腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] Inside Firefox's DOH engine: https://daniel.haxx.se/blog/2018/06/03/inside-firefoxs-doh-engine/
-

[ Detect ] Mimikatz DCsync 检测规则: https://github.com/Neo23x0/sigma/blob/master/rules/windows/builtin/win_dcsync.yml
-

[ Industry News ] 美国票务网站 Ticketfly 遭受黑客攻击勒索至今未恢复: https://threatpost.com/ticketfly-major-concert-venues-still-offline-after-hack/132436/
-
-

[ iOS ] 编写 Swift 代码来拦截 SSL Pinning 的 HTTPS 请求: https://medium.com/@kennethpoon/lets-write-swift-code-to-intercept-ssl-pinning-https-requests-12446303cc9d
-

[ Others ] propagate: PROPagate 代码注入技术示例: https://github.com/odzhan/propagate
-

[ Pentest ] 使用 Whois 命令进行文件传输的技巧: https://twitter.com/i/web/status/1001985728342102017
-

[ ReverseEngineering ] Ionic 3 应用逆向分析: https://www.citadel.sh/blog/reverse-engineering-ionic-applications
-

[ ReverseEngineering ] 逆向移动端游戏 My Tamagotchi Forever : http://natashenka.ca/reversing-my-tamagotchi-forever-evolution/
-

[ Tools ] routersploit - 嵌入式设备漏洞利用框架: https://github.com/threat9/routersploit
-

[ Tools ] maltrail - 恶意流量检测系统: https://github.com/stamparm/maltrail
-

[ Web Security ] 基于 Location 的 XSS Payloads Part 1: https://brutelogic.com.br/blog/location-based-payloads-part-i/
-

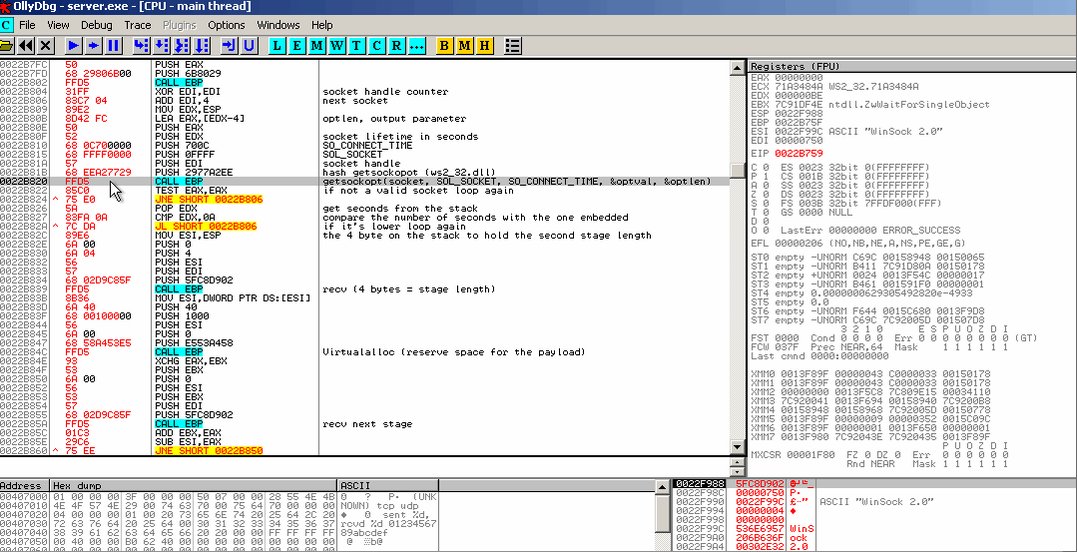
[ Windows ] Windows 套接字重用 ShellCode 编写: https://www.shelliscoming.com/2018/06/windows-reuse-shellcode-based-on.html
-

[ Windows ] PROPagate 代码注入技术介绍: https://medium.com/@0x6b64/background-abdddfdd59d2
-

[ Windows ] 使用 SCCM 和 Viewfinity 提权的技巧: https://ninja.style/post/privesc/
-

[ Windows ] Windows 漏洞利用开发:SEH 和 ROP 链利用: http://blog.k3170makan.com/2018/06/windows-exploit-development-exploiting.html
-

[ macOS ] macOS 驱动的量化的、可视化的攻击面地图,来自 Proteas 's weibo’:https://weibo.com/1290630720/GjkzOtK2V?type=comment#_rnd1528089034088