腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Attacks and Defence on Android Free Floating Windows - https://dl.acm.org/citation.cfm?id=2897897
" Android 自由浮动窗口的攻击与防御,来自 ACM 数字实验室的 Paper: https://t.co/1Wmy53JTuB"
-

[ Android ] Interested to read this: Consumer-centric android application repackaging detection (http://www.sciencedirect.com/science/article/pii/S0167739X16301327) from @ lcavallaro
" 以消费者为中心的 Android 应用重打包(Repackaging)检测技术: https://t.co/GlejBWBr0F "
-

[ Android ] LG Now Has Its Own Security Bulletin Like Google And Samsung http://www.androidpolice.com/2016/06/10/lg-now-security-bulletin-like-google-samsung/ https://t.co/SimZJsTfLL
"像 Google 和三星一样,LG 也有自己的安全公告网站了: https://t.co/tunxVQuZ8T https://t.co/SimZJsTfLL"
-

[ Android ] Android /system/bin/sdcard Stack Buffer Overflow https://packetstormsecurity.com/files/137404/GS20160609225743.tgz
"Android /system/bin/sdcard 栈缓冲区溢出漏洞(CVE-2016-2494),来自 Project Zero Issue 798: https://bugs.chromium.org/p/project-zero/issues/detail?id=798 "
-

[ Attack ] Latest Intelligence for May 2016 http://www.symantec.com/connect/ko/blogs/latest-intelligence-may-2016-0
" Symantec 安全情报报告(2016.05): https://t.co/HHEjPOF1bO"
-

[ Browser ] Window Hijacking: Using JavaScript to open a new tab then change location of tab after an arbitrary period of time : https://github.com/dxa4481/windowHijacking
" WindowHijacking - 浏览器新标签页窗口劫持 ︰ https://t.co/OtynVYpZNN"
-

[ Browser ] This mobile performance paper is always worth re-reading: http://sealedabstract.com/rants/why-mobile-web-apps-are-slow/
" 为什么手机浏览器那么慢 ︰ https://t.co/aebWdNEhwc"
-

[ Cloud ] Distributed honeypot deployment in the cloud. H/T @ MalwareMustDie http://simonclary.com/wp-content/uploads/2016/05/How-feasible-is-a-distributed-honeypot-deployment-in-the-cloud-v-1.pdf (PDF) cc: @ binitamshah https://t.co/NdjvPoIzua
" 在云环境中部署分布式蜜罐的可行性, Paper: https://t.co/1ILzJH5qQs https://t.co/NdjvPoIzua"
-

[ Defend ] Intel Release New Tech Specifications to Protect Against ROP Attacks : https://blogs.intel.com/evangelists/2016/06/09/intel-release-new-technology-specifications-protect-rop-attacks/ ,CET Details: https://software.intel.com/sites/default/files/managed/4d/2a/control-flow-enforcement-technology-preview.pdf (pdf)
" Intel 公开了一种用于对抗 ROP 攻击的新技术,称为 CET︰ https://t.co/ygIH1QWnc3 关于 CET 的技术细节︰ https://t.co/FBWAKrlpJi "
-

[ Detect ] FUNNY HONEY – TRACKING HACKERS IN CYBERSPACE : DFIR BLOG https://dfir-blog.com/2016/05/17/funny-honey-tracking-hackers-in-cyberspace-part1/
" 这篇 Blog 讲通过蜜罐监控网络攻击活动。作者听说蜜罐捕获的攻击活动很多都来自中国,于是他在 Google 云上搭建了 6 个蜜罐,看看是不是这么回事: https://t.co/ooDT0YeqaY"
-

[ Fuzzing ] Open Source Fuzzers list : https://www.peerlyst.com/posts/resource-open-source-fuzzers-list
" 开源 Fuzzer 列表,来自 PeerLyst Blog︰ https://t.co/t3XXcjYl9y"
-

[ Fuzzing ] delta debugging on afl crashes https://github.com/MarkusTeufelberger/afl-ddmin-mod readings:"Reducers are Fuzzers" http://blog.regehr.org/archives/1284 paper http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.126.6907&rep=rep1&type=pdf
" afl crash 增量调试: https://t.co/00SSPgyhuu Reducers are Fuzzers: https://t.co/8XOHWGZ6R3 Paper: https://t.co/zx5w1EFxWR"
-

[ Hardware ] Drone Bypass : http://blog.ptsecurity.com/2016/06/phd-vi-how-they-stole-our-drone.html https://t.co/h77SUtqKF9
" 他们是如何偷走我们的无人机的,这篇 Blog 是对 PHDays 会议无人机劫持攻击的技术介绍 ︰ https://t.co/u3OM8n8XKh https://t.co/h77SUtqKF9"
-

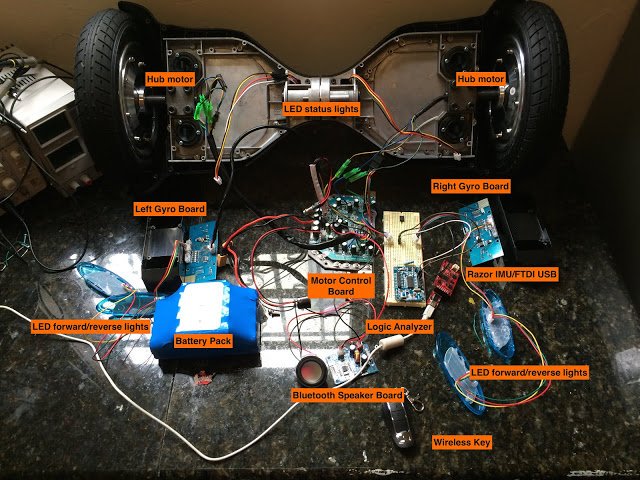
[ Hardware ] How I hacked the Self Balancing Scooter : http://drewspewsmuse.blogspot.in/2016/06/how-i-hacked-self-balancing-scooter.html https://t.co/NR2MHlFTAL
"看我如何黑掉自平衡滑板车︰ https://t.co/tOD4nwtVjl https://t.co/NR2MHlFTAL"
-

[ Hardware ] Computer Engineering (A DEC View of Hardware Systems Design) : http://research.microsoft.com/en-us/um/people/gbell/Computer_Engineering/index.html #FYI #b2b
" 从 DEC 的角度看计算机硬件系统设计︰ https://t.co/nQB0tPoVQu DEC 即 Digital Equipment Corporation,是美国一家老牌的电脑公司"
-

[ Hardware ] Hacking the CampCopter (@ ToorCamp) slides are up: http://greatscottgadgets.com/slides/ossmann-spill-toorcamp-2016.pdf
" Hacking CampCopter (无人机)︰ https://t.co/f0uzD4MMRN"
-

[ IoTDevice ] Practical Reverse Engineering http://jcjc-dev.com/2016/04/08/reversing-huawei-router-1-find-uart/ http://jcjc-dev.com/2016/04/29/reversing-huawei-router-2-scouting-firmware/ http://jcjc-dev.com/2016/05/23/reversing-huawei-3-sniffing/ http://jcjc-dev.com/2016/06/08/reversing-huawei-4-dumping-flash/
" 之前推送过 Juan Carlos Jimenez 写的 3 篇《逆向华为路由器》系列文章,最近他又继续写了第 4 篇:《 Dump 华为路由器的 Flash》: http://jcjc-dev.com/2016/06/08/reversing-huawei-4-dumping-flash/ "
-

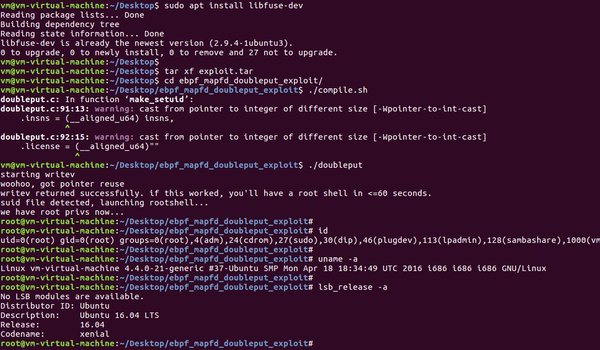
[ Linux ] Linux Kernel 4.4.x (Ubuntu 16.04) - Use-After-Free vulnerability https://www.exploit-db.com/exploits/39772/ #exploitdev #vunl #infosec https://t.co/UFqyeOobgv
"Linux 内核 4.4.x (Ubuntu 16.04) BPF BPF_PROG_LOAD double-fdput() UAF(CVE-2016-4557): https://t.co/cGpPRAkxbw https://t.co/UFqyeOobgv"
-

[ Mac OS X ] OS X exploitable kernel NULL pointer dereference in IOAudioEngine https://bugs.chromium.org/p/project-zero/issues/detail?id=776#c_ts1465491638
"OS X 内核 IOAudioEngine 一个可利用的空指针解引用漏洞(CVE-2016-1821): https://t.co/LLiRH9aS5V"
-

[ Mac OS X ] OS X Kernel GeFore GPU Driver Stack Buffer Overflow https://packetstormsecurity.com/files/137394/GS20160609224302.tgz
" OS X 内核 GeForce GPU 驱动栈缓冲区溢出漏洞(CVE-2016-1861),来自 Project Zero Issue 724: https://bugs.chromium.org/p/project-zero/issues/detail?id=724 "
-

[ Mac OS X ] OS X / iOS Kernel IOHDIXControllerUserClient Use-After-Free https://packetstormsecurity.com/files/137395/GS20160609224508.tgz
"OS X/iOS 内核 IOHDIXControllerUserClient UAF(CVE-2016-1807),来自 Project Zero Issue 732: https://bugs.chromium.org/p/project-zero/issues/detail?id=732 "
-

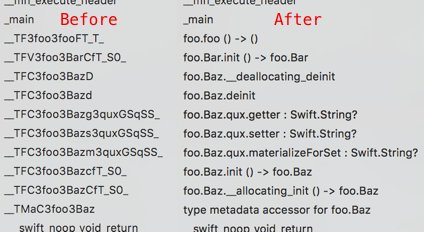
[ Mac OS X ] Just released the Hopper plugin I wrote for demangling Swift symbols https://github.com/keith/hopper-swift-demangle https://t.co/DhEcPPnYYt
" OS X 逆向工具 Hopper 用于调试符号 Demangle 的插件: https://t.co/hzVeNb8Oiu https://t.co/DhEcPPnYYt"
-

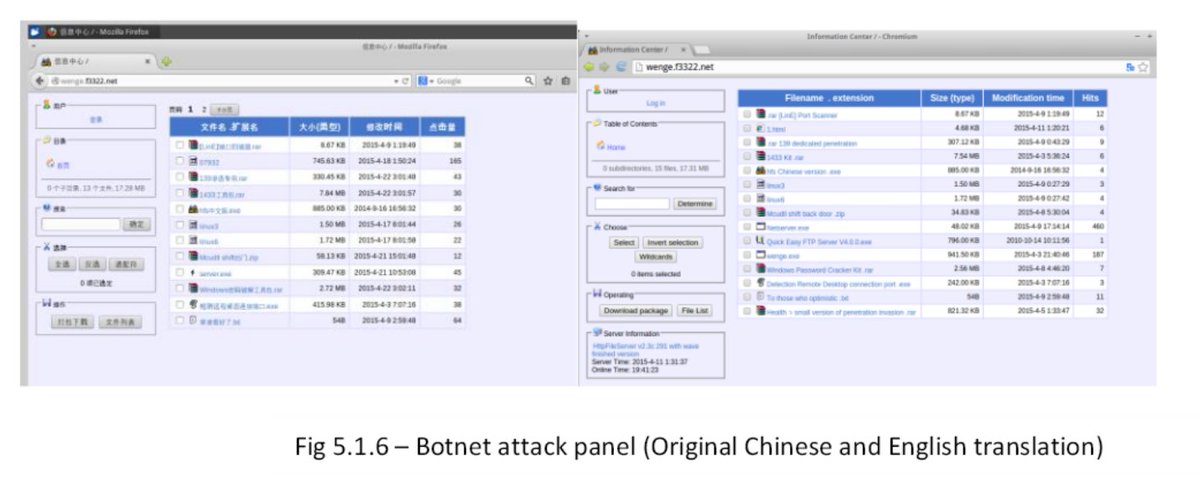
[ Malware ] Necurs Botnet, one of the world’s largest malicious architecture has vanished http://securityaffairs.co/wordpress/48248/cyber-crime/necurs-botnet.html
"Necurs 僵尸网络 - 世界最大的恶意软件基础设施之一,6 月 1 号之后消失了,来自 SecurityAffairs 的报道: https://t.co/hIJoK1qWpZ"
-

[ Malware ] New decryption utilities further bury #TeslaCrypt #ransomware https://threatpost.com/decryption-utilities-unlock-files-encrypted-by-all-teslacrypt-versions/118602/
" Kaspersky 的工具可以解密各版本 TeslaCrypt 污染后的文件: https://t.co/Y6IvfWqZxE"
-

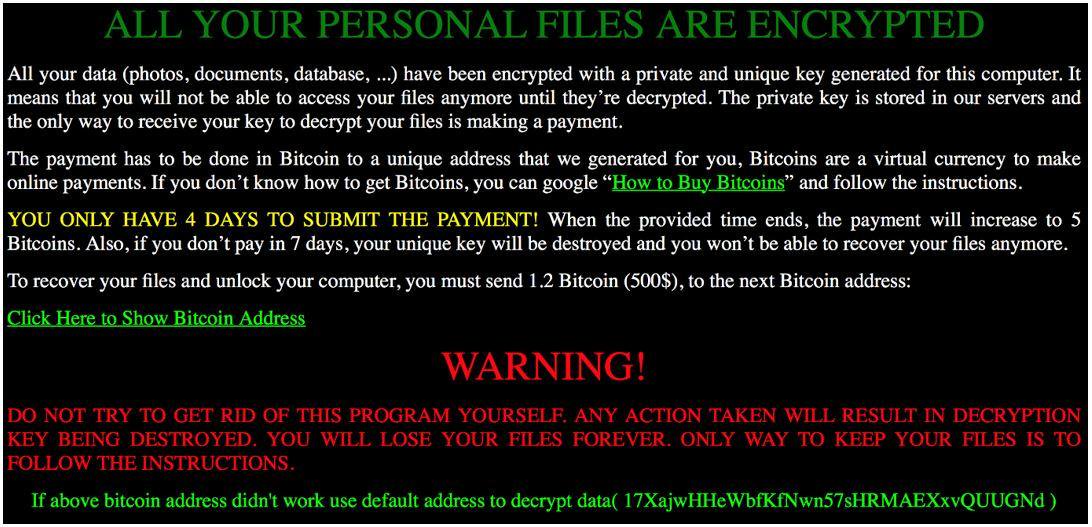
[ Malware ] Petya and Mischa – Ransomware Duet (part 2) https://blog.malwarebytes.org/threat-analysis/2016/06/petya-and-mischa-ransomware-duet-part-2/
" Petya 和 Mischa 勒索软件二重奏(Part 2),来自 MalwareBytes Blog: https://t.co/dcclsnOhHP"
-

[ Malware ] #Zcrypt expands reach as "virus #ransomware," uses same Nullsoft installer as CryptoLocker http://intel.ly/1UjUwgK https://t.co/SSgnzk1jpz
" McAfee Blog 对 Zcrypt 勒索软件的分析: https://t.co/kmHzEbrleZ https://t.co/SSgnzk1jpz"
-

[ Malware ] Reverse-engineering DUBNIUM | @ msftmmpc #APT #Malware Analysis https://blogs.technet.microsoft.com/mmpc/2016/06/09/reverse-engineering-dubnium-2/
" DUBNIUM(也被称为 DarkHotel)APT 样本逆向分析,来自微软 Blog: https://t.co/9pUjO1YoeO"
-

[ MalwareAnalysis ] NCC Group Cyber Defense Operations Technical Note and more: on Sakula DLL Planting Analysis - https://github.com/nccgroup/Cyber-Defence/tree/master/Technical%20Notes/Sakula by @ edeca
" Sakula 恶意软件 DLL 劫持技术分析,来自 NCC Group 的 GitHub Repo: https://t.co/khEEtWMpky "
-

[ Network ] Optimizing TLS over TCP to reduce latency http://blog.cloudflare.com/optimizing-tls-over-tcp-to-reduce-latency/
" 通过 TCP 优化 TLS,以减少传输延迟,来自 CloudFlare Blog: https://t.co/UPsfRfvmES"
-

[ OpenSourceProject ] Two fresh penetration reports of ours were published via MOSS. Tested were PCRE and libjpeg-turbo - enjoy: https://wiki.mozilla.org/MOSS/Secure_Open_Source/Completed
" PCRE 和 libjpeg-turbo 库安全审计报告,来自 Mozilla MOSS 计划︰ https://t.co/meh2xK97Wn"
-

[ OpenSourceProject ] Talos Blog: Vulnerability Spotlight: PDFium Vulnerability in Google Chrome Web Browser http://tinyurl.com/j3ase9g
" Cisco Talos 团队研究员在 Chrome 浏览器的 PDFium 组件中发现了一个堆溢出漏洞(CVE-2016-1681): https://t.co/XOo2Aapsos "
-

[ Others ] Slides for my OWASP Gothenburg talk are here https://speakerdeck.com/0xtero/security-for-enterprise-hobbits
" 0xtero 在 OWASP 哥德堡会议关于企业安全的演讲: https://t.co/zV5QIRwIuM"
-

[ Others ] DRAMA Reverse-Engineering Tool and Side-Channel Tools : https://github.com/IAIK/drama cc @ lavados
" DRAMA - Intel DRAM 寻址功能存在新的边信道攻击面,来自 GitHub Repo︰ https://t.co/wvG28MtQCz "
-

[ Others ] "XSS vulnerabilities account for 66% of valid submissions" is why we're pushing hard on CSP in @ mozsec . src: https://pages.bugcrowd.com/hubfs/PDFs/state-of-bug-bounty-2016.pdf
" Bug Bounty 项目的现状,来自 BugCrowd 的报告。报告中提到:XSS 漏洞占据有效提交的 66%: https://t.co/ibYXZ8tqMC"
-

[ Others ] Build and run your unikernel in python with unik. Great project : https://github.com/emc-advanced-dev/unik/blob/master/docs/getting_started_python3.md
" 利用 Python 和 Unik 工具运行 UniKernel ︰ https://t.co/XsjwEtmtxG"
-

[ Pentest ] Dissecting Veil-Evasion Powershell Payloads and Converting to a Bind Shell : http://threat.tevora.com/dissecting-veil-evasion-powershell-payloads-and-converting-to-a-bind-shell/
" Veil-Evasion PowerShell Payloads 剖析,以及如何将 TCP 反弹 Payload 替换成 TCP Bind Shell︰ https://t.co/RvTEK6qnNv"
-

[ Pentest ] Mapping your LAN from a web browser: http://blog.beefproject.com/2016/06/mapping-your-lan-from-web-browser.html
" 浏览器攻击框架 BeEF 最近新增加了一个扩展,用于映射局域网网络拓扑︰ https://t.co/Dcf657cCg3"
-

[ Popular Software ] Apache Struts REST Plugin With Dynamic Method Invocation Remote Code Execution https://packetstormsecurity.com/files/137375/struts_dmi_rest_exec.rb.txt
"Apache Struts REST 插件动态方法执行 RCE(CVE-2016-3087), Metasploit 攻击模块: https://t.co/AzGZ38Mh2s"
-

[ ReverseEngineering ] awesome reversing resources by @ 0xtyh https://github.com/0xtyh/awesome-reversing
" 逆向相关的资料收集整理: https://t.co/MU97yC7mGj"
-

[ ReverseEngineering ] Using IDAPython to Make Your Life Easier: Part 6 http://researchcenter.paloaltonetworks.com/2016/06/unit42-using-idapython-to-make-your-life-easier-part-6/
" IDAPython 让你的生活更轻松 Part 6,来自 Palo Alto Blog: https://t.co/bXIDuJjtwn Part 5: http://researchcenter.paloaltonetworks.com/2016/01/using-idapython-to-make-your-life-easier-part-5/ "
-

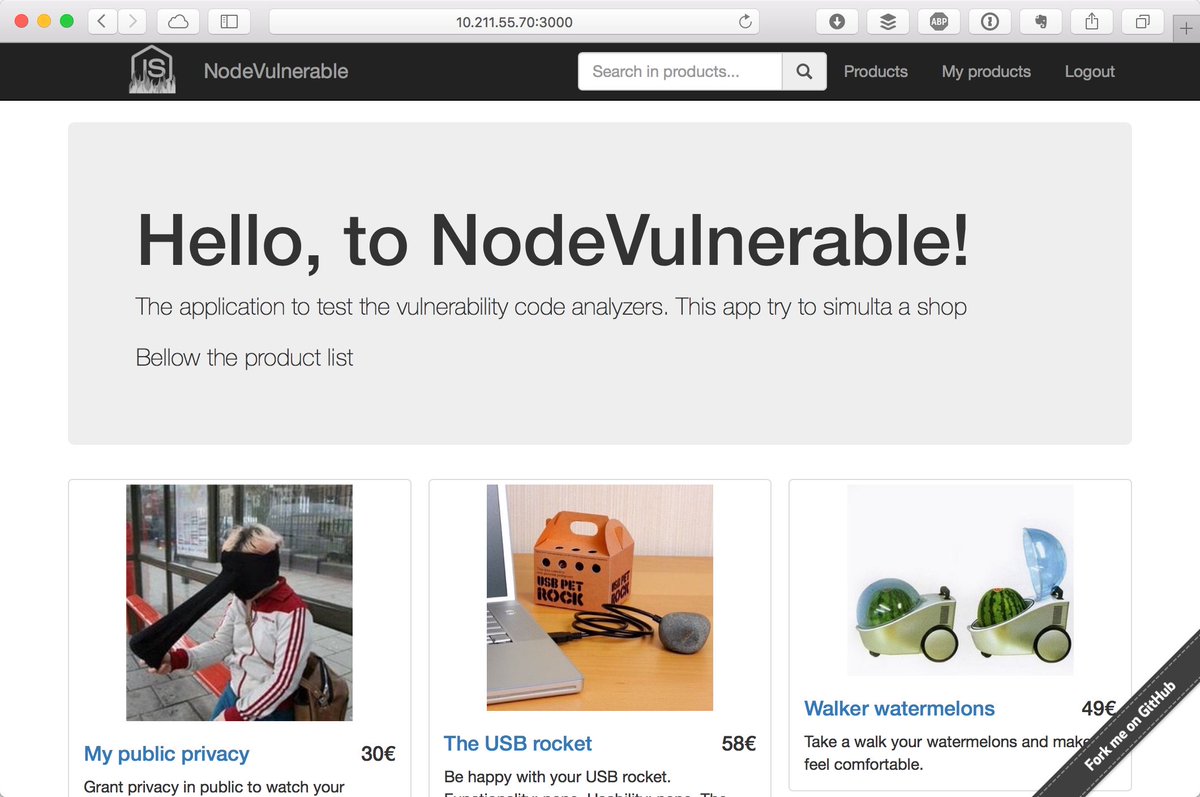
[ Tools ] [NEW PROJECT] A very vulnerable web in NodeJS for measure security analysis tools #nodejs https://github.com/cr0hn/vulnerable-node https://t.co/92FHLP2Js2
" vulnerable-node - 一个存在漏洞的 NodeJS Web 站点,该项目主要用于测试 NodeJS 漏洞和工具: https://t.co/83Nu4tEnM0 https://t.co/92FHLP2Js2"
-

[ Tools ] I wrote a python script to parse the RecentDocs key: http://www.raptir.com/2016/06/recentdocs-python-script.html Also, my first blog post!
" 用于导出 '最近打开文档' 列表的脚本 ︰ https://t.co/PDz6W4FgN6 "