腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] DexExtractor - Android dex file extractor, anti-bangbang (Bangcle) - https://github.com/bunnyblue/DexExtractor
"DexExtractor - Android dex 文件提取工具,可以对抗梆梆: https://t.co/Q0nwbQtxtx"
-

[ Android ] Some more CF-Auto-Root's for Samsung 6.0 firmwares have been uploaded, including several Note4 variants. https://autoroot.chainfire.eu/
" CF-Auto-Root - 跟踪最新的 Android Root 信息: https://t.co/asmdVrLyTc"
-

[ Android ] POC for remote Linux / Android kernel stack buffer overflow via WiFi https://github.com/abdsec/CVE-2016-0801/blob/master/PoC.c
" Android/Linux 内核 WiFi 模块栈缓冲区溢出漏洞 PoC(CVE-2016-0801): https://t.co/sZW71rupja"
-

[ Backdoor ] Back door found in Allwinner Linux kernels : http://www.theregister.co.uk/2016/05/09/allwinners_allloser_custom_kernel_has_a_nasty_root_backdoor/ , Patch : https://github.com/friendlyarm/h3_lichee/commit/5d4d02b1c8f336ba002eed4d97dee3a51ea76cdd
"全志科技(Allwinner)Linux 定制内核被发现了 Root 后门 : https://t.co/vv0Z2AB8D7 Patch : https://t.co/5V3c9Wa32n"
-

[ Browser ] ZDI-16-283: (Pwn2Own) Microsoft Edge JavaScript fill Out-Of-Bounds Access Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-283/
"ZDI-16-283: Edge 浏览器 JavaScript fill 越界访问 RCE, 腾讯 KeenLab 今年用此漏洞参加了 Pwn2Own 比赛: https://t.co/bzD7AFpHUz"
-

[ Browser ] Advisory - ZDI-16-282: (Pwn2Own) Microsoft Edge JavaScript concat Method Uninitialized Memory Remote Code Executio… http://ift.tt/1TDbamz
"ZDI-16-282 公告: 微软 Edge 浏览器 JavaScript 引擎 concat 方法内存未初始化 RCE,今年的 Pwn2Own,lokihardt 就是用此漏洞攻击的 Edge: https://t.co/98dqBpepYM"
-

[ Challenges ] Facebook Open-Source Capture The Flag (CTF) Platform https://github.com/facebook/fbctf #infosec
"Facebook 开源了一个山丘之王风格的 CTF 平台: https://t.co/hcqvty1e8x "
-

[ Detect ] Proactive threat detection on Windows machines https://github.com/devonakerr/Presentations/blob/master/Proactive%20Threat%20Detection%20-%20Windows.pdf
" Windows 主动威胁检测技术,作者来自 FireEye,这是他在 NorCERT 和 BSides Nola 会议的演讲: https://t.co/4bZa4cpfaD"
-

[ Forensics ] Powershell #DFIR must-reads: 1. https://p0w3rsh3ll.files.wordpress.com/2014/08/fireeye-lazanciyan-investigating-powershell-attacks.pdf 2. https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html 3. https://blogs.msdn.microsoft.com/powershell/2015/06/09/powershell-the-blue-team/ 4. http://www.asd.gov.au/publications/protect/Securing_PowerShell.pdf
"关于 Powershell 取证技术与应急事件响应的几篇必读文章︰ 1: https://t.co/DKUgh9FPXh 2: https://t.co/X7KaXOJaAy 3: https://t.co/YgvKECO5Ji 4: https://t.co/1zuf2Ruib7"
-

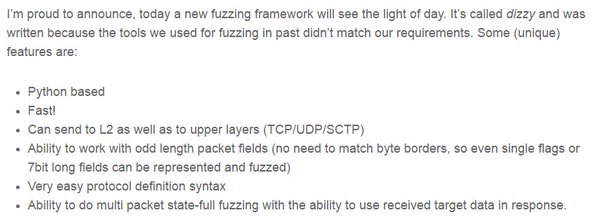
[ Fuzzing ] Also: dizzy fuzzing library https://github.com/ernw/dizzy https://www.insinuator.net/2011/07/week-of-releases-dizzy/ https://github.com/ernw/insinuator-snippets/tree/master/VoLTE-dizzy https://t.co/iAMWCLVJLv
" Dizzy - 网络数据包 Fuzz 框架, Python 语言编写: https://t.co/JNjOrnzn98 https://t.co/LN7ockj3Nq https://t.co/sBWXInpMYz https://t.co/iAMWCLVJLv"
-

[ Hardware ] 10 Part Tutorial on Designing/Building a PCB (Using FOSS) : https://contextualelectronics.com/gtb-kicad-4-0/
" PCB 板设计与制作指南 ︰ https://t.co/NksaEQp3if"
-

[ Industry News ] IBM’s Watson Supercomputer Takes On Security, being used to profile and thwart viruses and ransomware ! https://threatpost.com/ibms-watson-supercomputer-takes-on-security/117999/
"IBM 的沃森超级计算机准备为安全做点贡献,将被用来对抗病毒、勒索软件和 DDoS 攻击: https://t.co/9ItF08r7EJ"
-

[ Malware ] Large Kovter digitally-signed malvertising campaign and MSRT cleanup release https://blogs.technet.microsoft.com/mmpc/2016/05/10/large-kovter-digitally-signed-malvertising-campaign-and-msrt-cleanup-release/
" 微软 MMPC 团队对 Kovter 家族恶意广告攻击的分析: https://t.co/4AiT1fXqOC"
-

[ Malware ] AlphaLocker Is the Most Professional Ransomware Kit to Date http://ow.ly/Q5Fj3001bDW
"AlphaLocker 是目前为止最专业的勒索软件,来自 SoftPedia 的报道: https://t.co/EFuI44duYJ"
-

[ Malware ] Gootkit/Xswkit Javascript Malware Source Files https://github.com/jgegeny/gootkit-xswkit-js #RE #malware #infosec
"Gootkit/Xswkit 木马的 JavaScript 源码: https://t.co/AH7ye3tdXt S21sec 对 Gootkit 的逆向分析: http://securityblog.s21sec.com/2016/05/reverse-engineering-gootkit.html "
-

[ MalwareAnalysis ] Adaptive Internet Simulation, fighting fingerprinting, new blog post out: http://joe4security.blogspot.ch/2016/05/adaptive-internet-simulation.html #DFIR https://t.co/oUOmRW46zl
" 在恶意软件自动化分析中,样本通常需要联网。但是联网也是有风险的,因为这相当于暴露了我们的指纹信息。这篇 Blog Joe Security 团队提出了 '自适应网络模拟技术' 解决这个问题: https://t.co/sKkXYncQD3 https://t.co/oUOmRW46zl"
-

[ OpenSourceProject ] Talos Blog: Multiple 7-Zip Vulnerabilities Discovered by Talos http://bit.ly/1ZFySmR
"Talos 团队发现了 7-Zip 工具的多个漏洞: https://t.co/BOH7PWPRGz"
-

[ Others ] Clearing up some misconceptions around the "ImageTragick" bug http://lcamtuf.blogspot.com/2016/05/clearing-up-some-misconceptions-around.html
" Lcamtuf 澄清关于 "ImageTragick" Bug 的一些误解: https://t.co/H0dAU0HNA5 "
-

[ Pentest ] 5 Years of Real Penetration Test Data https://foxglovesecurity.com/2016/05/10/why-dos-isnt-compromise-5-years-of-real-penetration-test-data-to-stand-behind/ (via @ jstnkndy)
"看完 Verizon 的数据泄漏报告后,作者依据自己 5 年的真实渗透测试数据来谈谈看法: https://t.co/OJJeofDI80"
-

[ Popular Software ] If you're using any of @ JetBrains #IntelliJ based IDEs please read this http://blog.jetbrains.com/blog/2016/05/11/security-update-for-intellij-based-ides-v2016-1-and-older-versions/ and update as soon as possible #itsecurity
" IntelliJ IDE v2016.1 版本更新安全公告: https://t.co/fGngHTTAWQ "
-

[ Popular Software ] Running SAP Java apps? Check whether the Invoker Servlet is enabled. https://threatpost.com/attackers-targeting-critical-sap-flaw-since-2013/118013/ via @ threatpost
" SAP 商业应用软件的 Invoker Servlet 存在严重漏洞,多个企业被攻击: https://t.co/xRNBC8HTWR"
-

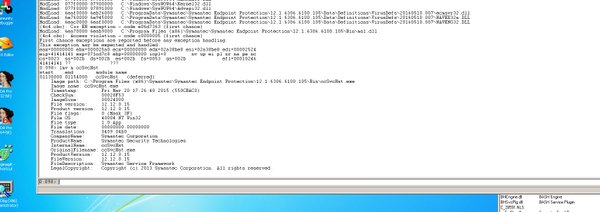
[ SecurityProduct ] Many remote stack overflows in Symantec Endpoint. No big deal, because /GS is the default since 2005, right? Hahaha. https://t.co/ac40M0Ki90
" Symantec 终端防护软件多个栈溢出漏洞(远程)。 Tavis 接着嘲讽两句:没什么大不了的, VS2005 就默认启用 /GS 栈保护了,对吧: https://t.co/ac40M0Ki90"
-

[ Tools ] Excellent Tool - Hasher (Chrome extension) https://github.com/s12v/hasher This has proved very helpful. Let me know what you think.
"Hasher(Chrome 扩展) - 常用 HASH 算法计算工具: https://t.co/QE4fPKX75u "
-

[ Web Security ] WordPress 4.5.1 XSS & SOME: https://gist.github.com/cure53/df34ea68c26441f3ae98f821ba1feb9c https://gist.github.com/cure53/09a81530a44f6b8173f545accc9ed07e Issue was re-found and published, thus the early release.
"WordPress 4.5.1 Flash flashmediaelement.swf 中的 XSS︰ https://t.co/jhdpXGWARz plupload.flash.swf 中的同源方法执行问题: https://t.co/4uzIclKrZu 国内 Seebug 平台关于该漏洞的分析: https://www.seebug.org/vuldb/ssvid-91515 MidZer0 Blog 对该漏洞的分析: https://midzer0.github.io/2016/wordpress-4.5.1-xss/ "
-

[ Windows ] Advisory - ZDI-16-279: (Pwn2Own) Microsoft Windows win32kfull.sys Surface Object Use-After-Free Privilege Escalati… http://ift.tt/1Wmvwai
"ZDI-16-279 公告: Windows 内核 win32kfull.sys Surface 对象 UAF 漏洞,360Vulcan 团队用此漏洞参加的 Pwn2Own 比赛: https://t.co/RN8CC4YWOH"
-

[ Windows ] Advisory - ZDI-16-278: (Pwn2Own) Microsoft Windows xxxEndDeferWindowPosEx Window Use-After-Free Privilege Escalati… http://ift.tt/1TDb8v3
"ZDI-16-278 公告: Windows 内核 win32k.sys xxxEndDeferWindowPosEx UAF 漏洞, 360Vulcan 团队用此漏洞参加的 Pwn2Own 比赛: https://t.co/T6D3kUSX4f"
-

[ Windows ] Advisory - ZDI-16-280: (Pwn2Own) Microsoft Windows NtGdiGetEmbUFI Information Disclosure Vulnerability http://ift.tt/1WmvxLf
" ZDI-16-280: Windows NtGdiGetEmbUFI 信息泄露漏洞(CVE-2016-0174),腾讯电脑管家团队用此漏洞参加的 Pwn2Own 比赛: https://t.co/L6GYbvW0Q7"
-

[ Windows ] Advisory - ZDI-16-281: (Pwn2Own) Microsoft Windows PFFOBJ::bDeleteLoadRef Font Use-After-Free Privilege Escalation… http://ift.tt/1WmvxLj
"ZDI-16-281: Windows 内核 PFFOBJ::bDeleteLoadRef 字体 UAF 漏洞,腾讯电脑管家团队用此漏洞参加的 Pwn2Own 比赛: https://t.co/SABeomn0cs"
-

[ Windows ] I still like this method for collecting endpoint data. "Capture a Network Trace without installing anything" https://blogs.msdn.microsoft.com/canberrapfe/2012/03/30/capture-a-network-trace-without-installing-anything-capture-a-network-trace-of-a-reboot/ #DFIR
" 不装任何软件,在 Windows 系统实现记录网络日志: https://t.co/qy8oGePskZ "
-

[ Windows ] PowerShell now for IE & JS. Thanks COM+ (Weird..) https://gist.github.com/subTee/68749aa53d7ce0fb02e0a64b89615767 PowerShell without PowerShell.exe ;-) Endpoint Vendors->Your Move
" 不依赖 PowerShell.exe 执行 PowerShell 脚本 - 在 IE 中通过 JS 和 COM 执行 PowerShell 脚本: https://t.co/KSomzvcBli "