腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] 对 Android 操作系统的安全性分析:每4000行 C++ 代码就存在一个潜在漏洞: https://medium.com/@CPP_Coder/android-operating-system-one-potential-vulnerability-per-4000-lines-of-c-code-85041585927b
-

[ Android ] WEDDINGCAKE Android ELF 解密脚本: https://github.com/maddiestone/IDAPythonEmbeddedToolkit/tree/master/Android
-

[ Backdoor ] rosenbridge - x86 CPU 硬件后门项目: https://github.com/xoreaxeaxeax/rosenbridge
-

[ Browser ] “Double Kill” Internet Explorer Zero-Day(CVE-2018-8174)利用中所使用的 DLL 地址泄漏技巧: https://www.fortinet.com/blog/threat-research/analysis-of-dll-address-leaking-trick-used-by-double-kill-internet-explorer-0-day-exploit.html
-

[ Fuzzing ] Fuzzlyn 项目可以生成随机的 C# 程序,通过优化和未优化代码之间的差异,找到了多个.NET JIT错误: https://twitter.com/i/web/status/1027224393217449986相关项目和漏洞的补丁链接: 1) https://github.com/jakobbotsch/Fuzzlyn 2) https://github.com/dotnet/roslyn 3) https://github.com/dotnet/coreclr/issues?utf8=%E2%9C%93&q=is%3Aissue+author%3Ajakobbotsch
-

[ Industry News ] 针对比特币 ATM 的恶意软件突然在地下黑客论坛出现: https://blog.trendmicro.com/trendlabs-security-intelligence/malware-targeting-bitcoin-atms-pops-up-in-the-underground/
-

[ Linux ] Linux Kernel 4.14.7 (Ubuntu 16.04 / CentOS 7) - (KASLR & SMEP 绕过) 任意文件读取(CVE-2017-18344): https://www.exploit-db.com/exploits/45175/
-

[ MachineLearning ] Protecting the protector:强化机器学习防御对抗性攻击,来自 BlackHat USA 2018 上 Microsoft 安全研究员们的议题解读: https://cloudblogs.microsoft.com/microsoftsecure/2018/08/09/protecting-the-protector-hardening-machine-learning-defenses-against-adversarial-attacks/
-

[ MalwareAnalysis ] Osiris 银行木马的下载者使用了 doppelgänging 技术,Malwarebytes 对此做了详细的技术分析: https://blog.malwarebytes.com/threat-analysis/2018/08/osiris-using-process-doppelganging/
-

[ MalwareAnalysis ] 代码重用分析揭示出朝鲜恶意软件家族中未被发现的联系: https://securingtomorrow.mcafee.com/mcafee-labs/examining-code-reuse-reveals-undiscovered-links-among-north-koreas-malware-families/
-

[ Pentest ] 活动目录安全技术分享 - 如何从工作站获取域管权限,来自 BlackHat USA 2018 上 Sean Metcalf 的演讲: http://i.blackhat.com/us-18/Wed-August-8/us-18-Metcalf-From-Workstation-To-Domain-Admin-Why-Secure-Administration-Isnt-Secure.pdf
-

[ SecurityReport ] 你的股票交易安全吗?交易技术中的安全漏洞揭示白皮书,来自 IOActive : https://ioactive.com/wp-content/uploads/2018/08/Are-You-Trading-Stocks-Securely-Exposing-Security-Flaws-in-Trading-Technologies.pdf
-

[ Symbolic Execution ] 使用符号执行分析安全协议的实现,重点介绍了如何使用符号执行处理协议中的加密模块(Paper): https://papers.mathyvanhoef.com/woot2018.pdf
-

[ Tools ] darling - 在 Linux 上模拟 macOS 的工具: https://github.com/darlinghq/darling
-

[ Tools ] honeyku - 基于 Heroku 的 Web 蜜罐: https://github.com/0x4D31/honeyku
-

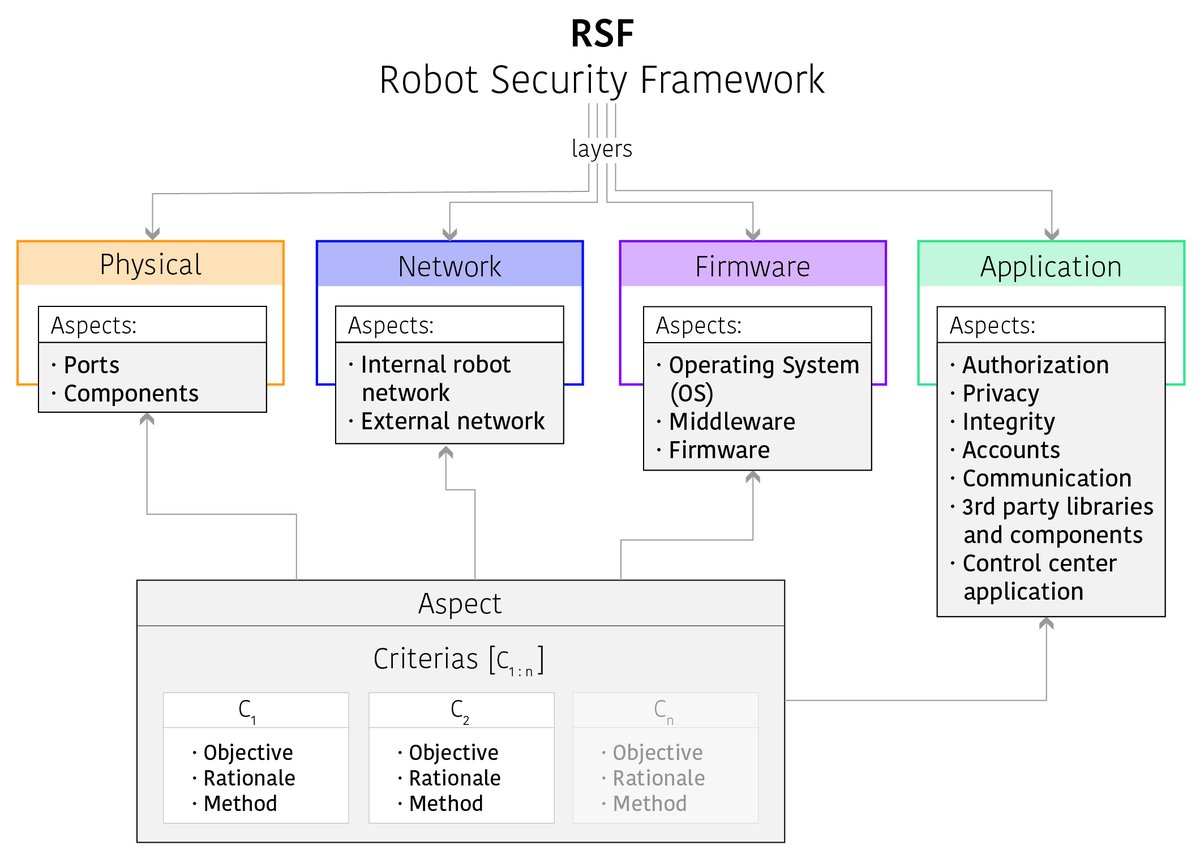
[ Tools ] RSF 机器人安全框架,对机器人技术进行安全评估的标准化方法: https://aliasrobotics.com/research/rsf.htm https://github.com/aliasrobotics/RSF
-

[ Tools ] 逆向工程框架 - Miasm2,作者通过 IR 实现了符号执行,虚拟机对抗和shellcode 模拟执行等功能,来自 BlackHat USA 2018 : http://i.blackhat.com/us-18/Wed-August-8/us-18-DesclauxMougey-Miasm-Reverse-Engineering-Framework.pdf
-
-

[ Web Security ] Web 缓存投毒技术详解: https://portswigger.net/blog/practical-web-cache-poisoning
-

[ Windows ] BlackHat USA 2018 上绕过缓解机制实现内核模式无文件攻击,来自 Threatpost 报道: https://threatpost.com/stealthy-new-kernel-attack-flies-under-windows-mitigation-radar/134847/
-

[ WirelessSecurity ] 逆向分析日产无线 SD 卡 - 从零开始到代码执行,来自 BlackHat USA 2018 上 Guillaume VALADON 的演讲: https://docs.google.com/presentation/d/13OJNOb2IMwp79SDrbxSLF3i7StTgWLdD7QlYpic39r8/edit#slide=id.g3d28bb72e8_5_74
-
-

[ iOS ] iOS越狱细节揭秘:危险的用户态只读内存,来自腾讯科恩实验室Black Hat USA 2018 的议题解读: https://mp.weixin.qq.com/s/Ns5pfynw0FHU9myiufAreg
-

[ iOS ] iOS 越狱内幕(2):通过回调逃离沙箱: https://media.weibo.cn/article?id=2309404271293301154324&jumpfrom=weibocom&sudaref=t.co&display=0&retcode=6102
-
-

[ MalwareAnalysis ] 使用多种逃避技术的恶意宏分析: http://www.pwncode.club/2018/08/macro-used-to-spoof-parent-process.html
-
-

[ Vulnerability ] syscall_exploit_CVE-2018-8897: POP/MOV SS (CVE-2018-8897) 漏洞本地提权利用: https://github.com/nmulasmajic/syscall_exploit_CVE-2018-8897