腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] The 2015 Global Threat Report is live! Download it to discover the latest trends and intelligence to stop breaches: http://ow.ly/XTrLW
"来自 CrowdStrike 的 2015 全球威胁报告: https://t.co/YbCeoKrtYb"
-

[ Attack ] Nuclear EK Leveraged In Large WordPress Compromise Campaign http://blog.malwarebytes.org/exploits-2/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign/
"大规模的 WordPress 攻击行动中发现了 Nuclear EK, 来自 MalwareBytes Blog: https://t.co/mFlXqbg5Sh Securi 的原始分析文章: https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html "
-

[ Browser ] MS Edge priorities in 2016: https://blogs.windows.com/msedgedev/2016/02/03/2016-platform-priorities/ Extensions (of course), HUGE #a11y improvements, and a whole host of new standards
"2016 年微软 Edge 浏览器的开发计划: https://t.co/xATlx2QYYe 回顾 2015 的变化: https://blogs.windows.com/msedgedev/2016/01/21/microsoft-edge-2015-in-review/ "
-

[ Browser ] Comodo's #Chromodo browser disables the same-origin policy - http://ow.ly/XUg3G
"Comodo 的 Chromodo 浏览器禁用了同源策略: https://t.co/dPcBThYe0X"
-

[ Debug ] #DeepSec Video: Building a Better #Honeypot Network:… http://wp.me/p6PE4U-D2 #Defence #InfoSec #Intelligence
"构建一个更好的蜜罐网, 来自 DeepSec 会议的演讲: https://t.co/o3DotSvtxz "
-

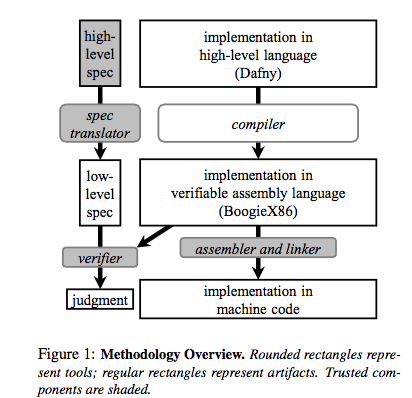
[ Defend ] Ironclad: end-to-end sec w automated verification [priv/intgr; annotation & Floyd-Hoare; Z3] http://research.microsoft.com/pubs/230123/final-osdi-2014.pdf https://t.co/zJdlvMxHrT
"通过自动化地全系统验证实现端到端安全, 来自微软的 Paper: https://t.co/riYRey5XgC https://t.co/zJdlvMxHrT"
-

[ Defend ] Simple, reasonable advice in this one: http://schd.ws/hosted_files/appseccalifornia2016/61/AppSec-PreventingSecurityBugsThroughSoftwareDesign-ChristophKern.pdf https://t.co/HyscRfTOMh
"通过软件设计减少安全漏洞, 来自 Google 的 Christoph Kern 的演讲: https://t.co/OgMUjRCSM8 https://t.co/HyscRfTOMh"
-

[ Defend ] Here are the slides http://bit.ly/1mbklBd for anyone interested in Domain Driven Security that missed @ danbjson and my talk at #DDDEU
"域驱动的安全, 来自 Omegapoint DanielDeogun 的演讲: https://t.co/SHme5OiIki"
-

[ Defend ] KeePassLogger - KeePass Two-Channel Auto-Type Obfuscation (TCATO) Bypass http://www.sinfocol.org/2016/02/keepasslogger-keepass-two-channel-auto-type-obfuscation-bypass/ Source code https://github.com/sinfocol/KeePassLogger
"KeePassLogger - 双通道自动键入混淆保护技术。 这种技术用于防止 Keylogger 截获密码,通过剪贴板和一个键盘模拟机制配合实现保护: https://t.co/ZBYzIp25Ib Github Repo: https://t.co/AvhbOf8f6a"
-

[ Exploit ] how2heap : A repository for learning various heap exploitation techniques : https://github.com/shellphish/how2heap
"how2heap - 几种堆利用技术收集, 包括 unsafe unlink、 单字节置 0 溢出等,都附有 PoC: https://t.co/8PTW7cEYnA"
-

[ Forensics ] OS X Yosemite vs El Capitan: Forensic Artifacts Differences #DFIR http://buff.ly/1PxYb8e
"OS X Yosemite 和 El Capitan 在数字取证方面的一些差异, 来自 Champlain 大学的 Mac OS X 数字取证分析报告: https://t.co/OXGGl4iF7u"
-

[ Fuzzing ] kitty : Fuzzing Framework written in python : https://github.com/cisco-sas/kitty
"kitty - 一个 Python 写的 Fuzz 框架,作者表示写这个框架的目标是为了 Fuzz 一些建立在非 TCP/IP 之上的不常见的协议。 Github Repo: https://t.co/kUwqG3SLp5"
-

[ Industry News ] This report lists >$10M VC investments in security from 2014-2015: http://momentum.partners/docs/Cybersecurity_Market_Review_Q4_2015.pdf I only recognize 3 that I know are useful.
"2014 ~ 2015 安全市场的一些变化,包括投资和收购, 来自 Partners 的报告: https://t.co/mzkE79bztG "
-

[ iOS ] Explaining the race condition recently patched on iOS 9.2 / 9.2.1 kernel exploit https://translate.google.com/translate?sl=auto&tl=en&js=y&prev=_t&hl=en&ie=UTF-8&u=http%3A%2F%2Fblog.pangu.io%2Frace_condition_bug_92%2F&edit-text= (Google translated)
"iOS 9.2/9.2.1 修补的内核漏洞, 来自 盘古团队 Blog: http://blog.pangu.io/race_condition_bug_92/ "
-

[ IoTDevice ] Fisher-Price Smart Toy® & hereO GPS Platform Vulnerabilities https://community.rapid7.com/community/infosec/blog/2016/02/02/security-vulnerabilities-within-fisher-price-smart-toy-hereo-gps-platform
"Fisher-Price 智能玩具和 hereO GPS 手表存在漏洞, 来自 Rapid 7 的 Blog: https://t.co/NdjsKWn3us"
-

[ Mac OS X ] Attacks targeting one #Apple OS could affect the other. Learn about the threat landscape: http://symc.ly/1SDSc2x https://t.co/KM0szb1N1b
"Apple 生态系统的安全现状分析报告, 来自 Symantec 的报告: https://t.co/fmnzIwmXOp https://t.co/KM0szb1N1b"
-

[ MalwareAnalysis ] Debungking a tiny ELF remote backdoor (shellcode shellshock part 2) : http://blog.malwaremustdie.org/2016/02/mmd-0051-2016-debungking-tiny-elf.html
"ELF 远程后门分析 (Shellshock Part 2), 来自 MalwareMustDie Blog: https://t.co/1QvOTiuhhT"
-

[ MalwareAnalysis ] Macro Redux: the Premium Package http://labs.bromium.com/2016/02/03/macro-redux-the-premium-package/
"Macro Redux: Bromium 对最近遇到的一个垃圾邮件中的 Word 样本的分析: https://t.co/LFzIwHAAOO"
-

[ Network ] You should take a look at mitmproxy, a tool that allows interactive examination and modification of HTTP traffic https://mitmproxy.org/
"mitmproxy - 交互式流量劫持工具,允许劫持、修改、重放流量: https://t.co/InOjRBx5U9 "
-

[ Others ] #Unit42 looks at #Emissary Trojan Changelog: Did Operation Lotus Blossom cause it to evolve? http://bit.ly/1R2OaAO
"Emissary 木马更新日志 - 是莲花盛开行动促使它更新的吗? https://t.co/MHaPsCi51V"
-

[ Popular Software ] Quick update made to the #Socat backdoor story: https://threatpost.com/socat-warns-weak-prime-number-could-mean-its-backdoored/116104/ via @ threatpost
"命令行工具 Socat 被怀疑植入后门, 弱质数可能就意味着存在后门, 来自 ThreatPost 报道: https://t.co/KKU430X2n3"
-

[ SecurityProduct ] A remote filesystem access vulnerability in the default Avast install. https://code.google.com/p/google-security-research/issues/detail?id=679
"Avast 文件系统任意文件远程读取漏洞, 来自 Project Zero Issue 679, Avast 存在一个通过 Web 页面可访问的 RPC 接口,通过这个接口可以启动一个无安全限制的 'SafeZone', 通过 SafeZone,可以任意读取文件系统文件,发送任意 HTTP 请求,读取响应,截获 Cookie等: https://t.co/mUkbksUacT"
-

[ ThirdParty ] Summing this up for you: Non-Chromium WebKit security for Linux is a tire fire. https://blogs.gnome.org/mcatanzaro/2016/02/01/on-webkit-security-updates/
"Michael Catanzaro 谈 Linux 发行版更新 WebKit 不及时的安全问题: https://t.co/SxFbs5Wjwb"
-

[ ThirdParty ] openssl_seal() is prone to use uninitialized memory that can be turned into a code execution http://akat1.pl/?id=1
"openssl_seal()、 PHP 和 Apache2handle 的故事, 介绍了一个 openssl_seal 函数的为初始化内存漏洞转化代码执行的利用过程: https://t.co/9zhRsElV5T"
-

[ Tools ] XXEinjector : Tool for automatic exploitation of XXE vulnerability using direct and different out of band methods : https://github.com/enjoiz/XXEinjector
"XXEinjector: XXE 漏洞自动利用工具: https://t.co/rjhcpbvCA1"
-

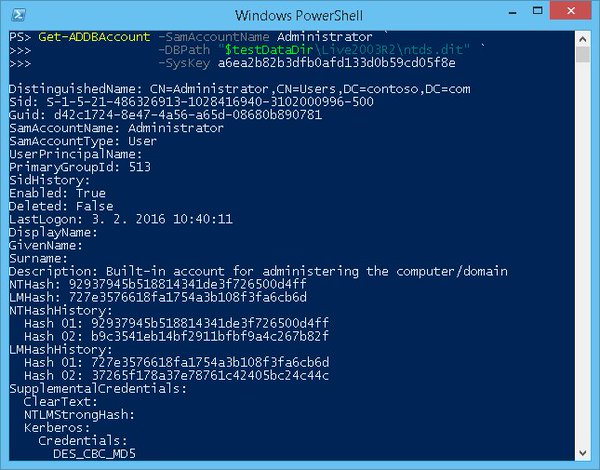
[ Tools ] New version of the #DSInternals PowerShell Module, now with Windows Server 2003 support. https://github.com/MichaelGrafnetter/DSInternals/releases https://t.co/FPXJvrzEJi
"新版本的 DSInternals PowerShell 模块支持 Windows Server 2003 了, DSInternals 导出了一些 Active Directory 的内部和未文档化的接口: https://t.co/cEhDAl4wNl https://t.co/FPXJvrzEJi"
-

[ Tools ] Codetainer-A Docker Container In Your Browser http://www.kitploit.com/2015/11/codetainer-docker-container-in-your.html Allows you to create code 'sandboxes' you can embed in your web apps
"Codetainer - 浏览器里的 Docker 容器: https://t.co/SuJE2B6hQ3 "
-

[ Web Security ] The Magic of Connecting The Dots : https://respectxss.blogspot.de/2016/01/the-magic-of-connecting-dots.html cc: @ soaj1664ashar
"连线的魔法(XSS): https://t.co/V9a59zT3bJ "
-

[ Web Security ] The latest @ WordPress update fixes both a SSRF and Open Redirect vuln -http://ow.ly/XU2Ne https://t.co/m0FQjBQItP
"最新版 WordPress 4.4.2 修复了一个 SSRF 和重定向漏洞, 来自 ThreatPost 的报道: https://t.co/uG0lWxzljd https://t.co/m0FQjBQItP"
-

[ Windows ] Bypass Windows AppLocker http://en.wooyun.io/2016/01/28/Bypass-Windows-AppLocker.html
"Bypass Windows AppLocker, 来自 Wooyun Drops, 作者 ID 为 三好学生: https://t.co/WUgAhEOeu3"
-

[ Windows ] .@ rckashyap @ vadimkotov I've discussed the RTF-dropping-exe (in fact, any file) trick & the risks back to July 2014 https://blogs.mcafee.com/mcafee-labs/dropping-files-temp-folder-raises-security-concerns.
"把文件释放到临时文件夹提高了安全风险, 来自 McAfee 2014 年 7 月的 Blog, 作者为 Haifei Li, 其中作者讨论了 RTF 释放 exe 的技巧: https://t.co/NQB6pG7UEx 还有一篇 Haifei Li 写的关于这个话题文章参考: http://justhaifei1.blogspot.com/2014/08/demonstration-of-windowsoffice-insecure.html "