腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] 分析基于行为模式的 Andriod 恶意检测: https://arxiv.org/pdf/1803.03448.pdf
-

[ Browser ] 以 Firefox 做通信通道来绕过防火墙限制的探索: https://medium.com/code-fighters/firefox-tunnel-to-bypass-any-firewall-bc6f8b432980
-

[ Compiler ] C 编译器生成只包含可打印字符的可执行文件(Paper) : http://www.cs.cmu.edu/~tom7/abc/paper.pdf
-

[ Firmware ] 针对爱国者(Aigo SK8671 )加密移动硬盘的研究,Part 1: https://syscall.eu/blog/2018/03/12/aigo_part1/ Part 2: https://syscall.eu/blog/2018/03/12/aigo_part2/
-

[ Firmware ] vim-clutch - 为提升 Vim 编码速度而生的 USB 电子脚踏板改造之旅: https://github.com/alevchuk/vim-clutch
-

[ Fuzzing ] CollAFL - Path Sensitive Fuzzing: https://csdl.computer.org/csdl/proceedings/sp/2018/4353/00/435301a660.pdf
-

[ Hardware ] 打造 GSM 基站: https://n0where.net/build-gsm-base-station
-

[ iOS ] iOS 静态分析与侦察: https://secdevops.ai/ios-static-analysis-and-recon-c611eaa6d108
-

[ IoTDevice ] 恢复一个变砖了的 MP Mini Delta 3D 打印机: http://arkorobotics.com/blog/?p=161
-

[ IoTDevice ] 卡巴斯基对韩华(Hanwha)智能摄像头的安全研究,发现了 10 多个严重漏洞: https://securelist.com/somebodys-watching-when-cameras-are-more-than-just-smart/84309/
-

[ Malware ] Proofpoint 安全研究员最近发现了一个新的 RAT 木马 FlawedAmmyy : http://www.cyberdefensemagazine.com/new-remote-access-trojan-rat-discovered/
-
-

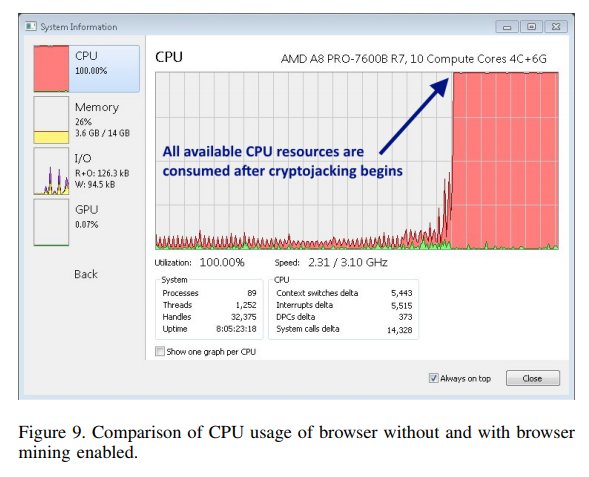
[ MalwareAnalysis ] 作者针对 Mac App Store 上一款 Calendar 2 应用的分析,此 APP 会偷偷将电脑用于挖矿: https://objective-see.com/blog/blog_0x2B.html
-

[ Others ] 使用 GDB 进行进程注入: https://magisterquis.github.io/2018/03/11/process-injection-with-gdb.html
-

[ SecurityReport ] McAfee 发布 2018 年 3 月威胁报告: https://www.mcafee.com/us/resources/reports/rp-quarterly-threats-mar-2018.pdf
-

[ Tools ] amass - Go 语言编写的子域名收集工具: https://github.com/caffix/amass
-

[ Tools ] uxss-db - UXSS 漏洞搜集仓库: https://github.com/Metnew/uxss-db
-

[ Tools ] tactical-exploitation - 战术型渗透测试工具包: https://github.com/0xdea/tactical-exploitation
-

[ Tools ] assessment-mindset - 网络安全评估思维导图: https://github.com/dsopas/assessment-mindset
-

[ Tools ] DockerAttack - 渗透测试用的 Docker 镜像: https://github.com/ZephrFish/DockerAttack
-

[ Tools ] NCC Group 发布 BLEBoy 用于学习 BLE 安全的工具: https://github.com/nccgroup/BLEBoy
-

[ Tools ] getaltname - 从 SSL 证书中提取域名的工具: https://github.com/franccesco/getaltname
-

[ Tools ] RAT-via-Telegram - 利用 Telegram 进行 C&C 通信的 Windows 远程控制工具: https://github.com/Dviros/RAT-via-Telegram
-

[ Tools ] forkless - 为 iOS 编写的第三方 fork 库: https://github.com/trufae/forkless/
-

[ Tools ] OWASP iGoat - 用于学习 iOS App 渗透测试和安全性的工具: https://github.com/OWASP/igoat
-

[ Tools ] PCILeech 内存进程文件系统的介绍: http://blog.frizk.net/2018/03/memory-process-file-system.html
-

[ Vulnerability ] Cisco Prime Collaboration Provisioning 硬编码密码漏洞披露(CVE-2018-0141): https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180307-cpcp
-

[ Windows ] 通过伪装图标的 JS 快捷方式调用 UNC 路径窃取用户 NetNTLM Hash: https://isc.sans.edu/forums/diary/Payload+delivery+via+SMB/23433/
-

[ Crypto ] 如何通过 DNS rebinding 的方法盗取你的以太坊:https://ret2got.wordpress.com/2018/01/19/how-your-ethereum-can-be-stolen-using-dns-rebinding/
-
-
-
-

[ Others ] 通过数据采集分析对进程注入进行检测: https://posts.specterops.io/defenders-think-in-graphs-too-part-1-572524c71e91
-