腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android P 中基于编译器的安全缓解措施(CFI 及检查整数溢出措施)介绍: https://android-developers.googleblog.com/2018/06/compiler-based-security-mitigations-in.html
-

[ Android ] 借助 Systematic Mutation 发现 Android 静态分析工具中的缺陷: https://arxiv.org/pdf/1806.09761.pdf
-

[ Browser ] Microsoft 为 iOS 及 Android 版本的 Edge 内置了 ad blocker: https://www.theverge.com/2018/6/25/17500318/microsoft-edge-android-ad-blocker-built-in
-

[ Challenges ] Google CTF 2018 初赛 Web 挑战 - gCalc 的解题报告: http://blog.orange.tw/2018/06/google-ctf-2018-quals-web-gcalc.html
-

[ Compiler ] Clang 编译函数的详细流程讲解: https://blog.regehr.org/archives/1605
-

[ Conference ] Recon Mtl 2018 大会议题材料放出: https://recon.cx/2018/montreal/schedule/speakers.html
-

[ Hardware ] 逆向分析一款 TI 生产的运算放大器芯片,主要是分析了其晶元(silicon die)里面的一个“蝴蝶形”晶体管: http://www.righto.com/2018/06/silicon-die-analysis-op-amp-with.html
-

[ Hardware ] Overcoming (some) Spectre browser mitigations,文中主要讲了CPU缓存与原理以及不同浏览器的缓解措施并如何绕过缓解措施: https://alephsecurity.com/2018/06/26/spectre-browser-query-cache/
-

[ IoTDevice ] 许多品牌的网络摄像头都存在默认密码问题,导致攻击者可以轻易接管摄像头窥视用户: https://www.bleepingcomputer.com/news/security/someone-is-taking-over-insecure-cameras-and-spying-on-device-owners/
-

[ Others ] ASLR 对静态链接的可执行文件的保护: https://www.leviathansecurity.com/blog/aslr-protection-for-statically-linked-executables
-

[ Others ] Mach-O 格式中的改变介绍: https://lief.quarkslab.com/doc/latest/tutorials/11_macho_modification.html
-

[ Pentest ] SQL Server 登录触发器限制绕过: https://blog.netspi.com/bypass-sql-logon-triggers/
-

[ Pentest ] NTLM 中继攻击介绍: https://www.coresecurity.com/blog/playing-relayed-credentials
-

[ Tools ] linux-kernel-exploitation - Linux 内核漏洞利用资源收集仓库: https://github.com/xairy/linux-kernel-exploitation/blob/master/README.md
-

[ Tools ] certs - 解析 X509 证书并从中提取子域名的工具: https://github.com/smiegles/certs
-

[ Tools ] 使用 IDA Python 进行相似漏洞搜索: https://www.zerodayinitiative.com/blog/2018/6/26/mindshare-variant-hunting-with-ida-python
-

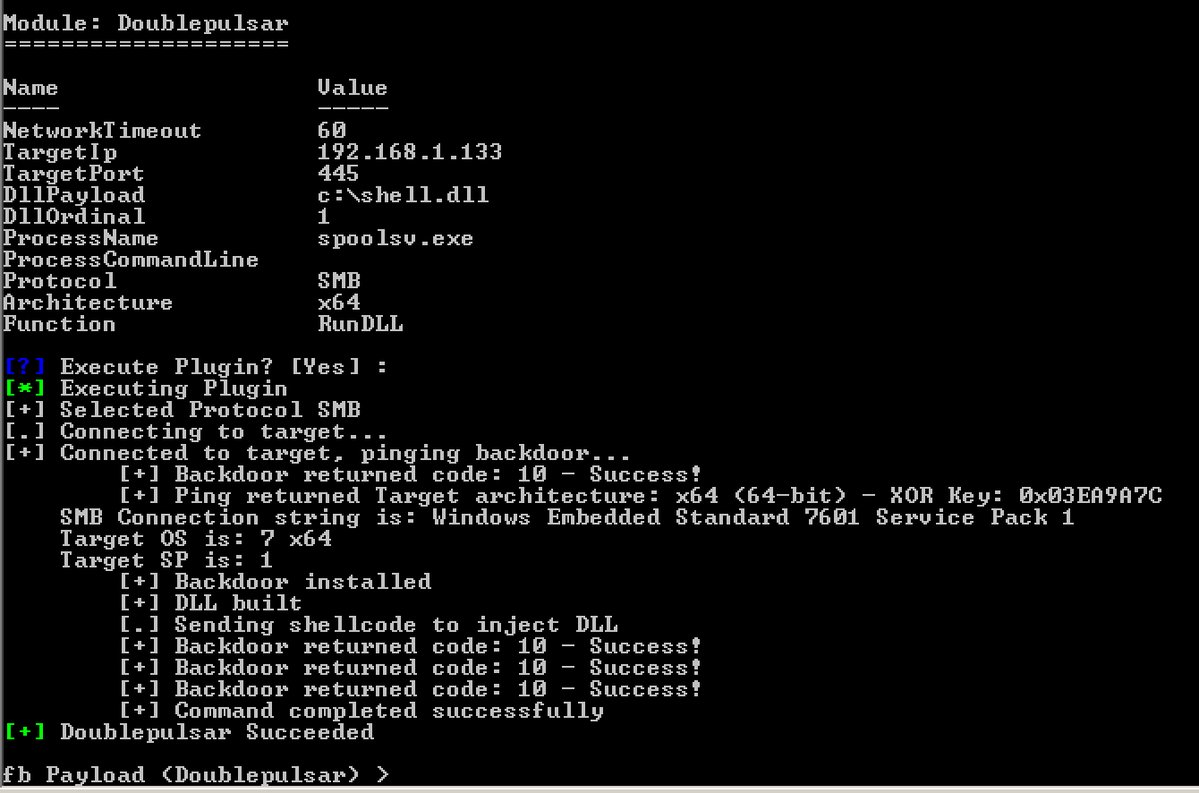
[ Windows ] 修改 DoublePulsar 以完成在 Windows 嵌入式系统上的 EternalBlue 漏洞利用: https://capt-meelo.github.io/pentest/2018/06/26/patching-doublepulsar.html
-
-
-

[ Conference ] MOSEC议题解读 1)PWN2OWN shannon基带破解之旅: https://www.anquanke.com/post/id/149698 2)A Look back at iBoot : https://www.anquanke.com/post/id/149549 3)Build your own iOS kernel debugger: https://www.anquanke.com/post/id/149551 4)Bread——接踵而来的短信诈骗: https://www.anquanke.com/post/id/149446
-
-
-
-

[ MalwareAnalysis ] 2016-2018年,勒索软件与恶意加密货币矿工的此消彼长,来自 Kaspersky 的统计分析报告: https://securelist.com/ransomware-and-malicious-crypto-miners-in-2016-2018/86238/
-

[ SecurityReport ] McAfee Labs 发布 6 月威胁报告: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-jun-2018.pdf
-
-

[ Tools ] CrowdStrike 发布 Office 365 取证工具: https://lmgsecurity.com/exposing-the-secret-office-365-forensics-tool/
-

[ Windows ] Windows 持久化攻击方式分析 Part 1,主要介绍恶意软件建立持久化所使用的方法: https://redcanary.com/blog/active-breach-establishing-persistence/