腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] CVE-2015-3854 Battery permission leakage in Android http://goo.gl/fb/eC2w6Q #FullDisclosure
" Android 电池、电量相关权限泄漏漏洞(CVE-2015-3854),发现者为 KeenLab Flanker,来自 FullDisclosure 的公告: https://t.co/N0gLScYtTy "
-

[ Android ] jniostorlab - Script to enumerate JNI methods in ELF files. https://github.com/ostorlab/jniostorlab
"jniostorlab - 用于枚举 ELF 文件中 JNI 方法的脚本, GitHub Repo: https://t.co/SohVJcmvSl"
-

[ Android ] Droid-ff: Android Fuzzing Framework: https://conference.hitb.org/hitbsecconf2016ams/materials/D1T3%20LABS%20-%20Anto%20Joseph%20-%20Droid-FF.pdf presentation by @ antojosep007 at @ HITBSecConf
" Droid-ff - Android Fuzz 框架,来自昨天 HITB 阿姆斯特丹会议的演讲: https://t.co/XNwQelf0TD 其他的几个已公告的议题 Slides: https://conference.hitb.org/hitbsecconf2016ams/materials/ "
-

[ Attack ] Dozens of VISA HTTPS-protected sites vulnerable to Forbidden attack http://securityaffairs.co/wordpress/47724/breaking-news/forbidden-attack.html
" 隶属 VISA 的大量 HTTPS 保护的网站易受 'Forbidden Attack' 攻击,70000 服务器受影响,来自 SecurityAffaris 的报道: https://t.co/LjkFJNuKON"
-

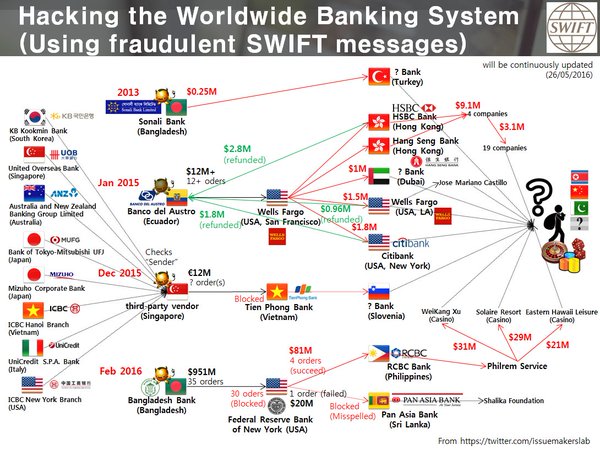
[ Attack ] Overview of the SWIFT Related Hacks https://t.co/cAr90GjUXz
" 一张图展示 SWIFT 相关的黑客攻击事件: https://t.co/cAr90GjUXz "
-

[ Attack ] [Intel Security] Android Banking Trojan ‘SpyLocker’ Targets More Banks in Europe https://goo.gl/5QSs9v
" Android 银行木马 'SpyLocker' 将攻击目标设为欧洲的很多银行,来自 McAfee Blog: https://t.co/5XfLMTX9vs"
-

[ Browser ] @ berendjanwever Version 2 is out, with slicker UI and port enumeration. Live: http://blog.skylined.nl/LocalNetworkScanner/ Source: https://github.com/SkyLined/LocalNetworkScanner/
" SkyLined 写的一个本地网络扫描工具,不一样的是,这是一个用 JavaScript 写的网页版工具︰ https://t.co/2PmTMwMiGN GitHub Repo︰ https://t.co/cs3C9RGcEb"
-

[ Crypto ] Slides from my lightning talk about Certificate Transparency and it's advantages at @ DefconRussia https://kyprizel.net/work/defcon-russia-ct.pdf
" 证书透明以及它的优点: https://t.co/rBvXK6eriM"
-

[ Crypto ] slides of my @ AusCERT talk "The burden of faulty and outdated TLS implementations" https://www.int21.de/slides/auscert-tls/
" 存在缺陷的过时 TLS 实现的负担: https://t.co/h9OyPFXtCy"
-

[ Debug ] Here's the basic recipe for debugging xnu with LLDB via the VMware debug server. @ osxreverser https://gist.github.com/rgov/e6107e85563875d9d70b4fab83ccc791
" 用 LLDB 调试器通过 VMware 的 Debug Server,调试 XNU: https://t.co/d6CQWiJpE7"
-

[ Defend ] Kevin Snow just presented at @ IEEESSP how to undermine destructive code reads via code inference attacks https://www3.cs.stonybrook.edu/~mikepo/papers/heisenbite.sp16.pdf
" 通过细粒度的地址随机化对抗代码重用攻击, Paper 《how to undermine destructive code reads via code inference attacks》: https://t.co/7lwke7hdab"
-

[ Hardware ] Warwalking WiFi networks with $4 ESP8266 IoT Module https://phasenoise.livejournal.com/2870.html
" Warwalking WiFi networks with ESP8266 IoT Module: https://t.co/eW5JBasl41 "
-

[ Linux ] Understanding bootloading by bx http://www.cs.dartmouth.edu/~bx/blog/2015/09/03/a-toure-of-bootloading.html [DC20 ELF brainf*kc #weirdmachine https://www.defcon.org/images/defcon-20/dc-20-presentations/Shapiro-Bratus/DEFCON-20-Shapiro-Bratus-Constructing-ELF-Metadata.pdf ] http://t.co/6dzeTb52zx
" 了解 Bootloading 的过程: http://t.co/c0mQ8VLKKs Defcon 20 会议的一篇演讲《构造 ELF 元数据》: https://t.co/YJXopsUq5v http://t.co/6dzeTb52zx"
-

[ Mac OS X ] ZDI-16-358: (Pwn2Own) Apple OS X WindowServer Use-After-Free Privilege Escalation Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-358/
"ZDI-16-358: Apple OS X WindowServer UAF 提权漏洞(CVE-2016-1804,KeenLab 用此漏洞参加的 Pwn2Own 比赛): https://t.co/2LOaIiOgCh"
-

[ Malware ] malSploitBase Malware Exploit Database by @ MisterCh0c https://github.com/misterch0c/malSploitBase https://t.co/Dn8854chM7
" Malware Exploit Database: https://t.co/ieXqcX3DJ6 https://t.co/Dn8854chM7 "
-

[ MalwareAnalysis ] Classifying Malware using Import API and Fuzzy Hashing – impfuzzy – http://blog.jpcert.or.jp/2016/05/classifying-mal-a988.html
" 基于导入表 API 和模糊哈希值分类恶意软件: https://t.co/LSh7RICupl"
-

[ Network ] Next-gen Tor is arriving and it will include a distributed random number generator http://securityaffairs.co/wordpress/47683/deep-web/distributed-tor-random-number-generator.html
" 下一代 Tor 将会采用分布式的随机数生成器,来自 SecurityAffairs 的报道: https://t.co/dyomBxbI0t"
-

[ Others ] Slides of @ JacobTorrey talk 'Using the Observer Effect & Cyber Feng Shui' #HITB2016AMS http://conference.hitb.org/hitbsecconf2016ams/materials/D1T1%20-%20Jacob%20Torrey%20-%20Using%20the%20Observer%20Effect%20and%20Cyber%20Fengshui.pdf
" 利用海森堡效应探测分析工具的存在,来自 HITB 阿姆斯特丹会议: https://t.co/rDHFAwCHHG"
-

[ Others ] AusCERT 2016 slides - introducing phwned http://www.slideshare.net/davidjorm/auscert-2016-cve-and-alternatives
"AusCERT 2016 演讲《CVE 分配过程中存在的问题以及它的替代品》: https://t.co/zLBSn6L5uv"
-

[ Popular Software ] CVE-2016-4803 dotCMS - Email Header Injection http://goo.gl/fb/KKe3s5 #FullDisclosure
" dotCMS 邮件头注入漏洞(CVE-2016-4803),来自 FullDisclosure 的公告: https://t.co/LnZnyDZnr8 "
-

[ SecurityProduct ] Let the AMSI bypasses continue! http://cn33liz.blogspot.nl/2016/05/bypassing-amsi-using-powershell-5-dll.html by @ Cneelis
" 利用 PowerShell 5 的 DLL 劫持漏洞绕过 Windows 10 的反病毒扫描: https://t.co/zwTixYuzhv"
-

[ Tools ] Docker IDA - open-source tool used to make reverse engineering on a large-scale simpler and faster http://blog.intezer.com/docker-ida/
"Docker IDA - Docker 与 IDA 的结合,可以使逆向规模化、简单化的工具: https://t.co/Tyg4uY8P77"
-

[ Windows ] Creating a custom out-of-process event listener host application https://msdn.microsoft.com/en-us/library/dn774991(v=pandp.20).aspx
" 自己写一个进程外的事件侦听器程序,来自 MSDN: https://t.co/AxpLR5Axzi"
-

[ Windows ] Fibratus - Tool for exploration and tracing of the Windows kernel https://github.com/rabbitstack/fibratus
" Fibratus - Windows 内核 Trace 工具,可以跟踪进程/线程的创建、文件系统操作、网络活动、注册表操作、DLL 加载等等行为: https://t.co/QFkxS6yeQh "