腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Fuzzing 的开发与改进: https://gamozolabs.github.io/fuzzing/2018/10/18/terrible_android_fuzzer.html
-

[ Browser ] 利用 Safari 的域名处理问题绕过 XSS 黑名单限制: https://labs.detectify.com/2018/10/19/xss-using-a-bug-in-safari-and-why-blacklists-are-stupid/
-

[ Exploit ] CTF BlazeFox 的 Exploit 代码: https://github.com/Kondara/BlazeFox
-

[ MalwareAnalysis ] 攻击者滥用 SettingContent-ms 文件来安装木马后门,TrendMicro 对此作出了技术分析: https://blog.trendmicro.com/trendlabs-security-intelligence/settingcontent-ms-can-be-abused-to-drop-complex-deeplink-and-icon-based-payload/
-

[ Pentest ] 通过 osint 和 datasploit 来获取行为信息: https://www.exploit-db.com/docs/english/45543-detecting-behavioral-personas-with-osint-and-datasploit.pdf
-

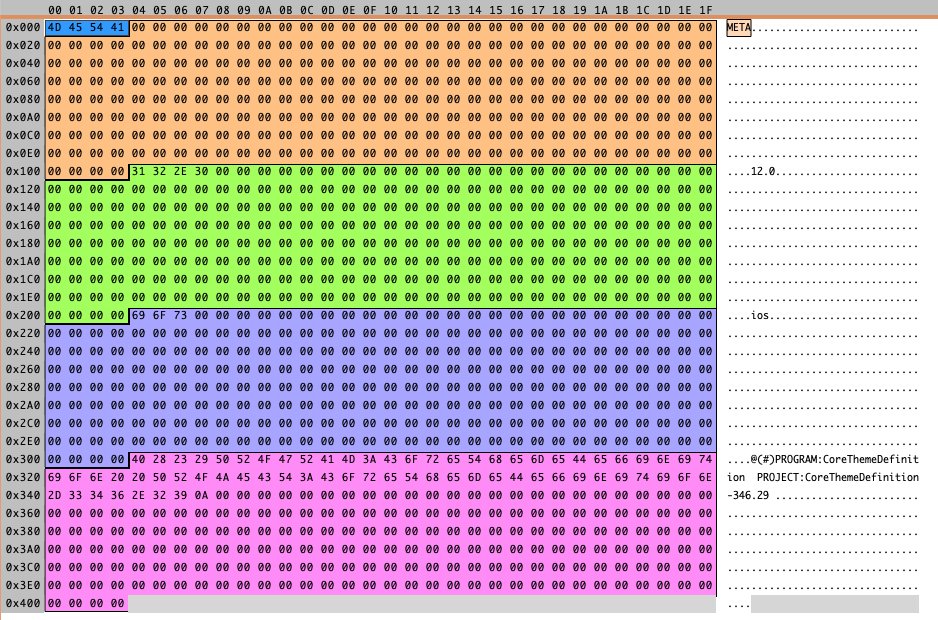
[ ReverseEngineering ] .car 文件格式逆向分析介绍 : https://blog.timac.org/2018/1018-reverse-engineering-the-car-file-format/
-

[ Tools ] 使用 IDAPython 自动映射二进制文件替换默认函数名: https://0xgalz.github.io/
-

[ Tools ] testssl.sh - 可以用来测试 SSL 安全性的工具: https://www.darknet.org.uk/2018/10/testssl-sh-test-ssl-security-including-ciphers-protocols-detect-flaws/
-

[ Tools ] Microcode - 逆向 x86 处理器微码的框架和示例程序: https://github.com/RUB-SysSec/Microcode
-

[ Tools ] MEOW HASH - 一种快速的用于非加密的 hash: https://mollyrocket.com/meowhash