腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

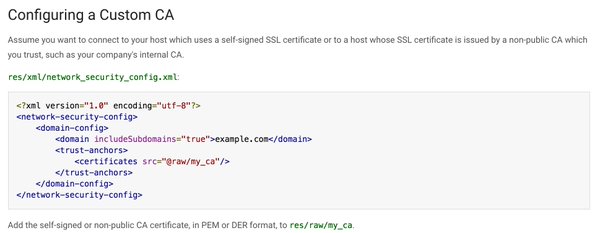
[ Android ] Android N's cert pinning API is easy-to-implement & flexible. Works with custom certs. https://developer.android.com/preview/features/security-config.html https://t.co/dDrjG8Sxxd
" Android N 网络安全配置指南,来自 Android 开发者网站: https://t.co/BENiOp90Sr https://t.co/dDrjG8Sxxd"
-

[ Android ] Android Qualcomm Vulnerability Impacts 60 Percent of Devices: https://threatpost.com/android-qualcomm-vulnerability-impacts-60-percent-of-devices/118191/ via @ threatpost
" 'Bits, Please' Blog 那篇《从 QSEE 劫持 Linux 内核》提到的高通漏洞影响 60% 的 Android 设备,来自 ThreatPost 的报道: https://t.co/jzVkx2JvD9 从 QSEE 劫持 Linux 内核: http://bits-please.blogspot.com/2016/05/war-of-worlds-hijacking-linux-kernel.html Duo Security 的分析: https://duo.com/blog/sixty-percent-of-enterprise-android-phones-affected-by-critical-qsee-vulnerability "
-

[ Browser ] Audio, Battery, WebRTC APIs in HTML5 are all being abused by third-party scripts for fingerprinting : https://webtransparency.cs.princeton.edu/webcensus/index.html#fp-results
"HTML5 中的 Audio、Battery、WebRTC API 都可以被滥用实现指纹跟踪︰ https://t.co/ovqd7hL0Ut lcamtuf 也研究过这个问题: https://www.chromium.org/Home/chromium-security/client-identification-mechanisms "
-

[ Browser ] ZDI-16-338: Microsoft Edge JavaScript shift Method Uninitialized Memory Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-338/
"ZDI-16-338︰ 微软 Edge 浏览器 JavaScript shift 方法未初始化内存 RCE,来自 ZDI 的公告: https://t.co/cRQrQ6e1Cq"
-

[ Browser ] ZDI-16-342: (Pwn2Own) Apple Safari TextTrack Object Use-After-Free Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-342/
"ZDI-16-342: Apple Safari TextTrack 对象 UAF RCE(lokihardt 参加 Pwn2Own 比赛用的漏洞): https://t.co/5sR87zad14"
-

[ Crypto ] Gmail Disabling RC4 and SSLv3 SMTP Support https://cryptosense.com/gmail-disabling-rc4-and-sslv3-smtp-support/
"Gmail TLS 服务器不再支持 RC4 和 SSLv3: https://t.co/Lj4aKyVpKJ"
-

[ Crypto ] Nonce-Disrespecting Adversaries: Practical Forgery Attacks on GCM in TLS https://github.com/nonce-disrespect/nonce-disrespect
" TLS AES-GCM 随机数重用攻击: https://t.co/xo2QowXUF3"
-

[ Debug ] Detecting KMDs with a single instruction http://www.anti-reversing.com/detecting-kmds-with-a-single-instruction/
" 一条指令检测内核模式调试器: https://t.co/7qCTavGKrG "
-

[ Detect ] Hunting rootkits with Windbg v1.1 : http://www.reconstructer.org/papers/Hunting%20rootkits%20with%20Windbg.pdf (pdf) #b2b
"用 Windbg 找 Rootkit: https://t.co/9RO1cy2DAP "
-

[ Mac OS X ] ZDI-16-345: (Pwn2Own) Apple OS X IntelAccelerator Out-Of-Bounds Indexing Privilege Escalation Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-345/
"ZDI-16-345: Apple OS X IntelAccelerator 索引越界提权漏洞(KeenLab 参加 Pwn2Own 比赛中的漏洞) https://t.co/RQOi66xr0a"
-

[ Mac OS X ] ZDI-16-347: Apple OS X IOAudioFamily Buffer Overflow Privilege Escalation Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-347/
"ZDI-16-347︰ Apple OS X IOAudioFamily 缓冲区溢出提权漏洞, ZDI 公告: https://t.co/CZTBEEYq8i"
-

[ Malware ] document.getMalwareByLanguage ('JavaScript') http://www.crestandiisp.com/wp-content/uploads/2016/03/ThomasLancasterandChrisDoman.pdf
"document.getMalwareByLanguage('JavaScript'), JavaScript 编写的恶意软件,来自 CrestCon 会议: https://t.co/Ug2JbcnawI"
-

[ Network ] Our (Silke Holtmanns, me & @ i_j_oliver ) on location tracking in LTE is available now at http://tinyurl.com/iwfslides) & http://tinyurl.com/iwfpaper.
" 利用互通功能在 LTE 网络内实现用户地理位置跟踪, Slides: https://t.co/rANysuFnqy Paper: https://t.co/XCmspkmXvC "
-

[ Network ] Anothr cool thesis, by @ anantary: Security Implications of the MLD Protocol in IPv6 Networks https://www.its.fh-muenster.de/doc/Security_Implications_of_MLD_in_IPv6_Networks.pdf (supervisor @ seecurity)
" IPv6 网络中 MLD 协议对安全的影响, Paper: https://t.co/zSFjMAh6pj "
-

[ Obfuscation ] X86 Shellcode Obfuscation (Part 2) : https://breakdev.org/x86-shellcode-obfuscation-part-2/ , Part 1 : https://breakdev.org/x86-shellcode-obfuscation-part-1/
"X86 Shellcode 混淆 Part 2: https://t.co/SLVDc1HGj1 Part 1: https://t.co/PUQOjsaBuQ"
-

[ Others ] @ spacerog @ wr0 @ WeldPond The slides are available at https://mchow01.github.io/docs/source2016.pdf
" 网络安全教育的疏漏: https://t.co/gd09UWjxTj"
-

[ Others ] Japanese Docomo makes its smartphone covertly trackable http://securityaffairs.co/wordpress/47476/mobile-2/docomo-trackable-devices.html
"日本手机渠道商 NTT Docomo 表示他们的手机可被政.府用于追踪用户位置: https://t.co/LPJRo0gUYG"
-

[ Others ] automatically classifying integer overflows as harmful or benign http://dl.acm.org/citation.cfm?id=2884820
" 自动化区分可利用和不可利用的整数溢出漏洞: https://t.co/K98nyIJnMH"
-

[ Others ] Vote! Finalists of European Security Blogger Awards 2016 https://www.surveymonkey.com/r/secbloggerwards2016
" 2016 欧洲安全类博客大奖入围名单: https://t.co/u1nRTgJenh "
-

[ Pentest ] Client-side WarGames - my talk at @ HackInBo 2016 in Bologna. Slides online: http://www.hackinbo.it/wp-content/uploads/2016/05/HackInBO_2016_Orru.pdf Video soon on https://www.youtube.com/channel/UCu6uzKY7A5jQCx9yHUL_vfQ
" Client-side WarGames,来自 HackInBo 2016 会议一篇谈渗透、钓鱼的议题 ︰ https://t.co/KeJrtOyVqF 视频: https://t.co/sG8gpkYAoT"
-

[ Virtualization ] #Docker for Mac and Windows introduces new #opensource components: #HyperKit, #DataKit and #VPNKit https://blog.docker.com/2016/05/docker-unikernels-open-source/ via @ docker
" Docker for Mac and Windows 引入了新的开源组件︰ HyperKit、DataKit、VPNKit: https://t.co/dSziaVh7Iq"
-

[ Windows ] Nice paper on correlating the UsnJrnl, LogFile, and MFT: http://rp.delaat.net/2015-2016/p18/report.pdf
" NTFS 文件系统的历史日志(UsnJrnl)解析, Paper: https://t.co/pJgIrrJ1XY"
-

[ Windows ] [Blog Post] To Disarm Device Guard - Bring a Debugger to the Fight. Proof Of Concept http://subt0x10.blogspot.com/2016/05/to-disarm-device-guard-bring-debugger.html Feedback Welcome. Cheers
" 利用调试器使 Device Guard 缴械投降,来自 subTee 的 Blog: https://t.co/YrVsYq3uU7 "
-

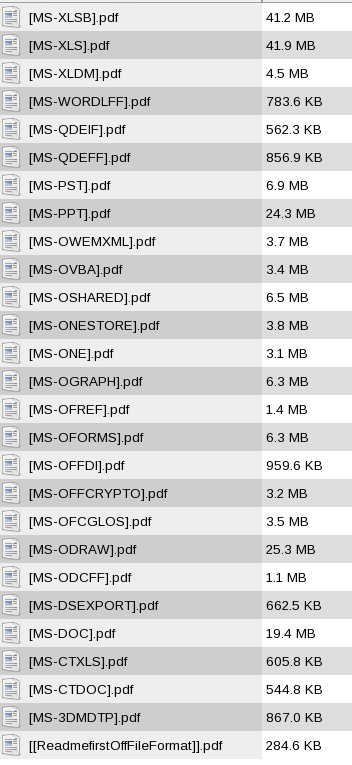
[ Windows ] [PDF] Zip [~83 Mb] with specifications of Microsoft Office File Formats Protocols. http://download.microsoft.com/download/2/4/8/24862317-78F0-4C4B-B355-C7B2C1D997DB/OfficeFileFormatsProtocols.zip https://t.co/2iX6l250k5
"Microsoft Office 文件格式规范下载(ZIP 格式,约 83MB): https://t.co/bvuZB0eqPF https://t.co/2iX6l250k5"