腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] How to bypass this LG smartphone’s fingerprint security in just 30 seconds http://www.welivesecurity.com/2016/02/16/lg-v10-security-bypass/
"30 秒内绕过 LG 智能手机的指纹解锁, 来自 WeLiveSecurity 的报道: https://t.co/FvVUO6esmj "
-

[ Crypto ] How to Safely Store a Password in 2016 : https://paragonie.com/blog/2016/02/how-safely-store-password-in-2016
"2016 年, 如何安全地存储一个密码? Blog: https://t.co/oRJlX6I8nP"
-

[ Defend ] Users can now access tracker codes using the web, API or our custom command line tools to instantly surface bad. http://blog.passivetotal.org/surfacing-infrastructure-with-trackers/
"PassiveTotal 网站提供了一个 API 服务,用于发现钓鱼站点, 来自 PassiveTotal Blog: https://t.co/8Gy1GTl4hs"
-

[ Detect ] "Creating Your Own Threat Intel Through Hunting & Visualization" by @ raffaelmarty http://www.slideshare.net/zrlram/creating-your-own-threat-intel-through-hunting-visualization
"通过对内部威胁的捕获和可视化构建自己的威胁情报, 来自 Slideshare: https://t.co/2KRJawYv1p"
-

[ Fuzzing ] Extend #aflfuzz mutation routines with Python modules: https://github.com/choller/afl/blob/master/docs/mozilla/python_modules.txt
"用 Python 模块扩展 AFL Fuzz 的变异逻辑, Github Page: https://t.co/XYmLP3BvO2"
-

[ Hardware ] SDR review: AirSpy - SdrPlay RSP - HackRF http://www.rtl-sdr.com/review-airspy-vs-sdrplay-rsp-vs-hackrf/ via @ dotMudge https://t.co/nF5W6xffAj
"SDR 横向比较 - AirSpy vs SdrPlay vs HackRF: https://t.co/nF5W6xffAj FreeBuf 昨天也有一篇相关的文章 《玩跨界?三款最优秀平价SDR对比》: http://www.freebuf.com/tools/96133.html "
-

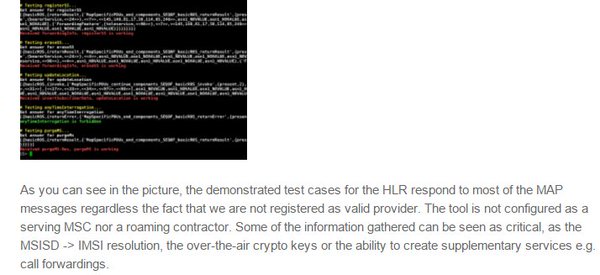
[ Hardware ] SS7 MAP (pen-)testing toolkit code https://github.com/ernw/ss7MAPer post https://www.insinuator.net/2016/02/ss7maper-a-ss7-pen-testing-toolkit/ https://t.co/wcttfCdSHK
"SS7MAPer - SS7 MAP 协议渗透测试工具, Github Repo: https://t.co/WWOhjyASLV Blog: https://t.co/wF50JmILRM https://t.co/wcttfCdSHK"
-

[ Linux ] Do you run Linux and perform DNS queries? Check this glibc RCE (CVE-2015-7547) https://googleonlinesecurity.blogspot.com/2016/02/cve-2015-7547-glibc-getaddrinfo-stack.html and PoC https://github.com/fjserna/CVE-2015-7547
"glibc getaddrinfo 栈缓冲区溢出 RCE (CVE-2015-7547), 影响 2.9 以上所有版本。 来自 Google Online Security Blog: https://t.co/yfyWogU7EH PoC: https://t.co/FweNyG8fOf"
-

[ Linux ] Ntpd ntp-4.2.6p5 ctl_putdata() Buffer Overflow https://cxsecurity.com/issue/WLB-2016020152
"Ntpd ntp-4.2.6p5 ctl_putdata() 缓冲区溢出漏洞(附 PoC), 来自 CXSecurity: https://t.co/teaQLe0ipD"
-

[ Network ] The Art of Network Vulnerability Assessment http://goo.gl/18npJ6 #Hacking #PenetrationTesting
"网络安全漏洞评估的艺术, 来自 InfoSec Blog: https://t.co/2K44gsq26h "
-

[ Pentest ] Automated Derivative Administrator Search - Using graph theory to automate domain admin path finding: https://wald0.com/?p=14
"域内渗透过程中的管理员搜索问题 - 使用图论自动化地查找域管理员路径。 Blog: https://t.co/g8pb4rv8Nj"
-

[ ThirdParty ] RCE in Oracle NetBeans Opensource Plugins: PrimeFaces 5.x Expression Language Injection http://blog.mindedsecurity.com/2016/02/rce-in-oracle-netbeans-opensource.html
"Oracle NetBeans 开源插件 PrimeFaces 5.x 版本存在表达式注入 RCE 漏洞, 来自 Minded Security Blog: https://t.co/WxzG6bcnh0"
-

[ Vulnerability ] Microsoft Internet Explorer Type Confusion https://cxsecurity.com/issue/WLB-2016020145
"IE 类型混淆 PoC(CVE-2016-0061/0063): https://t.co/emVybcOOxH"
-

[ Windows ] How to Check for Dangerous Certificates and Unsigned Windows OS Files http://www.risk3sixty.com/2016/02/16/how-to-check-for-dangerous-certificates-and-unsigned-windows-os-files/
"如何用 Sigcheck 工具检查系统中的危险证书列表和未签名的 Windows 文件, Blog: https://t.co/KWiC5Z7vzf"