腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

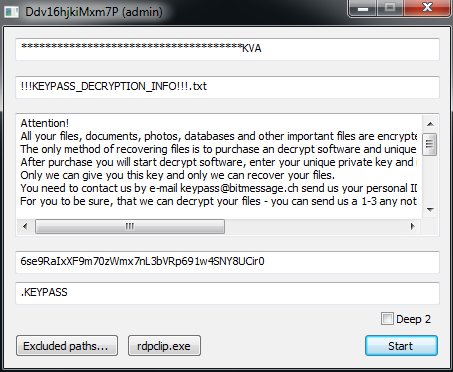
[ Android ] Android - 通过注入 blkid 输出遍历 USB 目录(CVE-2018-9445): https://www.exploit-db.com/exploits/45192/
-

[ Android ] 攻破 "最艰难的目标":赢得 ASR 项目历史上最多奖金的利用链通过一个 V8 漏洞破坏渲染进程,一个 system_server 漏洞逃离沙箱并获取 System 权限: https://github.com/JiounDai/slides/blob/master/Pwning%20the%20toughest%20target%20%E2%80%94%20the%20exploit%20chain%20of%20winning%20the%20largest%20bug%20bounty%20in%20the%20history%20of%20ASR%20program.pdf
-

[ Browser ] WebRTC RtpFrameReferenceFinder::MissingRequiredFrameVp9 越界内存读取漏洞披露(CVE-2018-6129): https://bugs.chromium.org/p/chromium/issues/detail?id=838672
-

[ Detect ] 检测 .NET 的恶意使用 - Part 1: https://countercept.com/our-thinking/detecting-malicious-use-of-net-part-1/
-

[ Detect ] 使用 YARA 规则进行威胁狩猎: https://pylos.co/2018/08/13/yara-for-hunting/
-

[ Hardware ] 如何滥用x86 / x64 CPU "Feature" 的高级错误来实现多个操作系统上的本地特权提升: https://docs.google.com/presentation/d/1Z9p2iZuysTmkPIC2BdcDbQOCSnVwhaHfrPdzGiStLHI/edit#slide=id.g3e40cb6e62_0_684
-

[ Hardware ] The unbearable lightness of BMC,BMC 的攻击面分析和漏洞挖掘及演示,来自 BlackHat USA 2018: http://i.blackhat.com/us-18/Wed-August-8/us-18-Waisman-Soler-The-Unbearable-Lightness-of-BMC.pdf
-

[ Linux ] 了解 Linux 可执行文件的内存布局: https://gist.github.com/CMCDragonkai/10ab53654b2aa6ce55c11cfc5b2432a4
-

[ MachineLearning ] 使用循环神经网络检测 Web 攻击: https://aivillage.org/posts/detecting-web-attacks-rnn/
-

[ macOS ] patrick wardle 在今年 BlackHat 及 DEF CON 上的演讲 1)冰与火:创建与破坏 macOS 防火墙: https://speakerdeck.com/patrickwardle/fire-and-ice-making-and-breaking-macos-firewalls ; 2)通过 "组合" 鼠标点击攻击 macOS: https://speakerdeck.com/patrickwardle/the-mouse-is-mightier-than-the-sword
-

[ macOS ] macOS 端点安全软件自我保护功能研究: https://www.mdsec.co.uk/2018/08/endpoint-security-self-protection-on-macos/
-

[ macOS ] 攻击 macOS 内核图形驱动,来自 DEFCON 26: https://media.defcon.org/DEF%20CON%2026/DEF%20CON%2026%20presentations/DEFCON-26-Yu-Wang-Attacking-The-MacOS-Kernel-Graphics-Driver.pdf
-
-

[ MalwareAnalysis ] Osiris 银行木马的下载者程序同时使用了 Process Doppelgänging 和 Process Hollowing 两种技术,来自 Malwarebytes 的分析: https://blog.malwarebytes.com/threat-analysis/2018/08/process-doppelganging-meets-process-hollowing_osiris/
-

[ Mobile ] Exploitation of a Modern Smartphone Baseband,现代智能手机基带的利用,来自 BlackHat USA 2018 : https://speakerdeck.com/marcograss/exploitation-of-a-modern-smartphone-baseband
-

[ OpenSourceProject ] 开源商店系统 OXID eShop 中的用户权限提升漏洞分析(CVE-2016-5072): https://mogwailabs.de/blog/2018/07/vulnerability-spotlight-cve-2016-5072/
-

[ Others ] Another Flip in the Row,介绍了 rowhammer 一些新的进展和研究,主要包含定向 rowhammer,指令翻转等新的攻击方法,来自 BlackHat USA 2018: https://gruss.cc/files/us-18-Gruss-Another-Flip-In-The-Row.pdf
-

[ Others ] Burpsuite 新型 Scanner 支持对 JavaScript 的动态分析: https://portswigger.net/blog/dynamic-analysis-of-javascript
-

[ SecurityProduct ] 如何远程枚举杀毒软件配置信息: https://www.fortynorthsecurity.com/remotely-enumerate-anti-virus-configurations/
-

[ Tools ] Blind-Bash - bash 脚本混淆项目: https://github.com/Rizer0/Blind-Bash
-
-

[ Tools ] Juicy Potato 本地特权提升工具(RottenPotatoNG加强版):版): https://ohpe.github.io/juicy-potato/ h/
-

[ Tools ] x41-smartcard-fuzzing - 智能卡驱动 Fuzzing 工具: https://github.com/x41sec/x41-smartcard-fuzzing
-
-

[ Vulnerability ] Oracle 数据库服务器的 Java VM 组件漏洞警告(CVE-2018-3110): http://www.oracle.com/technetwork/security-advisory/alert-cve-2018-3110-5032149.html
-

[ Vulnerability ] 惠普 OfficeJet 一体式喷墨打印机中的传真协议存在两处严重漏洞,可让攻击者完全控制打印机,来自 DEF CON 26 上 Check Point 安全研究人员公开了漏洞细节: https://threatpost.com/def-con-2018-critical-bug-opens-millions-of-hp-officejet-printers-to-attack/134972/