腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

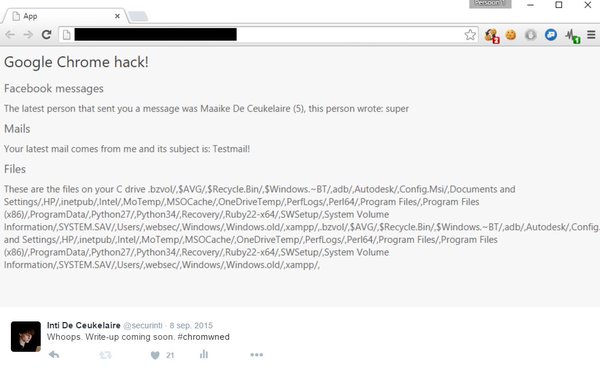
[ Browser ] [WRITE-UP] A tale of two offline @ google Chrome UXSS vulns! http://ceukelai.re/a-tale-of-two-offline-chrome-uxss-vulns/ https://t.co/USZmlbVy2M
"两个离线 Chrome UXSS 漏洞的故事(CVE-2015-6784/CVE-2015-6790) https://t.co/TlBhJ1hFfS https://t.co/USZmlbVy2M"
-

[ Cloud ] Docker Engine 1.10 Security Improvements! It's a bomb dot com release! https://blog.docker.com/2016/02/docker-engine-1-10-security/
"Docker 引擎 1.10 版本在安全方面的一些改进: https://t.co/6YG4x5Vqi2"
-

[ Defend ] Intel Tamper Protection Toolkit - Beta https://software.intel.com/en-us/tamper-protection/details
"Intel 篡改保护工具 Beta 版: https://t.co/HFaCCPnA4q 支持逆向保护和数据篡改保护,相关的文档: https://software.intel.com/en-us/tamper-protection/documentation "
-

[ Hardware ] Barcode recovery using a priori constraints : http://www.windytan.com/2016/02/barcode-recovery-using-priori.html cc: @ windyoona
"使用先验约束的方法还原条形码, Blog: https://t.co/qyBIoxRKq6 "
-

[ iOS ] Bypassing Jailbreak Detection in iOS : https://www.notsosecure.com/2016/02/05/bypassing-jailbreak-detection-ios/
"绕过 iOS 的越狱检测, 来自 NotSoSecure Blog: https://t.co/PdUIOAaWIQ"
-

[ Linux ] Presentation by the "rootkit hunter guy", about intrusion detection and handling. http://www.slideshare.net/MichaelBoelen/handling-of-compromised-linux-systems PDF: http://michaelboelen.com/presentations/
"Linux 入侵检测与防御 - 攻击者是如何进来的、 Rootkit 在哪、 恶意软件如何应对、 如何做好防御。 Slides: https://t.co/uCOm0sWOL4 PDF: https://t.co/iqoC9ixC9u"
-

[ Mac OS X ] Not bad, @ rantyben on the "joys" of fuzzing on MacOS X: https://reverse.put.as/wp-content/uploads/2015/11/OSXScale.pdf
"大规模 Fuzz Mac OS X, 作者为 rantyben, PDF: https://t.co/2FR5kmkIoj "
-

[ MalwareAnalysis ] Using optimization algorithms for malware deobfuscation - http://os2.zemris.fer.hr/ns/malware/2010_spasojevic/diplomski_spasojevic.pdf
"使用优化算法实现恶意软件反混淆, Paper: https://t.co/KC8e6SxM1p"
-

[ MalwareAnalysis ] #Unit42 observed T9000 used in multiple targeted attacks against organizations based in the US. Learn more http://bit.ly/1PYSITG
"模块化的高级后门 T9000 在多个定向攻击中出现, 该后门采用多种复杂的分析对抗技术。 来自 Palo Alto Blog: https://t.co/pmWIw9LN0g"
-

[ Others ] Domain Validation Vulnerability in Symantec Certificate Authority https://www.agwa.name/blog/post/domain_validation_vulnerability_in_symantec_ca
"Symantec 证书颁发过程中在验证域名时存在漏洞: https://t.co/tJ8S1H0MyX "
-

[ ThirdParty ] OpenSSL CVE-2016-0701私钥恢复攻击漏洞分析 - http://blogs.360.cn/blog/openssl%E7%A7%81%E9%92%A5%E6%81%A2%E5%A4%8D%E6%94%BB%E5%87%BB%E6%BC%8F%E6%B4%9Ecve-2016-0701%E5%88%86%E6%9E%90/
"OpenSSL CVE-2016-0701 私钥恢复攻击漏洞分析, 来自 360 Blog, 作者为 au2o3t: https://t.co/5nEXH6d5Jn"
-

[ ThirdParty ] Vulnerability Spotlight: Libgraphite Font Processing Vulnerabilities http://blog.talosintel.com/2016/02/vulnerability-spotlight-libgraphite.html
"Libgraphite 字体处理库存在多个漏洞(CVE-2016-1521/1522/1523/1526), 该库在 Linux、 Firefox、 OpenOffice 中广泛使用, 来自 Talos 对该漏洞的分析: https://t.co/9u2boyyFXW"
-

[ Web Security ] Yahoo RCE : https://seanmelia.files.wordpress.com/2016/02/yahoo-remote-code-execution-cms.pdf (pdf)
"通过雅虎收购的 MGO 公司的漏洞实现雅虎服务器远程代码执行, 漏洞分析报告: https://t.co/bsvtgSQkSh "
-

[ Windows ] Remote Weaponization of WSUS MITM : http://www.sixdub.net/?p=623
"远程 WSUS(Windows 服务器更新服务) 中间人劫持攻击, 来自 sixdub Blog: https://t.co/81XXuVG9MC"
-

[ Windows ] Hacking Microsoft SQL Server Without a Password : https://blog.anitian.com/hacking-microsoft-sql-server-without-a-password/
"仅通过一点数据包操作, 无需密码就 Hacking Microsoft SQL Server: https://t.co/JY6hNExVil"