腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] PunkeyPOS might have already stolen millions of payment card numbers http://securityaffairs.co/wordpress/48742/malware/punkeypos-impacts-millions-via-infected-restaurants.html
"PandaLabs 安全专家表示:PunkeyPOS 恶意软件已经盗取了 120 万独立用户的支付卡数据: https://t.co/qMZL4y2VhH"
-

[ Attack ] Locky Ransomware is back! 49 domains compromised! http://securityaffairs.co/wordpress/48725/malware/locky-ransomware-back.html
" Locky 勒索软件归来,49 个域名被攻破,来自 SecurityAffairs 的报道: https://t.co/GoNTEupG09"
-

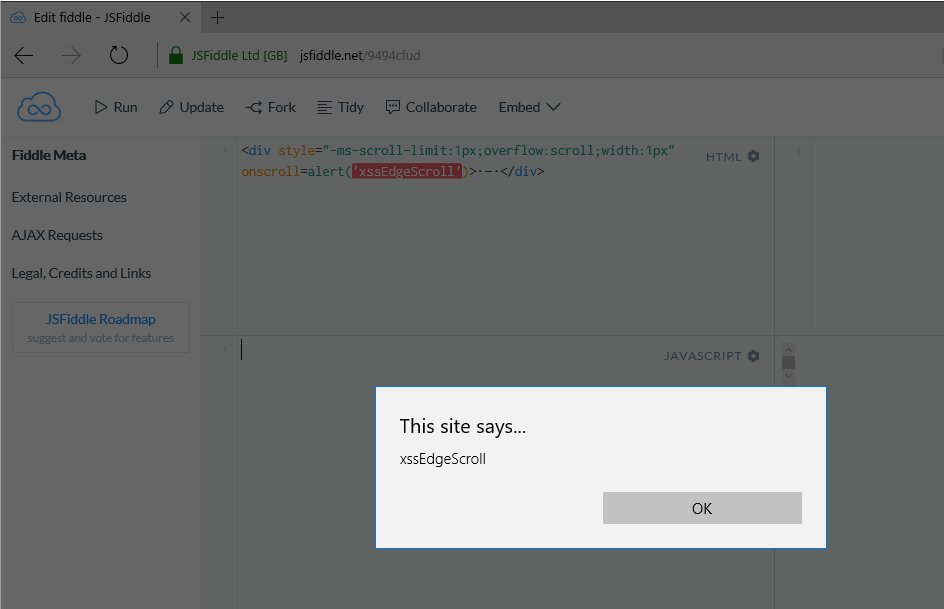
[ Browser ] No UI #XSS vector Edge, MSIE10-11 <div style="-ms-scroll-limit:1px;overflow:scroll;width:1px" onscroll=alert('xss')> https://t.co/ZHvLVK37qC
" 影响 Edge、IE 10-11 的一个 XSS 攻击向量: https://t.co/ZHvLVK37qC"
-

[ Debug ] Intro to kernel debugging (Part 1) : https://blogs.msdn.microsoft.com/meason/2016/06/17/intro-to-kernel-debugging-1/ ,Part 2 : https://blogs.msdn.microsoft.com/meason/2016/06/17/intro-to-kernel-debugging-2/
" MSDN Blog 一篇介绍内核调试的文章, Part 1︰ https://t.co/G9VuFeXCA3 Part 2: https://t.co/LcoBxNQBpY"
-

[ Fuzzing ] fuzzing using a neural network-- I had been planning to try this but these guys got to it first! http://cifasis.github.io/neural-fuzzer/
"Neural-Fuzzer - 基于神经网络的 Fuzzer: https://t.co/CHShZ7MJ0j"
-

[ iOS ] #idevicerestore now works with iOS 10, plus some other fixes: https://github.com/libimobiledevice/idevicerestore
" iOS 固件恢复/更新工具 idevicerestore 支持 iOS 10 了︰ https://t.co/VtaGhgPpPE"
-

[ macOS ] Guide to Securing Apple OS X 10.10 Systems for IT Professionals: http://csrc.nist.gov/publications/drafts/800-179/sp800_179_draft.pdf(pdf)
" Apple OS X 10.10 系统安全加固指南 ︰ https://t.co/Dmk3ue95uQ"
-

[ Malware ] Top Exploit Kit Activity Roundup https://www.zscaler.com/blogs/research/top-exploit-kit-activity-roundup
" 顶级 Exploit Kits 汇总: https://t.co/e1evumng7s"
-

[ Malware ] How Did the Russian Abuse Twitter as C&C in Hammertoss Malware? Python Answers http://resources.infosecinstitute.com/how-did-the-russian-abuse-twitter-as-cc-in-hammertoss-malware-python-answers/
"俄罗斯的一款恶意软件 Hammertoss 是如何滥用 Twitter 作为 C&C 信道的: https://t.co/RGPdAagSaO"
-

[ Network ] Ettercap Man In The Middle Attack + SSL strip : https://sinister.ly/Thread-Ettercap-Man-In-The-MIddle-Attack-SSL-Strip
" 基于 Ettercap 和 SSL Strip 工具的中间人攻击 ︰ https://t.co/FyWFOZh8iK"
-

[ OpenSourceProject ] AsteroidOS : An open-source operating system for smartwatches: http://asteroidos.org/
"AsteroidOS - 一个开源的智能手表操作系统: https://t.co/jVSgEnTgQa"
-

[ Others ] Bypassing Protections: Exploiting Activation to Access Sensitive Data http://reverseengineeringtips.blogspot.com/2016/06/bypassing-protections-exploiting.html
" 绕过 ChessArbiter 的激活保护,访问服务器存储的其他用户的敏感信息: https://t.co/zhkrtzYQHh"
-

[ Pentest ] Cloakify Toolset : Data Exfiltration In Plain Sight; Evade DLP/MLS Devices & AV detection : https://github.com/trycatchhcf/cloakify
"Cloakify 工具集 - 眼皮底下偷数据的工具,可以逃逸 DLP/MLS、杀软的检测 ︰ https://t.co/V1fei2kMKG"
-

[ Web Security ] Utilizing Multi-byte Characters To Nullify SQL Injection Sanitizing http://howto.hackallthethings.com/2016/06/using-multi-byte-characters-to-nullify.html
"利用多字节字符使 SQL 注入检查失效: https://t.co/6nqtXDiaRd"