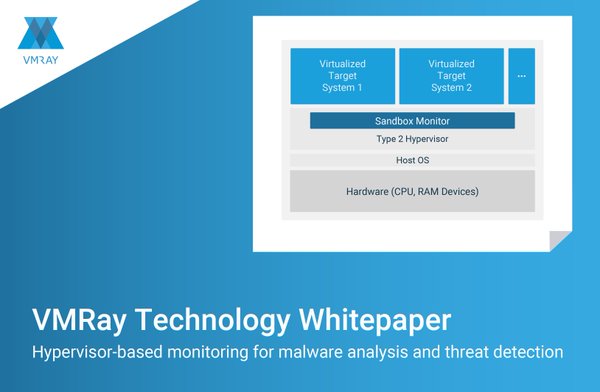
[ Detect ] Our #Whitepaper explains why a global aerospace giant, Dell SonicWALL & more use VMRay http://bit.ly/1SZJewH https://t.co/ZTQVxKwsxp
" VMRay 技术白皮书, VMRay 是一种基于 Hypervisor 的恶意软件分析和威胁检测技术: https://t.co/TGPDaClv2O https://t.co/ZTQVxKwsxp"
-

[ Fuzzing ] Major new features in AFL 2.20b: https://groups.google.com/forum/#!topic/afl-users/tTR5KcoecGs
" AFL Fuzz 2.20b 版本的两个新特性: https://t.co/e1VJrkI7w2"
-

[ Fuzzing ] New post: Fuzzing with AFL is an Art http://moyix.blogspot.com/2016/07/fuzzing-with-afl-is-an-art.html
" 基于 AFL 的 Fuzz 是一种艺术: https://t.co/5rVl26ghn3"
-

[ Linux ] Spawn shell like it's 90s again! A quick walk-through to gaining root privileges in NetBSD by abusing mail.local(8) http://akat1.pl/?id=2
" 像 90 年代那样弹 Shell - 滥用 mail.local(8),在 NetBSD 系统中获得 Root 权限: https://t.co/UhLFTQBrT2"
-

[ Linux ] Graphene - a library OS for Linux multi-process applications with Intel SGX support https://github.com/oscarlab/graphene
" Graphene - 提供 Intel SGX 支持的 Linux 多进程库实现, GitHub Repo: https://t.co/yVJVGwr9eO"
-

[ macOS ] [CVE-2016-4633] Another OS X Bug in Apple Graphics https://marcograss.github.io/security/apple/cve/2016/07/21/cve-2016-4633-apple-graphics-another-osx-bug.html
" OS X 图形处理相关的另一个漏洞(CVE-2016-4633): https://t.co/LcPxePz4eM"
-

[ Malware ] #Unit42 finds #PowerWare #ransomware spoofing Locky malware family http://bit.ly/2afQXq7
" PowerWare - PoshCoder 勒索软件家族的新变种,利用 PowerShell 加密文件,来自 Palo Alto 的分析: https://t.co/aqeeLmhYZZ"
-

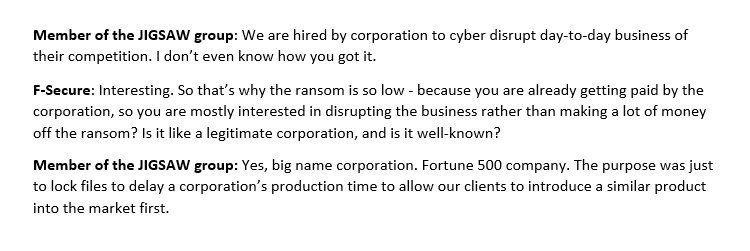
[ Malware ] Interesting detail from our latest report on the operations of ransom trojan gangs. More at http://safeandsavvy.f-secure.com/2016/07/18/why-these-online-criminals-actually-care-about-your-convenience/ https://t.co/jsUSedghE8
" 一些线上犯罪团伙一直在关注着大家的线上求助(FAQ、技术支持论坛): https://t.co/gUEBgCPcrS https://t.co/jsUSedghE8"
-

[ Malware ] Symantec report looks at trends in ransomware http://www.symantec.com/connect/blogs/report-organizations-must-respond-increasing-threat-ransomware https://t.co/3zuZ4bYfYk
"赛门铁克发布了一份关于勒索软件发展趋势的报告: https://t.co/81qjMwqqQv https://t.co/3zuZ4bYfYk"
-

[ Malware ] Source code of Cerber #ransomware reported to be traded in the Russian online black markets: http://bit.ly/29Hu1P7 #Cybercrime #InfoSec
" 据报道,Cerber 勒索软件的源码在俄罗斯黑市上交易︰ https://t.co/Y87xLfMQuH "
-

[ Network ] High Performance Browser Networking : https://hpbn.co/ (Online Book by @ igrigorik )
"高性能浏览器网络(在线图书)︰ https://t.co/M08qsHKROs "
-

[ OpenSourceProject ] Let's recheck Blender. http://www.viva64.com/en/b/0413/ (#blender, #pvsstudio, #devtools, #cpp, #opensource, #spoiler) https://t.co/FHqfV3vrUQ
" 用 PVS-Studio 工具对 Blender 3D 建模开源库的静态分析: https://t.co/gitxcQLTeo "
-

[ OpenSourceProject ] [CVE-2016-6265] MuPDF library use after free - https://marcograss.github.io/security/cve/2016/07/21/cve-2016-6265-mupdf-uaf.html
" MuPDF PDF 文件处理库的一个 UAF 漏洞(CVE-2016-6265),marcograss 说这是 Fuzz 其他库时顺便发现的: https://t.co/iNWYf78ra5"
-

[ Operating System ] How Qubes makes handling PDFs way safer https://micahflee.com/2016/07/how-qubes-makes-handling-pdfs-way-safer/ cc @ bartongellman
" Qubes 操作系统是如何使 PDF 的处理更安全的: https://t.co/mc5NiM7tRA "
-

[ Others ] Slides from my @ owaspnz talk "Deserialization, what could go wrong?" have been published: https://www.insomniasec.com/downloads/publications/Deserialization%20-%20%20What%20Could%20Go%20Wrong.pdf Happy to answer any Qs
" 反序列化,哪里可能出错,PDF︰ https://t.co/2Wh0JZdhjV "
-

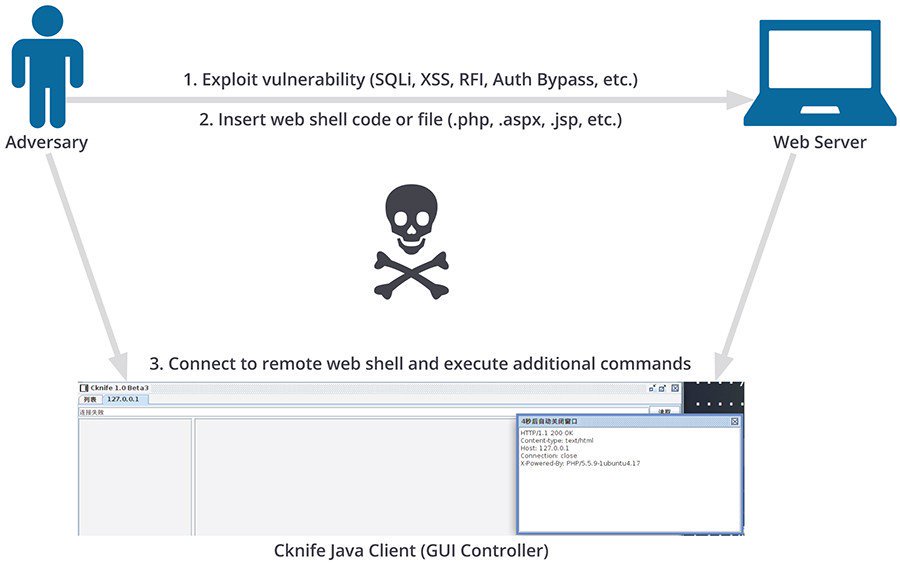
[ Pentest ] New Made-in-China Web Shell Threatens the #Security of Web Servers Worldwide http://ow.ly/dMnD302rKGI via @ Softpedia https://t.co/dhYijOI08g
" 两名中国研究员开源的一份 WebShell 对世界范围的 Web 服务器构成了威胁: https://t.co/dhYijOI08g "
-

[ Pentest ] "The History of Penetration Testing" http://resources.infosecinstitute.com/the-history-of-penetration-testing/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+infosecResources+%28InfoSec+Resources%29
" 渗透测试的历史,来自 InfoSec Blog: https://t.co/JxmOyXL71Z"
-

[ Popular Software ] Attacking Federated Skype for Business with PowerShell https://blog.netspi.com/attacking-federated-skype-powershell/
" 用 PowerShell 攻击商业版 Skype: https://t.co/rOqzDZyGXf "
-

[ Popular Software ] Git for Windows accidentally creates NTFS alternate data streams : http://latkin.org/blog/2016/07/20/git-for-windows-accidentally-creates-ntfs-alternate-data-streams/
"Git for Windows 意外地创建了一个 NTFS 备用数据流(Alternate Data Streams)︰ https://t.co/5buKSADdeu"
-

[ Programming ] The Hitchhiker’s Guide to Python : http://docs.python-guide.org/en/latest/
" Python 的《银河系漫游指南》: https://t.co/3o38lm55IU"
-

[ Protocol ] mini-tor : PoC implementation of tor protocol using Microsoft CryptoAPI : https://github.com/wbenny/mini-tor
" mini-tor - 基于 Microsoft CryptoAPI,实现的一款 Mini Tor 工具,可以用此工具访问洋葱网络(.onion)︰ https://t.co/Kg0tEsxU3c"
-

[ ReverseEngineering ] Reverse Engineering a Malicious MS Word Document https://sites.utexas.edu/iso/2016/07/08/reverse-engineering-a-malicious-ms-word-document/
" 一个恶意的 MS Office 样本的逆向分析: https://sites.utexas.edu/iso/2016/07/08/reverse-engineering-a-malicious-ms-word-document/ "
-

[ ReverseEngineering ] Reverse Engineering : Pokemon GO : https://www.fknsrs.biz/blog/reverse-engineering-pokemon-go.html
"逆向 Pokemon GO︰ https://t.co/AdquuTccbb"
-

[ Windows ] Windows File System Proxy - FUSE for Windows - https://github.com/billziss-gh/winfsp
" winfsp(Windows 文件系统代理) - Windows 系统的一根保险丝: https://t.co/mwvpINXNrH"
-

[ Windows ] Windows 10: What’s New in the Security System - https://securelist.com/blog/software/75427/windows-10-whats-new-in-the-security-system/ by @ swwwolf
"Windows 10 在安全方面的新动态, Kaspersky 这篇 Blog 的链接失效了: https://t.co/i1hAhxLMh9 可以通过 Google 的快照查看: https://webcache.googleusercontent.com/search?q=cache:rZaW28XBVkQJ:https://securelist.com/blog/software/75427/windows-10-whats-new-in-the-security-system/+&cd=4&hl=zh-CN&ct=clnk&gl=cn 另外微软官方也有一篇相关的 Blog: https://technet.microsoft.com/en-us/itpro/windows/whats-new/security "