腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Following Devil’s Footprints: Cross-Platform Analysis of Potentially Harmful Libraries on Android and iOS: http://www.ieee-security.org/TC/SP2016/papers/0824a357.pdf
"跟随魔鬼的脚步︰ Android、iOS 潜在危险的跨平台库分析: https://t.co/lmRVJkAW7q 来自 IEEE 安全与隐私研讨会,全部的议题: http://www.ieee-security.org/TC/SP2016/program-papers.html "
-

[ Attack ] Widespread Vulnerable Ads (Part Two) : Flash Edition (Facebook’s LiveRail, Akamai, Adobe products affected) : https://randywestergren.com/widespread-vulnerable-ads-part-two-flash-edition-facebooks-liverail-akamai-adobe-products-affected/
"广泛传播的存在漏洞的广告(Part 2)︰ Flash 版: https://t.co/voMk9cddre"
-

[ Attack ] Tech Support Scammers using Winlogon https://blog.malwarebytes.org/cybercrime/2016/05/tech-support-scammers-using-winlogon/
"技术支持骗子通过修改 Winlogon 注册表项诈骗用户: https://t.co/GUSN7xyIy0"
-

[ Attack ] FireEye detects unique #cyber attacks targeting banks in Middle East: http://bddy.me/27Qhemh #infosec
"FireEye 捕获到一个针对中东地区银行的定向攻击︰ https://t.co/4WjbQY7NSK "
-

[ Attack ] Excellent report from MELANI / GovCERT.ch about the APT attack against RUAG: https://www.govcert.admin.ch/blog/22/technical-report-about-the-ruag-espionage-case #turla
" 瑞士拉格公司(RUAG) APT 攻击分析报告,来自瑞士 CERT 披露: https://t.co/afSmeqC02H "
-

[ Conference ] All #PHDays video is now online http://www.phdays.com/broadcast/
" 上周 PHDays 会议的所有视频: https://t.co/6TTHtKwuZ5"
-

[ Defend ] Designing secure digital services: It is essential that public sector can build systems that are robust to attack https://www.cesg.gov.uk/news/designing-secure-digital-services
" 如何设计一个安全的数字服务系统,来自 CESG(英国通信电子安全小组,隶属 GCHQ): https://t.co/EgKYSc9m4D "
-

[ Detect ] CapTipper is a Python tool to explore malicious HTTP traffic, also review sessions from PCAP ~ http://www.darknet.org.uk/2016/05/captipper-explore-malicious-http-traffic/
"CapTipper - HTTP 异常流量检测工具, Python 语言编写,也支持从 PCAP 文件中检测: https://t.co/MLguJN2JZS"
-

[ Detect ] Ransomware Steals your Phone. Formal Methods Rescue it. https://www.researchgate.net/profile/Antonella_Santone/publication/301564057_Ransomware_Steals_your_Phone_Formal_Methods_Rescue_it/links/571f0ddc08aefa648899ab23.pdf [Paper - 6/2016]
" 这篇 Paper 提出了一种新的检测手机勒索软件的方法: https://t.co/Td27mHHJff "
-

[ IoTDevice ] Abusing Easy Smart TP-Link switches. How to sniff and crack admin creds: https://www.pentestpartners.com/blog/how-i-can-gain-control-of-your-tp-link-home-switch/ https://t.co/NqjojKcpCL
" 我是如何获得 Easy Smart TP-Link 交换机的管理员权限的︰ https://t.co/v74sBLUVwQ https://t.co/NqjojKcpCL"
-

[ Mac OS X ] Staying Secure and Unprepared: Understanding and Mitigating the Security Risks of Apple ZeroConf: http://www.ieee-security.org/TC/SP2016/papers/0824a655.pdf
" 了解并防护 Apple 零配置组件(Bonjour)的安全风险︰ https://t.co/sfU4KIdV8I"
-

[ Malware ] Dridex Updates Payload Distribution : http://www.malwaretech.com/2016/05/dridex-updates-payload-distribution.html cc @ MalwareTechBlog
"Dridex 更新了 Payload 的分发策略︰ https://t.co/YL3CytDj9X "
-

[ Malware ] #Unit42 discovers Operation #Ke3chang has resurfaced with new #TidePool #malware http://bit.ly/22l2g3S
" Ke3chang 攻击行动的最新进展 - 带着新工具 TidePool 卷土重来,来自 Palo Alto Blog: https://t.co/Pg2BwbcNiV"
-

[ Malware ] DMA Locker 4.0 – Known Ransomware Preparing For A Massive Distribution https://blog.malwarebytes.org/threat-analysis/2016/05/dma-locker-4-0-known-ransomware-preparing-for-a-massive-distribution/
"DMA Locker 4.0 勒索软件分析,来自 MalwareBytes Blog: https://t.co/RfV8N3rCPE"
-

[ Obfuscation ] Effectiveness of Synthesis in Concolic Deobfuscation https://hal.inria.fr/hal-01241356/document
" Effectiveness of Synthesis in Concolic Deobfuscation, Paper: https://t.co/2VKA6LMtP3 "
-

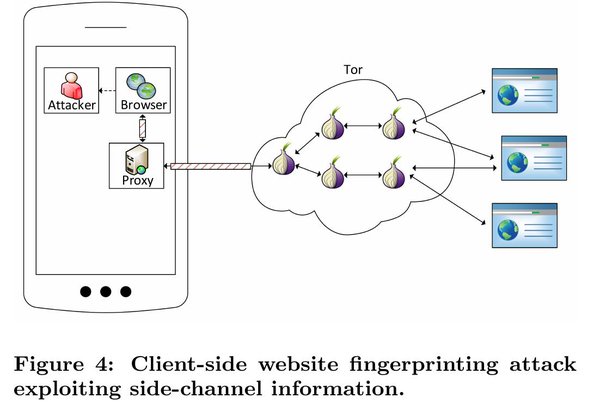
[ Others ] Our side-channel attack on inferring visited websites on #Android (in #Tor browser) accepted @spw2016 w/@SGriesmayr https://t.co/dpGV5qn8iy
"利用边信道攻击的方法探测 Android(Tor) 浏览器已访问过的站点"
-

[ Others ] The Megaprocessor - Architecture : http://www.megaprocessor.com/architecture.html ,Instruction Set : http://www.megaprocessor.com/instruction_set.pdf (pdf)
" Megaprocessor 架构 : https://t.co/wPzI9GqF0W 指令集手册 : https://t.co/1MjS4I6pGV "
-

[ Others ] Spawning a Shell by LFI Poisoning Log Files http://infoseczone.net/spawning-a-shell-by-lfi-poisoning-log-files/
" 通过污染日志文件的方法上传 Shell: https://t.co/KtbBSikqY7"
-

[ Popular Software ] Adobe patches Connect: https://helpx.adobe.com/security/products/connect/apsb16-17.html
"Adobe 发布补丁更新,修复了 Adobe Connect 产品的一个路径搜索相关的漏洞(CVE-2016-4118)︰ https://t.co/bnbkaxRW34"
-

[ Popular Software ] Exploring Java deserialization in GitHub http://philwantsfish.github.io/security/java-deserialization-github
" 从 GitHub 上的项目看 Java 反序列化漏洞的影响范围: https://t.co/7VHPrBRQZg "
-

[ ReverseEngineering ] Practical Reverse Engineering (Part 3) - Following the Data : http://jcjc-dev.com/2016/05/23/reversing-huawei-3-sniffing/ ,Part 2 : http://jcjc-dev.com/2016/04/29/reversing-huawei-router-2-scouting-firmware/
" 前段时间推送过两篇文章:《逆向华为路由器,寻找 HG533 路由器的调试端口》和《固件数据收集》,昨天作者又写了第三篇 : https://t.co/TqaVRfEW7b "
-

[ Tools ] Free decryptor for TeslaCrypt #ransomware https://kas.pr/Zth7 https://t.co/kfKmOxC5F1
" Kaspersky 公开了一款 TeslaCrypt 勒索软件解密工具: https://t.co/Y8PRx98fuG https://t.co/kfKmOxC5F1 "
-

[ Tools ] #malware #shellcode detector https://www.malwaretracker.com/shellcode.php
"Shellcode 在线检测工具: https://t.co/5IYUrY8dDd"
-

[ Tools ] Slides for my presentation on predictive modeling ecosystem at @ pydataberlin: http://ogrisel.github.io/decks/2016_pydata_berlin/ / notebook: https://github.com/ogrisel/docker-distributed
" 基于 Python 的预测模型建模方法和工具: https://t.co/sclUvg3U7w 笔记︰ https://t.co/OAmjUvA8XO"
-

[ Web Security ] Slides from my #XSS Talk @ BsidesBoston http://brutelogic.com.br/docs/advanced-xss.pdf @ plaverty9 @ _larry0 @ danielcid @ perezbox https://t.co/8v8QtNdLMF
" 高级 XSS 向量,来自 BsidesBoston 会议: https://t.co/44zzEzP2wc https://t.co/8v8QtNdLMF "
-

[ Web Security ] My slides from @ BsidesBoston https://gitlab.com/lcashdol/slides/blob/master/wordpress-1352.pdf cc @ forced_request
" 如何在一小时内发现 WordPress 插件的 1352 个 XSS 0Day,来自 BisdesBoston 会议: https://t.co/11LAOMZncV "
-

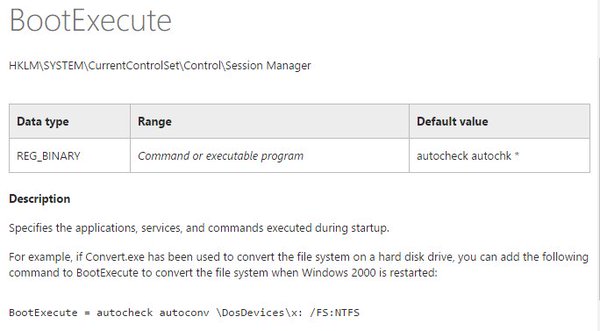
[ Windows ] #DFIR analysts: get familiar w/native BootExecute apps like #Furtim https://technet.microsoft.com/en-us/sysinternals/bb897447.aspx https://kobyk.wordpress.com/2008/07/26/debugging-user-mode-bootexecute-native-applications-with-kd/ https://t.co/IOFo0N7PDC
" 调试用户态 Native BootExecute 应用程序: https://t.co/KJLnhGgTR6 https://t.co/RxaIgG5omm "
-

[ Windows ] Pico Process Overview - https://blogs.msdn.microsoft.com/wsl/2016/05/23/pico-process-overview/ project drawbridge and wsl
" Pico Process Overview,来自微软 Blog: https://t.co/YhPuF0Aezv "