腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Backdoor ] Backdooring PE-File (with ASLR),向 PE 文件注入后门: https://hansesecure.de/backdooring-pe-file-with-aslr/
-

[ Browser ] Safari 技术预览版 59 发布: https://webkit.org/blog/8332/release-notes-for-safari-technology-preview-59/
-

[ Browser ] Wavethrough - 通过多媒体音频(Audio)相关的 API 绕过浏览器的同源策略,获取敏感信息,Edge(CVE-2018-8235)和 Firefox 浏览器受影响: https://jakearchibald.com/2018/i-discovered-a-browser-bug/
-

[ Cloud ] Azure AD 混合身份认证与密码难度检测: https://www.xtseminars.co.uk/blog/azure-ad-hybrid-identity-and-banned-password-detection
-

[ Fuzzing ] afl-fuzz 在不同文件系统上的性能对比: https://barro.github.io/2018/06/afl-fuzz-on-different-file-systems/
-

[ Industry News ] 据报道,Microsoft 将把 Windows 10 和 Linux 移植到了自制的E2 CPU 上: https://www.theregister.co.uk/2018/06/18/microsoft_e2_edge_windows_10/
-

[ iOS ] 针对 iOS 12 kernelcache 中的 tagged pointer 改动分析: https://bazad.github.io/2018/06/ios-12-kernelcache-tagged-pointers/
-
-

[ Malware ] Sucuri 安全人员发现 Hacker 利用 URL 短地址跳转进行加密货币挖矿: https://blog.sucuri.net/2018/05/cryptomining-through-disguised-url-shorteners.html
-

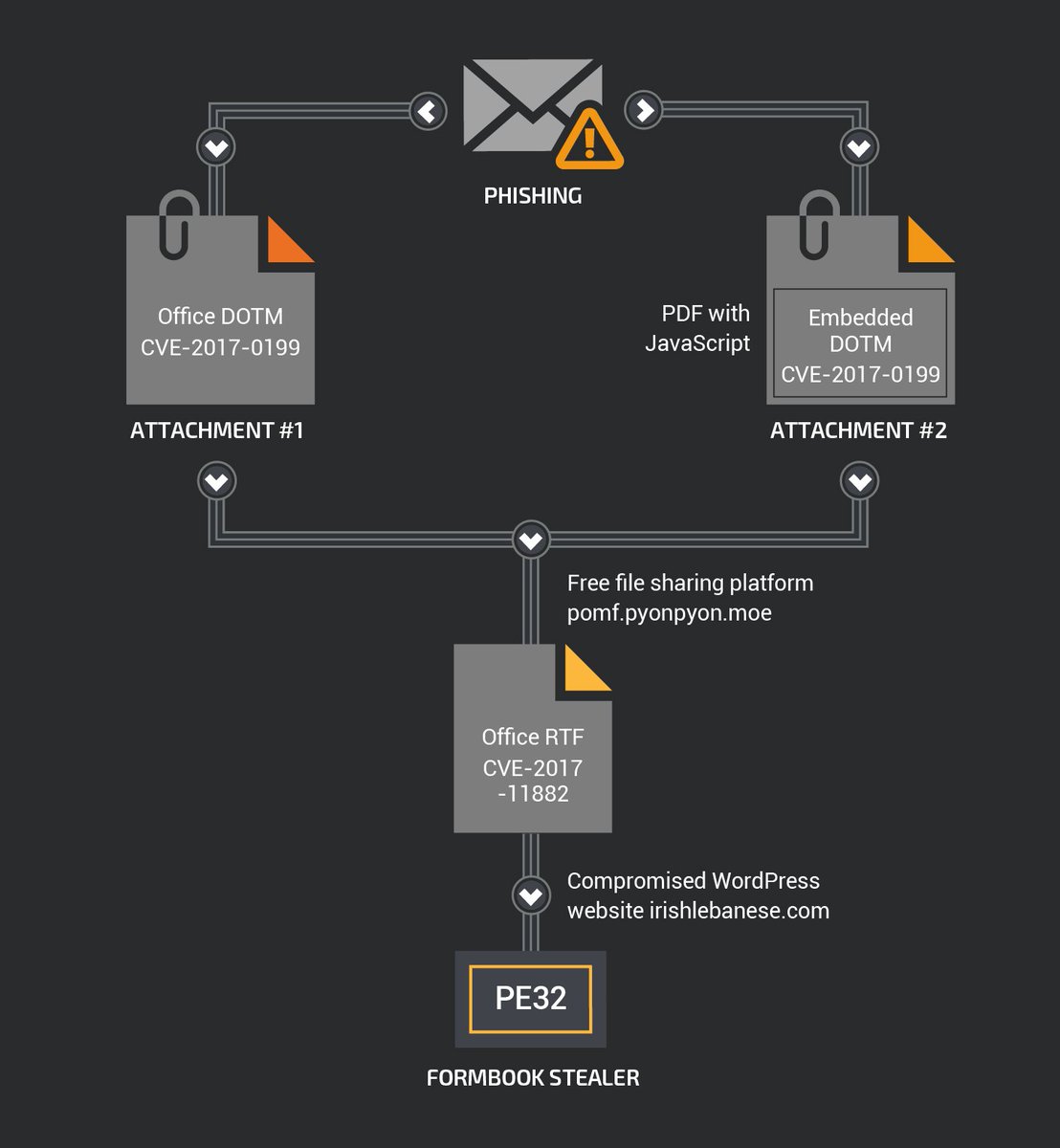
[ MalwareAnalysis ] Cisco 对最近使用了 FormBook 恶意软件的活动的分析 : https://blog.talosintelligence.com/2018/06/my-little-formbook.html
-

[ Pentest ] 使用 DNS Rebinding 从互联网攻击内网设备: https://medium.com/@brannondorsey/attacking-private-networks-from-the-internet-with-dns-rebinding-ea7098a2d325
-

[ Pentest ] 滥用 WMI Providers 实现持久化,来自 BSIDESTLV 大会: https://www.slideshare.net/PhilipTsukerman/abusing-wmi-providers-for-persistence-bsidestlv
-

[ Pentest ] AWS 特权升级漏洞介绍: https://rhinosecuritylabs.com/aws/aws-privilege-escalation-methods-mitigation/
-

[ Pentest ] 通过 Java Bundles 获取 Apache Felix 的反弹 Shell : https://posts.specterops.io/shelling-apache-felix-with-java-bundles-2450d3a099a
-

[ Pentest ] 关于 PowerShell AMSI 规避技术相关的文章阅读推荐: https://twitter.com/breakersall/status/1009463922745860099
-

[ Popular Software ] IPConfigure Orchid Core VMS 中未经身份验证的目录遍历漏洞披露(CVE-2018-10956): https://labs.nettitude.com/blog/cve-2018-10956-unauthenticated-privileged-directory-traversal-in-ipconfigure-orchid-core-vms/
-

[ Popular Software ] Apache CouchDB < 2.1.0 远程代码执行漏洞 exp(CVE-2017-12636 ): https://www.exploit-db.com/exploits/44913/
-

[ ReverseEngineering ] GalaXyHaXz 通过泄漏的符号文件逆向了暗黑破坏神(Diablo)游戏,并公布了源码: https://twitter.com/i/web/status/1009510552194838528
-

[ Tools ] pure-bash-bible - 通过 bash 实现其他常用功能的方式收集: https://github.com/dylanaraps/pure-bash-bible
-

[ Tools ] HookMsrBySVM - 通过 AMD SVM Hook msr 以监视 x64 中的系统调用: https://github.com/hrbust86/HookMsrBySVM
-

[ Tools ] 查询 MITRE ATT&CK 数据库的 PowerShell 脚本发布: https://github.com/SadProcessor/SomeStuff/blob/master/PoSh_ATTCK.ps1
-

[ Tools ] BOLT - 一款 Linux 下的二进制代码优化工具: https://github.com/facebookincubator/BOLT
-

[ Web Security ] Paloalto 对基于 Web 的威胁趋势分析: https://researchcenter.paloaltonetworks.com/2018/06/unit42-the-old-and-new-current-trends-in-web-based-threats/
-

[ Web Security ] 通过 CRLF 注入在 Chromium 中设置任意请求头: https://blog.bentkowski.info/2018/06/setting-arbitrary-request-headers-in.html
-
-
-

[ Malware ] Netflix 新型钓鱼开始使用具有有效 TLS 证书的站点: https://threatpost.com/new-phishing-scam-reels-in-netflix-users-to-tls-certified-sites/132976/
-

[ MalwareAnalysis ] 安全研究人员发现了一种使用高复杂度逃避技术的 Mylobot 僵尸网络: https://www.deepinstinct.com/2018/06/20/meet-mylobot-a-new-highly-sophisticated-never-seen-before-botnet-thats-out-in-the-wild/ https://threatpost.com/mylobot-botnet-emerges-with-rare-level-of-complexity/132967/
-

[ Pentest ] FireEye 对新型红队技巧 BYOL 的介绍:https://www.fireeye.com/blog/threat-research/2018/06/bring-your-own-land-novel-red-teaming-technique.html