腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] mosec2016 in shanghai "Advanced Android Root:How To Bypass PXN" slide https://github.com/jianqiangzhao/mosec2016
" Android Root 利用技术漫谈 - 绕过 PXN,来自 360 研究员在 MoSec 2016 会议的演讲: https://t.co/i2VtlP2G7c"
-

[ Android ] The slide and exploit of 《A Way of Breaking Chrome’s Sandbox in Android》in MoSec 2016 https://github.com/secmob/mosec2016
" 安卓 Chrome 沙箱逃逸的一种姿势,来自前两天龚广在 MoSec 2016 会议的演讲: https://t.co/NUsxbdWjpf"
-

[ Backdoor ] @ harmj0y I also fixed up/expanded my old code that backdoors .LNKs, adding enumeration options as well https://gist.github.com/HarmJ0y/984951d583d90ecee0f607e0b2849d1c
" 基于 LNK 快捷方式的后门实现: https://t.co/XeGK9aJdlU"
-

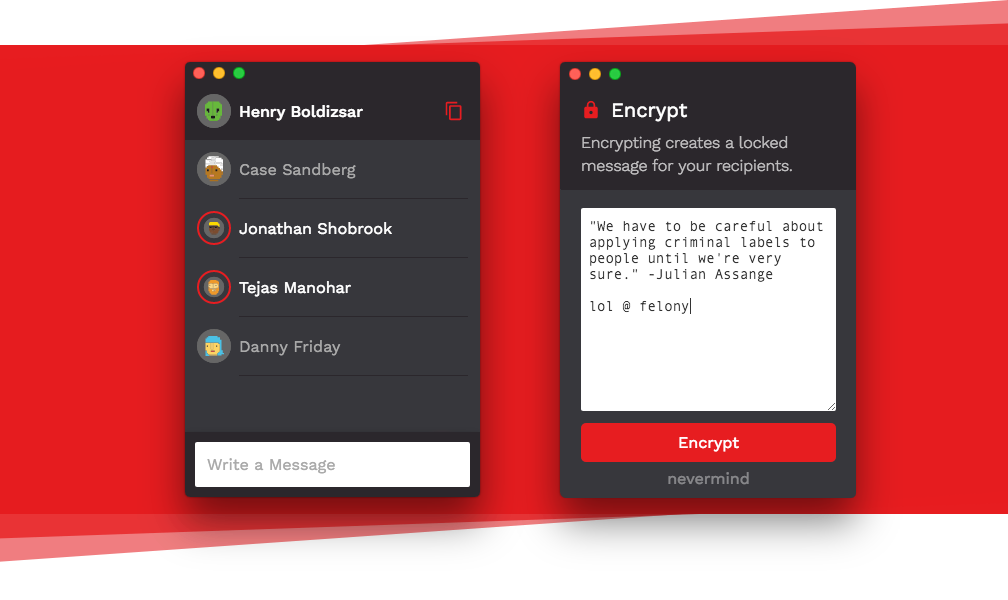
[ Crypto ] Felony : an open-source pgp keychain built on the modern web : https://github.com/henryboldi/felony https://t.co/ns5qLS5kHm
" Felony - 一款开源的 PGP 加密工具: https://t.co/6W8bn024bl https://t.co/ns5qLS5kHm"
-

[ Crypto ] Recently, I wrote this tool to analyze database dumps with unknown hashing algorithms: https://alexaltea.github.io/hasher/. Have fun!
" HASH 算法自动化检测工具,可以用于分析泄漏的密码 Hash 值︰ https://t.co/lchNaRu6ak "
-

[ Exploit ] Windows Exploitation Resources CyberPunk » Exploitation Tools https://n0where.net/awesome-windows-exploitation-resources/
"Windows 漏洞利用相关的文章收集: https://t.co/xDOuCwGEOP 推荐一个更全面的: https://www.gitbook.com/book/arthurgerkis/it-sec-catalog 还有一个 Linux x86 的: https://sploitfun.wordpress.com/2015/06/26/linux-x86-exploit-development-tutorial-series/ "
-

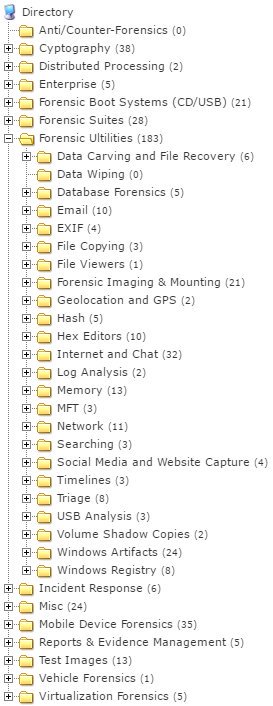
[ Forensics ] A collection of Digital Forensics and Incident Response tools by @ dfirtv http://dfir.training/index.php/tools/ #DFIR #Forensic https://t.co/OnnyUdgrub
" 数字取证与应急响应工具列表: https://t.co/9GrC54GPLO https://t.co/OnnyUdgrub"
-

[ iOS ] Tool for statically reconstructing the IOKit classes hierarchy from iOS kernelcache dumps https://github.com/jndok/iokit-dumper-arm64
" iokit-dumper-arm64 - 从 iOS 内核 KernelCache Dump 文件中重建类继承关系的静态工具: https://t.co/rBAzVGanB5"
-

[ IoTDevice ] UPC UBEE EVW3226 WPA2 Password Reverse Engineering - https://deadcode.me/blog/2016/07/01/UPC-UBEE-EVW3226-WPA2-Reversing.html
"逆向 UPC UBEE EVW3226 路由器的默认密码生成算法: https://t.co/V7w94VvT5I"
-

[ OpenSourceProject ] Pushed my libical fuzzing results to github. Mozilla either can’t or won’t repro, marked as low sev. https://github.com/brandonprry/ical-fuzz
"Brandon Perry 对 libical 开源库的 Fuzz 结果: https://t.co/ToSQ9vHrHY"
-

[ Others ] Sysinternal tools now run on NanoServer! Here is @ markrussinovich and Andrew Mason demonstrating them: https://channel9.msdn.com/shows/defrag-tools/defrag-tools-164-sysinternals-nano
" Sysinternals for Nano Server︰ https://t.co/Ef6V0a9UKr"
-

[ Others ] Wget Arbitrary Commands Execution : https://blogs.securiteam.com/index.php/archives/2701
"Wget 1.17 及之前版本任意命令执行漏洞︰ https://t.co/oVKzqy6gwE"
-

[ Others ] Turning a GPS-based dating application into a tracking system : http://www.synacktiv.ninja/ressources/ndh_2k16_gps_dating_app.pdf (pdf)
" 针对 GSM、GPRS 的攻击实践︰ https://t.co/0G0zPxlrl6 "
-

[ Others ] Blogged! Three Google bounties thanks to simple Google Caja sandbox escapes (with unicode escapes) http://blog.bentkowski.info/2016/07/xss-es-in-google-caja.html #xss #bugbounty
" Google Caja 编译器的 3 个 XSS 漏洞: https://t.co/r0zShbWOec "
-

[ Others ] New tech report: All Your Cards Are Belong To Us: Understanding Online Carding Forums http://ow.ly/EfhW301TwHe
" All Your Cards Are Belong To Us - 地下交易论坛研究报告: https://t.co/Gng20fmIS0"
-

[ Others ] Unravelling Code Injection in Binaries : https://suchakra.wordpress.com/2016/07/03/unravelling-code-injection-in-binaries/ cc @ tuxology https://t.co/KhAMSwATHe
"分离二进制文件中的代码注入︰ https://t.co/5uIz7wWtqQ https://t.co/KhAMSwATHe"
-

[ Pentest ] Few goodies for everyone today- first a PowerSploit cheat sheet https://github.com/HarmJ0y/CheatSheets/blob/master/PowerSploit.pdf
" PowerSploit 使用手册: https://t.co/3igArRkone"
-

[ ReverseEngineering ] dynStruct - tool for structure recovering and memory usage analysis based on DynamoRIO. Use capstone https://github.com/ampotos/dynStruct
"dynStruct - 基于 DynamoRIO,可以还原数据结构、分析内存使用情况的工具: https://t.co/e8CAOLhCKJ"
-

[ SecurityProduct ] SSD Advisory – Untangle NG Firewall Remote Command Execution https://blogs.securiteam.com/index.php/archives/2724
" Untangle 防火墙远程命令执行漏洞: https://t.co/Hz4E8R52D0"
-

[ SecurityProduct ] w0w, a new Unicorn-based AntiVirus by @ quangnh89 with an interesting approach: scan for malware at emulation time! https://github.com/develbranch/TinyAntivirus
" TinyAntivirus - 一款基于 Unicorn 模拟器的轻量级反病毒软件: https://t.co/ZzVdr6K70B"
-

[ SecurityProduct ] New advisory published: a directory traversal bug in Symantec Endpoint Protection Manager discovered by Che Lin Law https://labs.mwrinfosecurity.com/advisories/symantec-endpoint-protection-manager-directory-traversal/
" Symantec Endpoint Protection Manager 目录穿越漏洞(CVE-2016-5307): https://t.co/Z9i6nv7uRU"
-

[ ThreatIntelligence ] Last week I released OSTrICa - #opensource #threat #intelligence collector on #github http://bit.ly/29hImG3 #malware #itsecurity
" OSTrICa - 一款开源的威胁情报收集工具: https://t.co/GqnuyMYI0q "
-

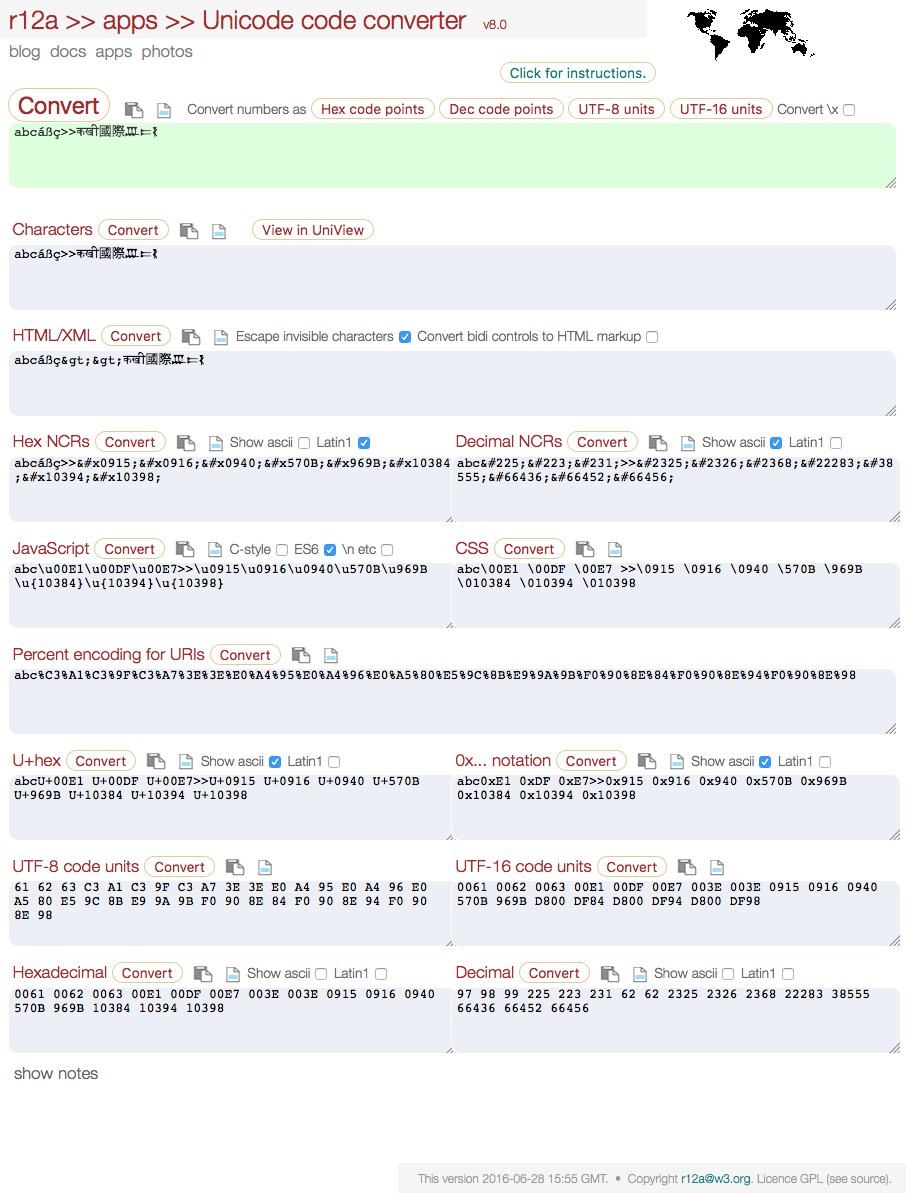
[ Tools ] Unicode Converter v8 released. Adds ES6 supp char escapes, instant option changes etc, see http://rishida.net/blog/?p=1733 https://t.co/FZLGvxHfkR
"Unicode 编码在线转换工具: https://t.co/eOKgFV284X https://t.co/FZLGvxHfkR"
-

[ Web Security ] Identifying RPO : http://blog.innerht.ml/rpo-gadgets/
" 寻找 RPO(Relative Path Overwrite) Gadgets: https://t.co/TYAcOsKlNj"
-

[ Windows ] Intercepting DLL libraries calls - API hooking in practice : https://www.pelock.com/articles/intercepting-dll-libraries-calls-api-hooking-in-practice
" Windows DLL API Hook 实现︰ https://t.co/E5RoHQyRuh"
-

[ Windows ] Great read: From hibernated computer to SYSTEM on a full-disk-encrypted Windows laptop 1) https://blog.ahmednabeel.com/from-zero-to-system-on-full-disk-encrypted-windows-system/ 2) https://blog.ahmednabeel.com/from-zero-to-system-on-full-disk-encrypted-windows-system-part-2/
" 昨天推送过《在全磁盘加密的 Windows 系统中实现从零到 SYSTEM》的 PPT,作者接着写了两篇 Blog, Part 1: https://t.co/mAgIGYTKLg Part 2: https://t.co/bYr6Db4u1E"