腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] CVE-2016-2061 PoC: https://goo.gl/a3uR92 CVE-2016-2469 PoC: https://goo.gl/QPPri2 CVE-2016-2465 / 2489 PoC: https://goo.gl/jxWZCr
" 研究员 Scott Bauer 几个小时前公开了 Android 内核多个漏洞的 PoC, CVE-2016-2061: https://t.co/RuRH55JOSX CVE-2016-2469: https://t.co/A4Kync14Lk CVE-2016-2465/2489: https://t.co/GUCZQ9Vpr1"
-

[ Android ] Mobile Security News Update June 2016 https://www.mulliner.org/blog/blosxom.cgi/security/mobile_security_news_update_june2016.html #mobilesecurity
"移动安全动态(2016 年 6 月版),来自 Mulliner Blog: https://t.co/KZteEsCuYX "
-

[ Android ] Google patches Mediaserver, Qualcomm drivers, libwebm in #Android Security Bulletin https://threatpost.com/latest-android-security-bulletin-heavy-on-critical-qualcomm-flaws/118479/ via @ threatpost
" Android 发布 6 月份补丁更新,本次修复了 Mediaserver、高通驱动、libwebm 的共计 6 个严重漏洞,来自 ThreatPost 的报道: https://t.co/Z9CFbHIXGV 来自官方的公告: https://source.android.com/security/bulletin/2016-06-01.html "
-

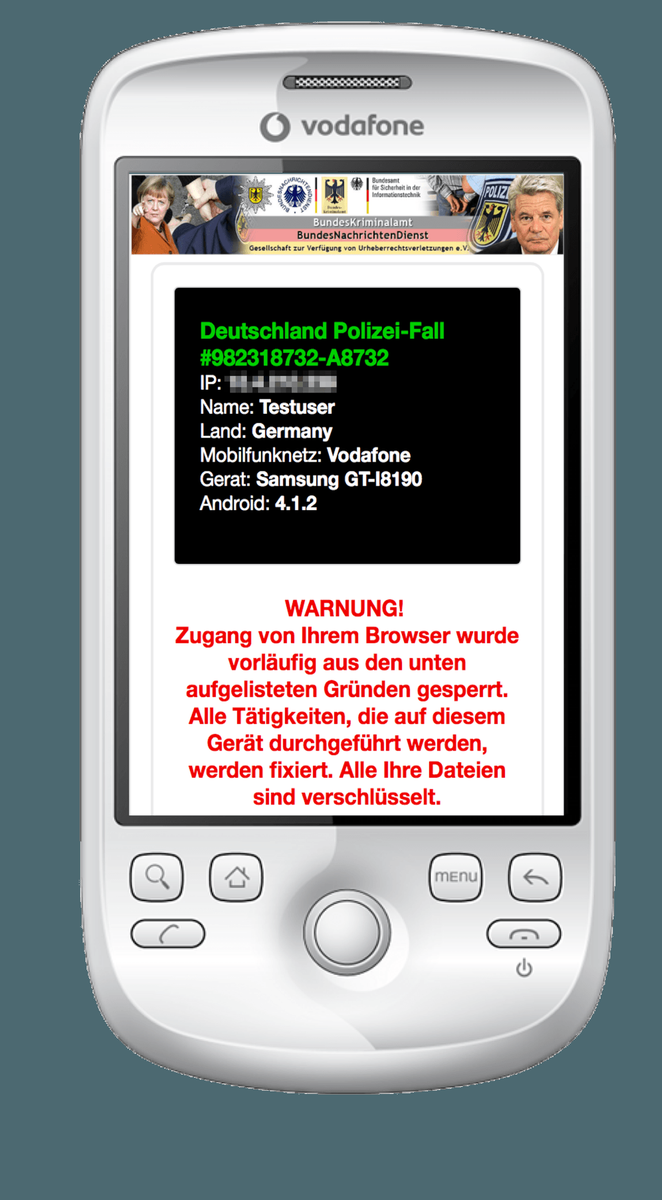
[ Android ] Short overview of Cryptolocker and Ransomware for Android http://forensics.spreitzenbarth.de/2016/06/06/overview-cryptolocker-and-ransomware/ https://t.co/FHNIflvAfN
" Android 平台 Cryptolocker 勒索软件概览: https://t.co/jgf78a1K34 https://t.co/FHNIflvAfN "
-

[ Attack ] 171 million http://VK.com accounts stolen by hackers, and are now for sale http://www.zdnet.com/article/vkontakte-vk-hacked-171-million-accounts-sold-dark-web/
"1.71 亿 VK.com 账户信息被黑客盗取,而且正在被出售。 来自 ZDNet 的报道: https://t.co/bCcylamlUw VK.com 是欧洲最大的社交网络平台"
-

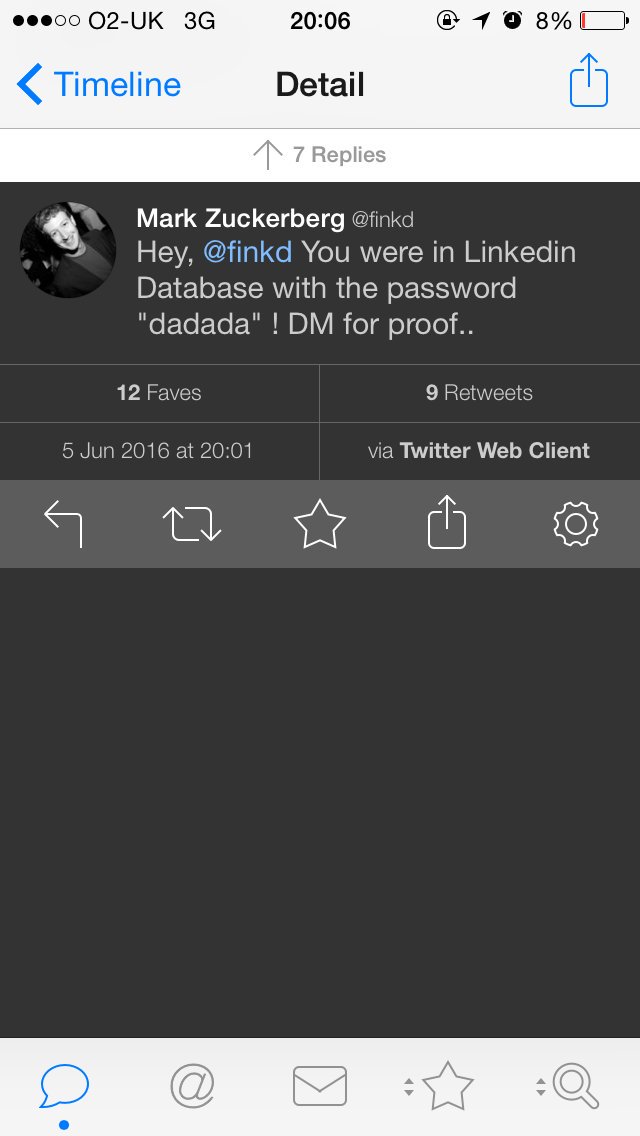
[ Attack ] Ouch. Mark Zuckerberg's social media accounts have been hacked https://t.co/KvVmXOIg5s
" 马克 · 扎克伯格的 Twitter 和 Pinterest 账号被黑,来自 SoftPedia 的报道: http://news.softpedia.com/news/saudi-hackers-take-over-mark-zuckerberg-s-twitter-and-pinterest-accounts-504893.shtml "
-

[ Browser ] WAVM : Standalone WebAssembly VM prototype : https://github.com/AndrewScheidecker/WAVM
"WAVM - 独立版本的 WebAssembly 虚拟机原型︰ https://t.co/4SQX5wEaPC"
-

[ Detect ] As promised, blog post: Threat Actors Employ COM Technology in Shellcode to Evade Detection https://blogs.mcafee.com/mcafee-labs/threat-actors-employ-com-technology-shellcode-evade-detection.
" 攻击者在 Shellcode 中采用 COM 技术逃逸检测: https://t.co/wSpEEPFFxm "
-

[ Fuzzing ] afl-cov 0.6 released: https://github.com/mrash/afl-cov Code coverage for afl-fuzz.
"afl-cov - afl Fuzz 工具的代码覆盖率计算工具︰ https://t.co/Z50kRB58VX "
-

[ Hardware ] Wi-Fi hack can disable Mitsubishi Outlander's anti-theft alarm http://www.theregister.co.uk/2016/06/06/mitsubishi_outlander_hack/
"通过 Wi-Fi 攻击的方法,黑客可以禁用三菱欧蓝德汽车的防盗报警器,来自 TheRegister 的报道: https://t.co/KeSiBDRtzR"
-

[ iOS ] Fingerprint Unlock Security: iOS vs. Google Android http://blog.elcomsoft.com/2016/06/ios-fingerprint-unlock-security/
" iOS 指纹解锁安全性研究: https://t.co/JRAraihr1u"
-

[ IoTDevice ] Connect to Bluetooth devices from the browser, with just 3 lines of JavaScript : https://sabertooth-io.github.io/
" Sabertooth - 三行代码实现通过浏览器与蓝牙设备交互︰ https://t.co/xl3i2fDPcn Sabertooth 是一个用于与蓝牙低功耗设备交互的 JavaScript 库"
-

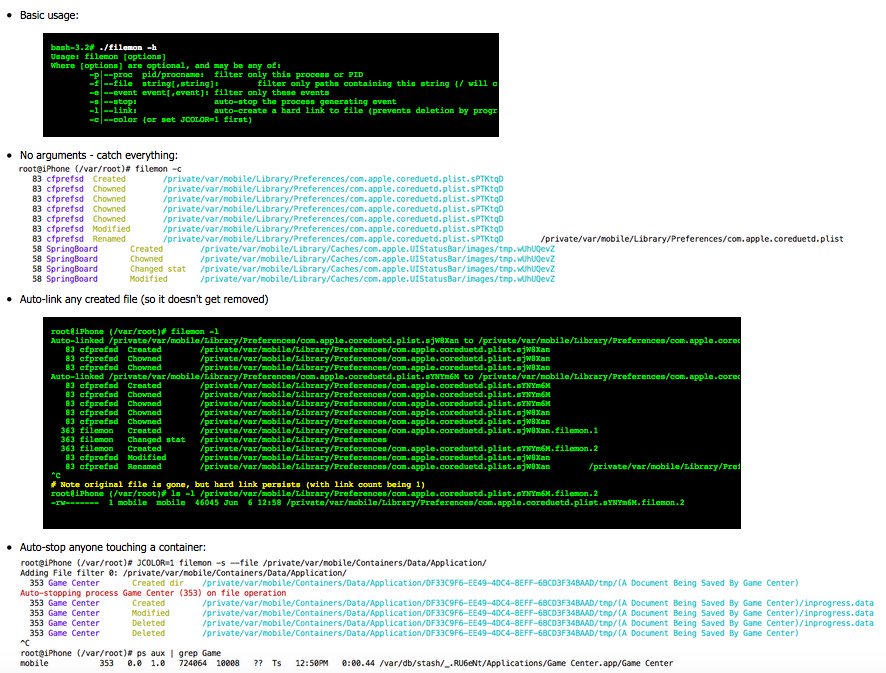
[ Mac OS X ] #OSX/#iOS #filemon utility - updated! Can now auto-stop processes and auto-hardlink files! http://NewOSXBook.com/tools/filemon.html https://t.co/nYDDSqREr1
" filemon - 基于文件系统事件的文件监控工具: https://t.co/6KFu0AtEnV https://t.co/nYDDSqREr1"
-

[ Mac OS X ] As requested - my talk from @ layer_one about #osx_pirrit is up! https://www.youtube.com/watch?v=CHiYT7vU9Fk&feature=youtu.be Slides coming soon
"OS X.Pirrit - 广告软件一直被大家忽视,尤其是 OS X 系统的广告软件,来自 Layerone 会议的一篇演讲就谈这个问题(视频): https://t.co/Ygo50kCwZ9 "
-

[ Malware ] Angler Exploit Kit Evading EMET https://www.fireeye.com/blog/threat-research/2016/06/angler_exploit_kite.html h/t @ StuAllard
" Angler Exploit Kit 组合多种技术成功逃逸 EMET 的检测,来自 FireEye Blog: https://t.co/lkUV30IXkn "
-

[ Malware ] Locky Ransomware Hides Under Multiple Obfuscated Layers of JavaScript https://blogs.mcafee.com/mcafee-labs/locky-ransomware-hides-under-multiple-obfuscated-layers-of-javascript/
" Locky 勒索软件通过多层 JavaScript 混淆隐藏自身,来自 McAfee Blog: https://t.co/h8jeqilp6a"
-

[ Malware ] Hash Factory - Cerber ransomware morphs every 15 seconds http://www.invincea.com/2016/06/hash-factory-new-cerber-ransomware-morphs-every-15-seconds/
"哈希工厂 - 每 15 秒产生一个新变种的勒索软件: https://t.co/bdyZgNXOwB"
-

[ Others ] RSA releases latest article on skimmers and hotel safes. Interesting http://www.rsaconference.com/blogs/the-dangers-of-skimmers-and-safes-in-hotel-rooms
"RSA 发了一篇 Blog 谈射频窃听装置与酒店安全: https://t.co/hpU8nh95fB"
-

[ Pentest ] Embedding reverse shell in .lnk file or Old horse attacks : http://onready.me/old_horse_attacks.html
" 如何在 .lnk 快捷方式文件中嵌入一个反弹 Shell︰ https://t.co/GbnG00yTTi"
-

[ Popular Software ] Analysis of Use-After-Free #Vulnerability (CVE-2016-4119) in #Adobe Acrobat and Reader http://blog.fortinet.com/2016/06/06/analysis-of-use-after-free-vulnerability-cve-2016-4119-in-adobe-acrobat-and-reader #Fortinet
" Adobe Reader/Acrobat UAF 漏洞分析(CVE-2016-4119),来自 Fortinet Blog: https://t.co/6pdBlDIwhF "
-

[ SecurityProduct ] Windows 7 firewall bypass PoC http://www.intelligentexploit.com/view-details.html?id=23956
"Windows 7 防火墙绕过 PoC,绕过的方法是搜索防火墙 UI 窗口和按钮,模拟发送按键,禁用保护: https://t.co/usK8S0fzWE"
-

[ Web Security ] Double Opt-In for Download 2.0.9 Sql Injection http://security.szurek.pl/double-opt-in-for-download-209-sql-injection.html #WordPress #Exploit
" WordPress 'Double Opt-In for Download' 插件 2.0.9 版本 SQL 注入漏洞: https://t.co/vXW2d01P20 "
-

[ Web Security ] Starting to publish my WordPress XSS plugin research results https://gitlab.com/lcashdol/wpxssdb
"上周推送过一篇《如何在一小时内发现 1352 个 WordPress 插件 XSS 0Day》,昨天作者公开了存储相关研究成果的数据库: https://t.co/CTESdrLGMU"
-

[ Windows ] Windows Api Hooking with x86 Assembly : http://www.bmicrosystems.com/blog/windows-api-hooking-with-x86-assembly/ cc @ BatuhanBurakcin
"Windows API Hook 的 x86 汇编实现 ︰ https://t.co/bp2Jv47AK3 "
-

[ Windows ] Windows IOCTL Reference - http://www.ioctls.net/
"从 DDK 中提取的 Windows IOCTL 表(包括 IOCTL Code、所在头文件、摘要介绍),共 760 条: https://t.co/XJJSQv8fkD"