腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] V8 garbage collector (GC) 原理详细介绍: https://v8.dev/blog/trash-talk
-

[ Challenges ] 为初学者建立的包含大量 CTF 赛题的网站 : https://twitter.com/matalaz/status/1080776104544268288
-

[ Fuzzing ] neuzz - 基于神经网络的 fuzzer: https://github.com/Dongdongshe/neuzz
-

[ Industry News ] NSA 开发的逆向工程框架 GHIDRA 将在 RSA 上发布: https://www.rsaconference.com/events/us19/agenda/sessions/16608-Come-Get-Your-Free-NSA-Reverse-Engineering-Tool
-

[ Malware ] 在没有 execve 的情况下如何运行 Linux 可执行文件: https://blog.rapid7.com/2019/01/03/santas-elfs-running-linux-executables-without-execve/
-

[ MalwareAnalysis ] 通过 FTP 泄漏数据的恶意脚本分析: https://isc.sans.edu/forums/diary/Malicious+Script+Leaking+Data+via+FTP/24484/
-

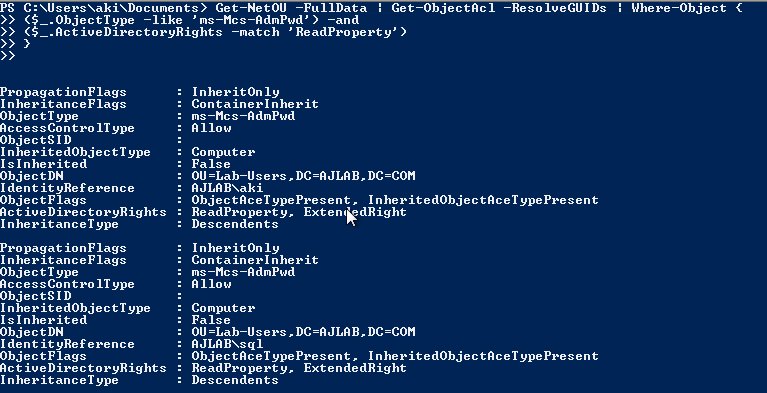
[ Pentest ] 通过滥用 Microsoft LAPS 可窃取用户密码: https://akijosberryblog.wordpress.com/2019/01/01/malicious-use-of-microsoft-laps/
-

[ SecurityAdvisory ] Adobe 发布安全公告,包括对两个严重漏洞的修复(CVE-2018-16011、CVE-2018-16018): https://helpx.adobe.com/security/products/acrobat/apsb19-02.html
-

[ Tools ] Windows-Kernel-Explorer - 一款 Windows 内核研究工具: https://github.com/AxtMueller/Windows-Kernel-Explorer
-

[ Tools ] XML 外部实体注入漏洞资源及工具整理: https://twitter.com/i/web/status/1080877419723194370
-

[ Tools ] binbag - 一款类似 toolbox 的 iOS 端命令行工具包: http://newosxbook.com/tools/iOSBinaries.html
-

[ Attack ] 如何利用内存重复数据删除技术读系统任意数据(Paper) : https://www.cs.vu.nl/~herbertb/download/papers/dedup-est-machina_sp16.pdf
-

[ MalwareAnalysis ] 云托管提供商 DataResolution.net 在平安夜遭受 Ryuk 勒索软件攻击的事件解析: https://krebsonsecurity.com/2019/01/cloud-hosting-provider-dataresolution-net-battling-christmas-eve-ransomware-attack/
-