腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Backdoor ] 分析恶意 Powershell 后门 "PRB-Backdoor": https://sec0wn.blogspot.in/2018/05/prb-backdoor-fully-loaded-powershell.html
-

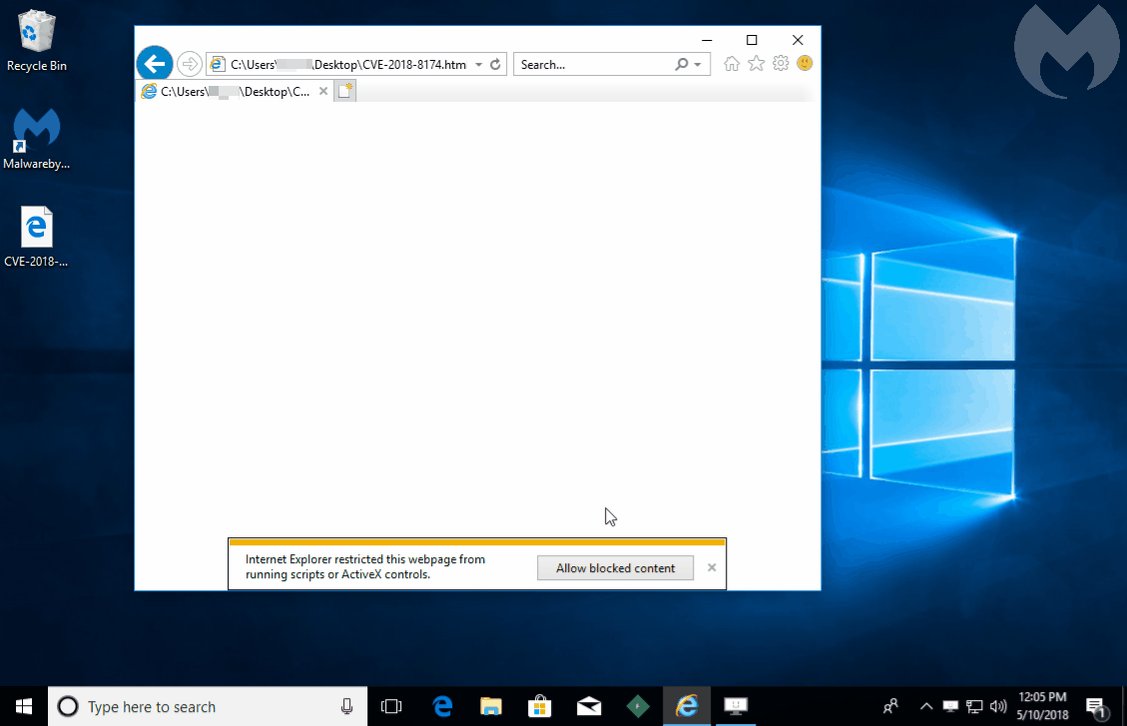
[ Browser ] Malwarebytes 对 IE 0day 漏洞(CVE-2018-8174)的分析: https://blog.malwarebytes.com/threat-analysis/2018/05/internet-explorer-zero-day-browser-attack/ ;
-

[ Fuzzing ] Adding AFL Bloom Filter to Domato for Fun: https://www.sigpwn.io/blog/2018/5/13/adding-afl-bloom-filter-to-domato-for-fun
-

[ macOS ] Pwning in the Sandbox OSX Macro Exploitation : https://www.slideshare.net/DannyChrastil/pwning-in-the-sandbox-osx-macro-exploitation
-

[ Malware ] Ubuntu Snap 商店中发现携带恶意挖矿后门的游戏 - 2048buntu: https://www.linuxuprising.com/2018/05/malware-found-in-ubuntu-snap-store.html
-

[ Protocol ] 编写 TCP / IP 协议栈 Part 1:以太网与ARP: http://www.saminiir.com/lets-code-tcp-ip-stack-1-ethernet-arp/
-

[ Tools ] build-your-own-x - Build your own 系列,各种环境的构建技术集合: https://github.com/danistefanovic/build-your-own-x
-

[ Tools ] ARM64JSON - JSON 格式的 ARM64 指令编码: https://github.com/kov4l3nko/ARM64JSON
-

[ Vulnerability ] 使用 CVE-2018-8897 POP SS 漏洞在 Ring 0 层执行任意代码: https://blog.can.ac/2018/05/11/arbitrary-code-execution-at-ring-0-using-cve-2018-8897/
-

[ Windows ] Microsoft Windows 2003 SP2 - 'RRAS' SMB 远程代码执行漏洞(CVE-2017-11885)利用: https://www.exploit-db.com/exploits/44616/
-

[ Windows ] Windows X64 上的栈溢出漏洞利用方式: https://nytrosecurity.com/2018/01/24/stack-based-buffer-overflows-on-x64-windows/
-

[ Windows ] LOLBAS - 使用 Windows 本地自带的可执行文件进行攻击的使用维基: https://github.com/api0cradle/LOLBAS
-

[ WirelessSecurity ] 部分 IoT 设备通过手机 APP 特定编码的 WiFi 广播包获取 WiFi 密码,攻击者也可以借此抓取密码,上海交大发了一篇关于该攻击方式的论文: https://loccs.sjtu.edu.cn/~romangol/publications/wisec18.pdf
-
-

[ Network ] CIA Hive Beacon Infrastructure复现1——使用Apache mod_rewrite实现http流量分发: https://3gstudent.github.io/3gstudent.github.io/CIA-Hive-Beacon-Infrastructure%E5%A4%8D%E7%8E%B01-%E4%BD%BF%E7%94%A8Apache-mod_rewrite%E5%AE%9E%E7%8E%B0http%E6%B5%81%E9%87%8F%E5%88%86%E5%8F%91/ Part 2: https://3gstudent.github.io/3gstudent.github.io/CIA-Hive-Beacon-Infrastructure%E5%A4%8D%E7%8E%B02-%E4%BD%BF%E7%94%A8Apache-mod_rewrite%E5%AE%9E%E7%8E%B0https%E6%B5%81%E9%87%8F%E5%88%86%E5%8F%91/
-

[ Processor ] Secure Boot and Remote Attestation in the Sanctum Processor: https://eprint.iacr.org/2018/427.pdf
-