腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] New post: Netflix and Uber Users: Cybercriminals’ Latest Favored Hacking Targets? http://bit.ly/1pmASo0 @ TrendMicro
"Netflix 和 Uber 用户是目前网络犯罪分子最喜欢的攻击目标, 来自 TrendMicro Blog: https://t.co/lp1IzgyepT"
-

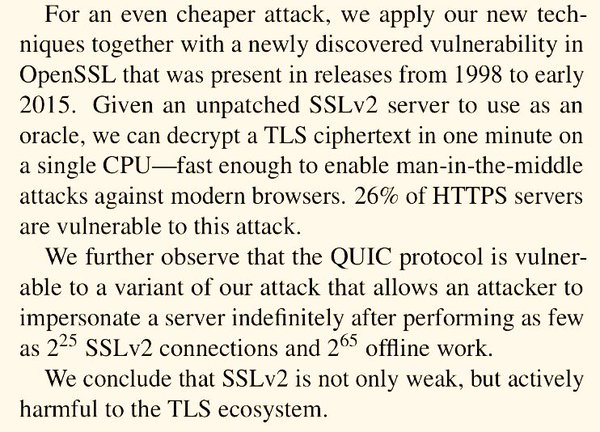
[ Crypto ] Oh, this is more fun than SSLv2… a timing attack! “CacheBleed: A Timing Attack on OpenSSL Constant Time RSA” https://ssrg.nicta.com.au/projects/TS/cachebleed/cachebleed.pdf
"CacheBleed - OpenSSL 常量时间 Timing Attack 攻击, 作者证明了分散聚集(scatter-gather)方法并不能保证时间是个常量. Paper: https://t.co/plH2hTQaD2"
-

[ Defend ] Announcing Windows Defender Advanced Threat Protection http://blogs.windows.com/windowsexperience/?p=110553 https://t.co/FNFr4MY1W5
"微软宣布推出面向企业用户的 Windows Defender 高级威胁保护服务: https://t.co/EqFDoD15kY https://t.co/FNFr4MY1W5"
-

[ Defend ] Learn how #gov is protecting systems from #cyberattacks http://bddy.me/1Rj2pxl #RSAC https://t.co/HOwWliNXvU
"在威胁日益增长的时代,如何构建国家级网络安全计划, 来自 FireEye 的 Paper: https://t.co/z61a7E5MXh https://t.co/HOwWliNXvU"
-

[ Hardware ] PoC for radio transmissions from air-gapped computers: https://github.com/fulldecent/system-bus-radio
"在不借助额外无线电硬件的情况下,从物理隔绝的 PC 中发射无线电. PoC 代码: https://t.co/Fj9Qy6KMry"
-

[ iOS ] neat blog post by one of coworkers: "Tracing Objective-C method calls on ARM64" http://nologic.github.io/blog/2016/02/28/ARM64-method-tracing/ + open source tool :)
" 在 ARM64 上 Trace Objective-C 方法调用, 来自 NoLogic Blog, 作者还开源了他的工具: https://t.co/t9a725mJFq "
-

[ iOS ] iOS 9.3 enables MDM to enforce homescreen layouts, black/whitelist apps, and enforce notification settings https://developer.apple.com/enterprise/ConfigurationProfileReference.pdf
"iOS 9.3 通过启用 MDM 强化主屏幕布局、应用黑/白名单和通知设置, 来自官方 iOS 配置概要手册: https://t.co/fjOqfFYzY9"
-

[ Mac OS X ] Largely undetected Mac malware suggests disgraced HackingTeam has returned http://arstechnica.com/security/2016/02/largely-undetected-mac-malware-suggests-disgraced-hackingteam-has-returned/
"一款 Mac 恶意样本(只有 10/56 的主流杀软可以检测)表明 HackingTeam 归来了, 来自 ArsTechnica 的报道: https://t.co/yyqLo9AaL6 更详细的技术分析: https://reverse.put.as/2016/02/29/the-italian-morons-are-back-what-are-they-up-to-this-time/ "
-

[ Malware ] Angler Attempts to Slip the Hook http://blog.talosintel.com/2016/03/angler-slips-hook.html
"Angler Exploit Kit 一直在更新升级, Talos 这篇 Blog 分析 Angler 最新的一些变化和技巧: https://t.co/sIsJdO1v6V"
-

[ Malware ] New post: Threat Actors Behind “Shrouded Crossbow” Creates BIFROSE for UNIX http://bit.ly/1QRX2uw @ TrendMicro
"TrendMicro 在最近的 'Shrouded Crossbow' 攻击行动中发现,攻击者重写了一个 Unix 版本的 BIFROSE: https://t.co/oug8wS2ErB "
-

[ MalwareAnalysis ] Operation Fingerprint: A Look Into Several Angler Exploit Kit Malvertising Campaigns https://blog.malwarebytes.org/malvertising-2/2016/03/ofp/
"指纹行动(Operation Fingerprint) - Angler Exploit Kit 的几次恶意广告攻击调查, 来自 MalwareBytes 的分析报告: https://t.co/ELeVETRNT6"
-

[ MalwareAnalysis ] Here is our WP on targeted #ransomware and more worryingly "keys are unique for each encrypted file." http://www.intelsecurity.com/advanced-threat-research/content/Analysis_SamSa_Ransomware.pdf
"定向勒索攻击到来了, 来自 IntelSecurity 对 SamSa 勒索软件的分析报告(PDF): https://t.co/cRQ9bis2cZ"
-

[ MalwareAnalysis ] Look Into Locky https://blog.malwarebytes.org/intelligence/2016/03/look-into-locky/
"MalwareBytes 对 Locky 勒索软件的分析: https://t.co/rUGjqvGq7E"
-

[ Network ] Packet Injection Attacks in the Wild https://www.netresec.com/?page=Blog&month=2016-03&post=Packet-Injection-Attacks-in-the-Wild
" 野外数据包注入攻击 - NetreSec 谈我国运营商数据包注入的问题: https://t.co/Nv8fOiuCQv 里面还引用了一篇 Paper 《运营商对网站内容的注入攻击》: http://arxiv.org/abs/1602.07128 "
-

[ Network ] New cross-protocol attack published: DROWN. Shared certs/keys on SSLv2 & TLS gear vulnerable https://www.drownattack.com/drown-attack-paper.pdf https://t.co/P3OJ1OMqRd
"DROWN - 新的跨协议攻击方法, 用 SSLv2 破坏 TLS 加密, Paper: https://t.co/2o66f7b48w 作者还为这个攻击搭建了一个网站 : https://drownattack.com/ "
-

[ Network ] How to get a list of the most common SSL certificate fingerprints in less than 5 seconds: https://asciinema.org/a/37867
"如果通过 Shodan 引擎命令行工具获取最常见的 SSL 证书指纹列表(视频): https://t.co/KlBgRUBRly"
-

[ Others ] "Maths boffins invent lottery prediction system" https://twitter.com/ThomasBaigneres/status/704605514861318145 via @ cryptopathe https://t.co/sKTVTkEgD0
-

[ Others ] Apache Hadoop Tutorial – The ULTIMATE Guide (PDF Download) - #hadoop #java http://buff.ly/1OHlG9P https://t.co/mIRisrUscL
"Apache Hadoop 终极指南 (书): https://t.co/fl8gofEzmP https://t.co/mIRisrUscL"
-

[ Popular Software ] CVE request Qemu: OOB access in address_space_rw leads to segmentation fault: Hello, Qemu emulator built t... http://bit.ly/21zklOY
" Qemu address_space_rw 越界访问拒绝服务漏洞,影响 1.6.0~2.3.1 版本。 安全公告: https://t.co/LhAOchUz5q"
-

[ Tools ] Do you know that @ DidierStevens’s toolbox is available on github (https://github.com/DidierStevens/DidierStevensSuite) or in a zip archive (http://didierstevens.com/files/software/DidierStevensSuite.zip)?
"DidierStevens 开源了他自己的工具库, 主要是一些用于恶意代码分析的工具: https://t.co/kyBcxHLr2W https://t.co/QGTgkyYbXx "
-

[ Tools ] Redress is a cool cross platform binary disassembler written in Java & based on Capstone https://github.com/binarybird/Redress-Disassembler https://t.co/4m29cBlXOq
"Redress - 跨平台的二进制反汇编工具, Java 语言编写,基于 Capstone, Github Repo: https://t.co/N0F27bQLCO https://t.co/4m29cBlXOq"